Windows Malware Family FlawedAmmy Disassembled
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample and activity in July for the “FlawedAmmy”, Windows RAT, Malware Family. SonicWall has covered malicious MS-Office files being used to distribute “FlawedAmmy” in the past by phishing campaigns. Phishing campaigns cover larger populations of victims, and are usually sent to the masses instead of personalized Spear-Phishing campaigns sent to individuals. Today, we will cover the actual disassembly of the Windows “FlawedAmmy” RAT malware that is executed after the VBA Macro code is executed.
Remote Access Trojans (RAT), sometimes called Creep-ware can allow an attacker to gain complete control over the system. An attacker can do almost anything that someone physically sitting at the computer can do, including using any 3rd party device connected to the machine.
Stage 1 – Static Information:
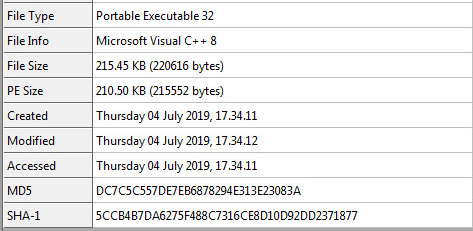
Packer & Entropy Information:
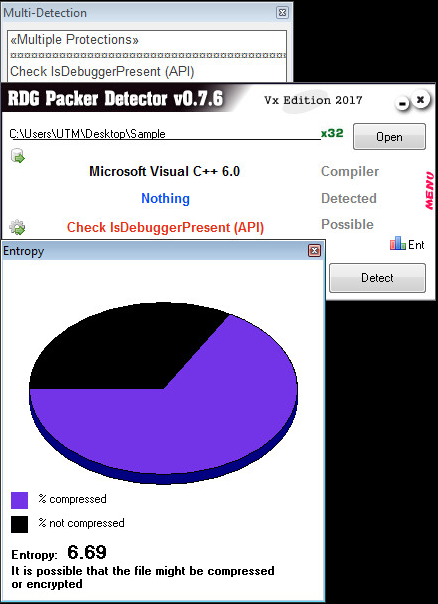
Retrieving & Unpacking The Sample:
Unpacking the sample can be completed by toggling a break point on VirtualAlloc. VirtualAlloc will be called multiple times creating three buffers. The first buffer that is used is hidden executable code. Which can be seen here:
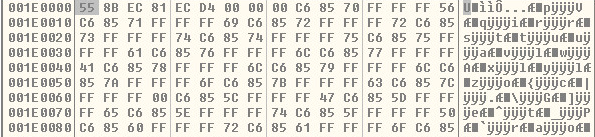
Translating this buffer into code will allow you to see the hidden code that is executed. Looking closer the sample uses the imports VirtualAlloc, GetProceAddress, VirtualProtect, LoadLibraryA, VirtualFree, and VirtualQuery:
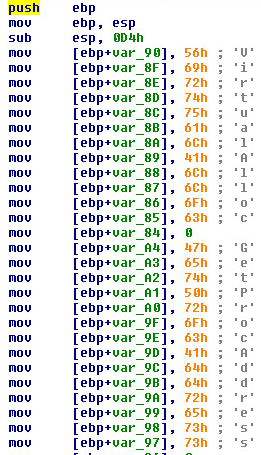
The second buffer is that of an encrypted PE File. We can see half of it starting to be decrypted here:
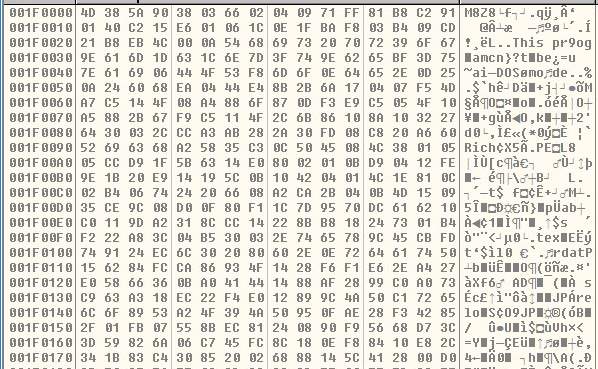
The third buffer will be the decrypted PE File. Once we see this buffer decrypted we can dump the new PE File to disk. This will be Stage 2:
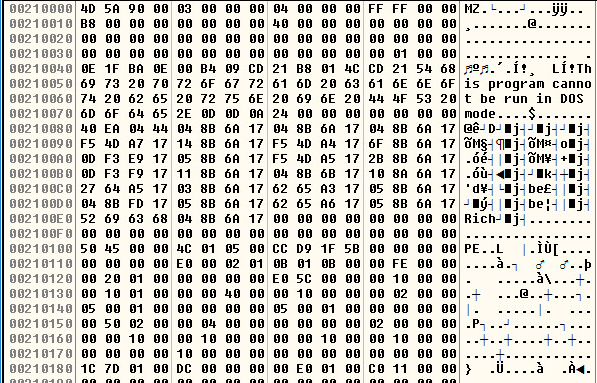
Xor Encryption Used:
Routine One:
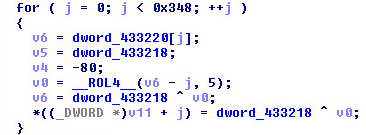
Routine Two:
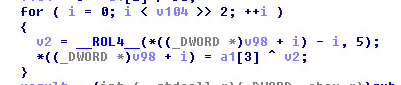
Stage 2 – Static Information:
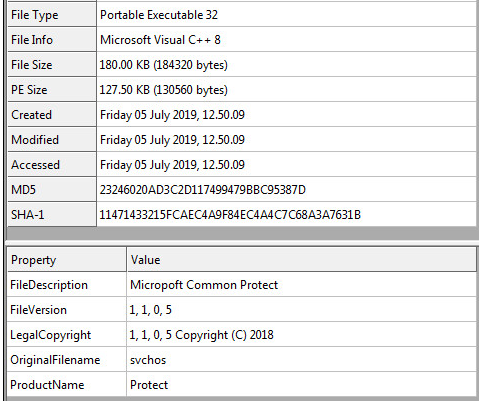
Packer & Entropy Information:
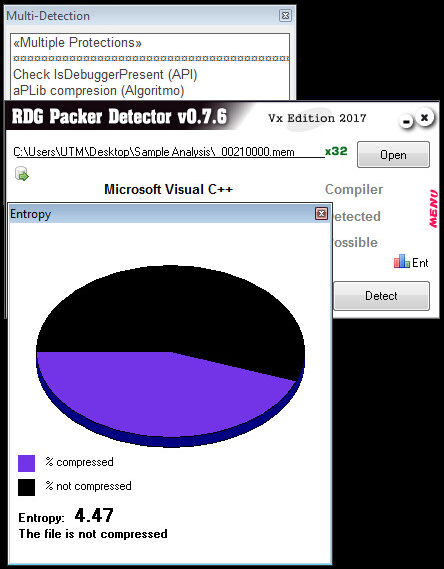
Static Network Indicators:
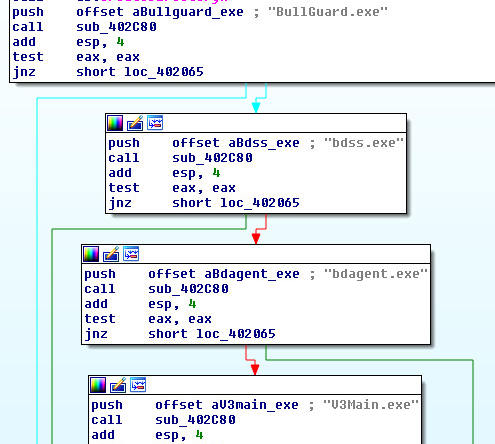
Anti-AntiVirus Techniques:
- BullGuard.exe – AntiVirus
- bdss.exe – BitDefender Core Component
- bdagent.exe – BitDefender Total Security Component
- V3Main.exe – AhnLab V3 Light
- V3SP.exe – AhnLab V3 Light
- PSUAMain.exe – Panda Internet Security
ProcMon Analysis:
During our testing, the sample actively loaded 88 modules (.dlls) while executing. The sample also opens 2,263 registry keys during operation. Starts two services called, “AMMYY” and “Foundation”. The location of files:
- C:\ProgramData\AMMYY\wmihost.exe
- C:\ProgramData\AMMYY\settings3.bin
- C:\ProgramData\Foundation\wmites.exe
- C:\ProgramData\Foundation\settings3.bin
- C:\ProgramData\Foundation1\wmites.exe
- C:\ProgramData\Foundation1\settings3.bin
- C:\ProgramData\Microsoft\wsus.exe
- C:\ProgramData\Microsoft\settings3.bin
- C:\ProgramData\Microsoft Help\wsus.exe
- C:\ProgramData\Microsoft Help\settings3.bin
- C:\ProgramData\Microsoft Help\wsus_41b480.tmp
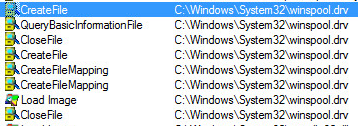
Loads one driver called winspool.drv.
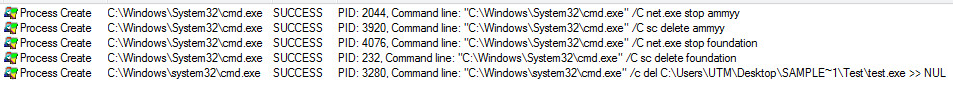
If the sample detects you are trying to debug the services and processes it has running. It will stop and delete them as seen in the picture below:
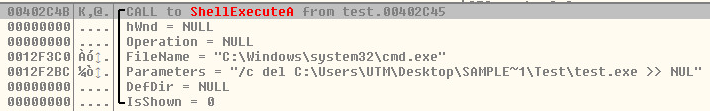
Deletes original file using ShellExecute:
Supported Systems:
- 5.1 or 5.2 (Windows XP x86 & x64) & (Windows Server 2003 & R2)
- 6.1 (Windows Server 2008 R2 & Windows 7)
- 6.2 (Windows Server 2012 & Windows 8)
- 6.3 (Windows Server 2012 R2 * Windows 8.1)
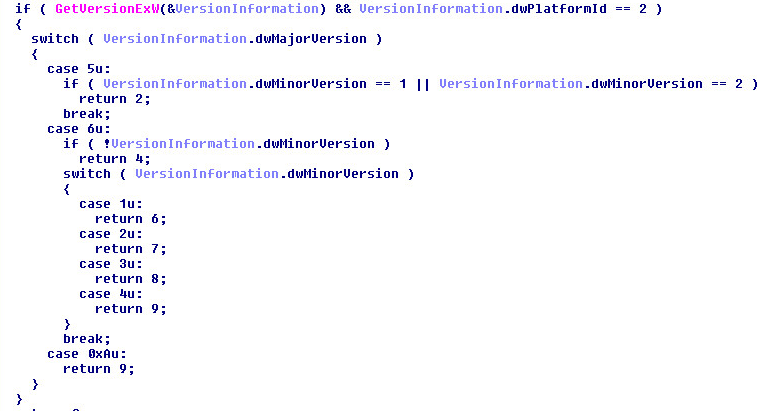
No-Support for Minor Version 6.4 and Windows 10.
Microsoft never came out with a Minor Version for 6.4. So, return “9” is an error.
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: FlawedAmmyy.RAT (Trojan)




