Zimbra Collaboration Suite TAR Remote Code Execution
Zimbra Collaboration Suite (ZCS) is a collection of tools which include an email server, a chat server, a file sharing server, a shared calendar, and an email client. The application’s web mail client and admin console can be accessed through HTTP. Amavisd runs as a daemon process and listens on TCP port 10024 for incoming SMTP connections. GNU cpio is a tool for creating and extracting archives, or copying files from one place to another. It handles many cpio formats and reading and writing TAR files.
Zimbra TAR Remote Code Execution | CVE-2022-41352
An issue was discovered in ZCS 8.8.15 and 9.0. An attacker can upload arbitrary files through amavisd via a cpio loophole (extraction to /opt/zimbra/jetty/webapps/zimbra/public) that can lead to incorrect access to any other user accounts. This vulnerability tracked as CVE-2022-41352 (CVSS score 9.8) is a remote code execution flaw that allows attackers to send an email with malicious archive attachment. This attachment bypasses antivirus checks and plants a web shell in the ZCS server.
The root cause of the vulnerability is using the ‘cpio’ file archiving utility to extract archives when Amavisd scans a file for viruses. The cpio component has a flaw that allows an attacker to create archives that can be extracted anywhere on a filesystem accessible to Zimbra.
When an email is sent to a Zimbra server, the Amavis security system will extract the archive to perform a virus scan of its contents. However, if it extracts a specially crafted .cpio, .tar, or .rpm archive, the contents could be extracted to the Zimbra webroot.
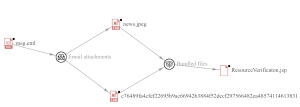
In the following exploit the attacker sends an email with subject line ‘News’ that contains malicious attachments news.jpg and news.jpeg
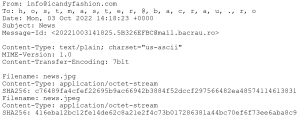
Both the attachments are specially crafted .tar files but are named .jpg and .jpeg
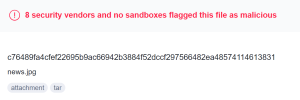
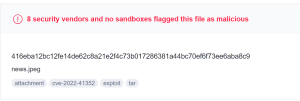
These contain a javascript ResourceVerificaton.jsp file that could deploy web shells to the Zimbra root, effectively giving an attacker shell access to the server.
SonicWall Capture Labs provides protection against this threat via following signatures:
- ASPY 374: Malformed-File tar.OT_1
- ASPY 379: Malformed-File tar.OT_2
- GAV CVE-2022-41352.A
- GAV CVE-2022-41352.A_1
Zimbra has patched this vulnerability.
IoCs
416eba12bc12fe14de62c8a21e2f4c73b017286381a44bc70ef6f73ee6aba8c9
094f2d7d11c612d470d6c8943585b860a42eac7fff974d0a41d5f9cf0906bbd7
c76489fa4cfef22695b9ac66942b3884f52dccf297566482ea48574114613831
b73f4f79e65bb804dae0962ebc5ba6657a4499847bacd4670b3e5ba14e2c7ef2





