Zoho ManageEngine Arbitrary File Upload Vulnerability
Overview:
ManageEngine ServiceDesk is an IT help desk platform that provides functionality to manage various aspects of an IT environment such as changes, incidents and assets and also incorporates a standard ITIL framework. ManageEngine SupportCenter Plus is a web-based customer support software that lets organizations effectively manage customer tickets, their account & contact information and the service contracts. The code/features between these two applications is extensively shared.
An arbitrary file upload vulnerability has been reported in Zoho ManageEngine ServiceDesk Plus, ServiceDesk Plus MSP, and SupportCenter Plus. The vulnerability is due to an unspecified flaw related to the /RestAPI URLs in a servlet, and ImportTechnicians in the Struts configuration.
A remote attacker could exploit this vulnerability by sending crafted requests to the target server. Successful exploitation could allow the attacker to execute arbitrary code with privileges of SYSTEM.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2021-44077.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.7 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.7 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
ManageEngine ServiceDesk/SupportCenter include the features for configuring technicians information. The IT help desk team comprises the help desk team manager, help desk agent, and technicians who will be handling the requests posted / raised by various requesters from different accounts. A user can add, edit, or remove the technicians in the application and also provide them with various access privileges that suit their role and need. A user can also view the list of technicians in a particular account and/or site by selecting the account from the Accounts combo box and site from Technicians for combo box. The feature relevant to understanding this vulnerability is importing technicians information from a comma-separated (CSV) file into the application. Note that this feature is a legacy feature that is no longer available in both the unpatched (at least in the versions 11012 and 11012) and patched version of the SupportCenter Plus application.
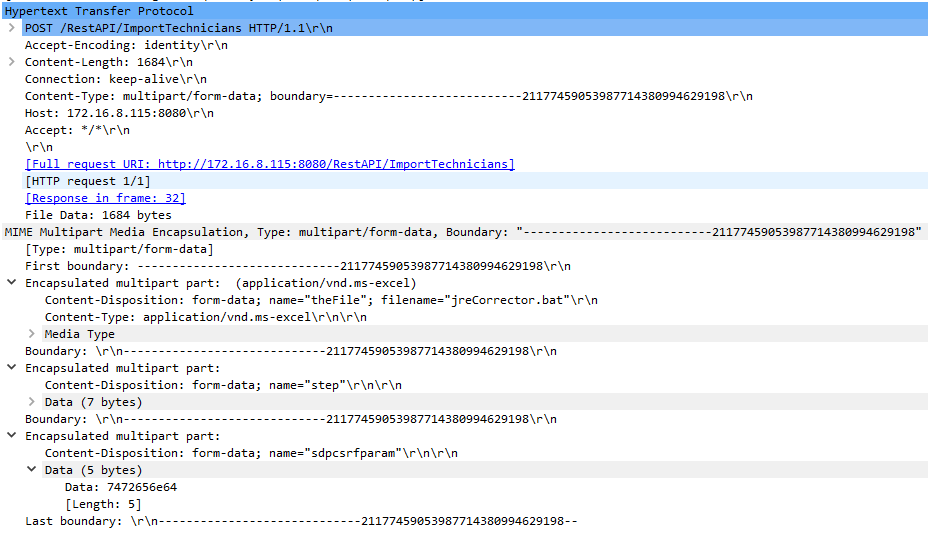
This feature is accessible via Apache Struts action ImportTechnicians defined in struts-config.xml. This feature is mapped to Request-URL “/RestAPI/ ImportTechnicians”. An unrestricted arbitrary file upload vulnerability exists in ManageEngine ServiceDesk Plus, ServiceDesk Plus MSP and SupportCenter Plus products. The vulnerability is due to improper validation of the filename parameter.
The user sends a POST request to /RestAPI/ImportTechnicians and the value of the Content-Type header is string multipart/form-data, the execute method in the class com.adventnet.servicedesk.setup.action.ImportTechniciansAction is eventually called. The execute method uses the value of the filename attribute of the Content-Disposition header in the body of the request to write the contents of the file in the “
The uploaded file is not checked for the expected file extension which is “.csv”. Note that directory traversal is not possible as the Java classes org.apache.struts.upload.CommonsMultipartRequestHandler and org.apache.struts.upload.CommonsMultipartRequestHandler.CommonsFormFile from struts.core-1.3.11.jar are used by the application to remove from the filename parameter all characters before the last ‘/’ or ‘\’ character, before the vulnerable code in com.adventnet.servicedesk.setup.action.ImportTechniciansAction is reached.
A remote, unauthenticated attacker can exploit this vulnerability by sending a crafted request to ImportTechnicians action to write or overwrite arbitrary files in “
Triggering the Problem:
• The target must be running a vulnerable version of the software.
• The attacker must have network connectivity to the target server.
Triggering Conditions:
The attacker sends a request to the vulnerable servlet on the target server. The vulnerability is triggered when the server processes the request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP, over port 8080/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2302 ManageEngine Products ImportTechnicians Arbitrary File Creation
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Restricting access to the affected communication port to trusted hosts only.
• Upgrading to a non-vulnerable version of the product when available.
• Detecting and blocking malicious traffic using the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory 1
Vendor Advisory – ServiceDesk Plus MSP
Vendor Advisory 2
Vendor Advisory – ServiceDesk Plus
Vendor Advisory 3