WWBN AVideo Command Injection Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
AVideo is a powerful base platform for uploading, curating, organizing, indexing, and distributing audio and video content. The plugin design allows you to get exactly the solution that addresses your needs today, while ensuring that your Media Broadcast Network implementation can grow and expand with you as your needs evolve.
A command injection vulnerability has been reported in WWBN AVideo. The vulnerability is due to improper input validation when executing a command.
A remote, authenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successful exploitation could result in execution of arbitrary commands.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-30534.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.9 (CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.9 (AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is low.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.9 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
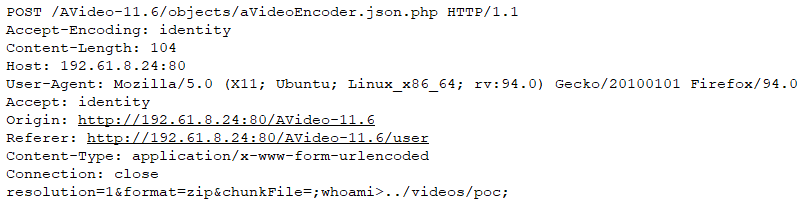
The management life cycle of media in AVideo consists of uploading media to temporary storage for encoding and then storing the media for distribution to other users. A user with upload privileges on an instance of AVideo can upload videos by providing a URL where the video can be accessed or uploading a video file for encoding. When a video is uploaded the functionality of AVideo/objects/aVideoEncoder.json.php is used to process the request and encode the video. The encoding step expects a POST request containing the chunkFile parameter that contains the provided file name as well as a ZIP file containing the video to be uploaded and encoded. If the chunkFile parameter is not empty the function decideMoveUploadedToVideos is called in AVideo/objects/functions.php with the value of the chunkFile parameter. The function decideMoveUploadedToVideos then calls the function unzipDirectory. The unzipDirectory function builds a command string to unzip the provided file for further processing.
However, during the building of the unzip command string the value of the chunkFile parameter is used directly without performing any sanitation. This allows an attacker to provide a request with a crafted chunkFile parameter that contains command injection characters to perform arbitrary operations on the target server. An example of a malicious request is shown below:
Triggering the Problem:
• The target system must have the vulnerable product installed and enabled.
• The attacker must have network connectivity to the affected ports.
• The attacker must be able to authenticate with the vulnerable server with upload permissions.
Triggering Conditions:
The attacker authenticates with the vulnerable AVideo server. Then the attacker sends a crafted HTTP request to the target server. The vulnerability is triggered when the target server processes the request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2142 WWBN AVideo chunkfile Command Injection
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Filtering traffic based on the signature above.
• Upgrading the product to a non-vulnerable version.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory