Watch out for this BlackLivesMatter spam email delivering malware
Black Lives Matter protests have spread across the United States and worldwide. The core of the protests have been activists taking to the streets but in this very online age while also amidst a pandemic, there have been a lot of inventive ways that people have shown their support online with viral tweets to hashtags and to signing online petitions. Unfortunately cybercriminals have also seized this opportunity to distribute emails disguised as supporting the movement using a malicious attachment of a document intended for the victim to “sign” to show their support.
Infection cycle:
This spam email comes with a malicious attachment that bears the following filename:
- e-vote_form_xxxx.doc
Upon opening of the malicious Word document file, the victim is presented with the image below:

Once the user follows the instructions to enable editing and enable content, a fake error will be displayed while the legitimate command prompt executable is spawned to continue its malicious actions.

![]()
It then does a DNS query to ppid dot indramayukab dot go dot id. And then simultaneously sends encrypted data to a remote server.
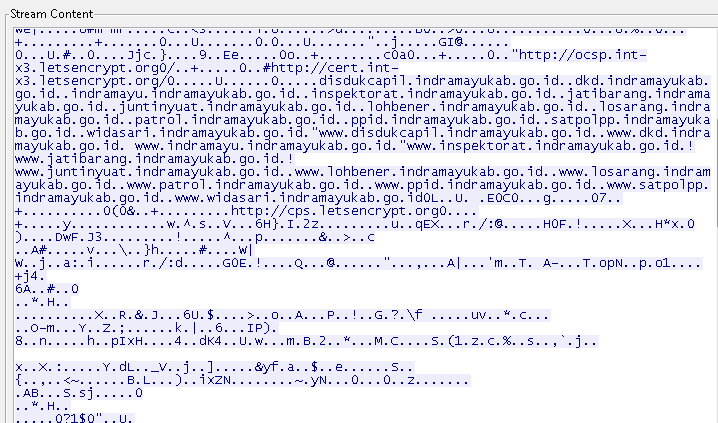
Sending encrypted data to remote server IP: 113.20.29.29
It also communicates with another server at inspeclabeling dot com.
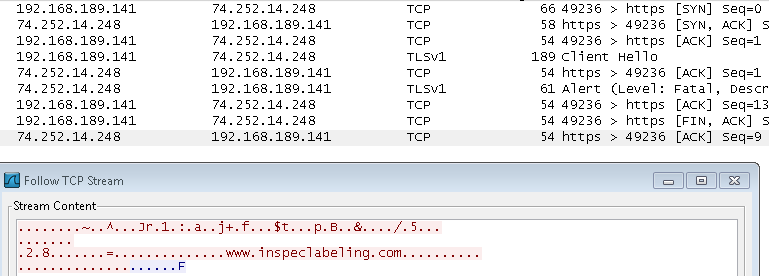
Connecting to 74.252.14.248, inspeclabeling.com
Both web addresses appear to be legitimate servers that could be well compromised.
Command prompt continues to run in the background even after closing the said word document, thus the malicious activity continues.
However, no further change in the system was made to ensure persistence therefore the infection does not continue after a system reboot.
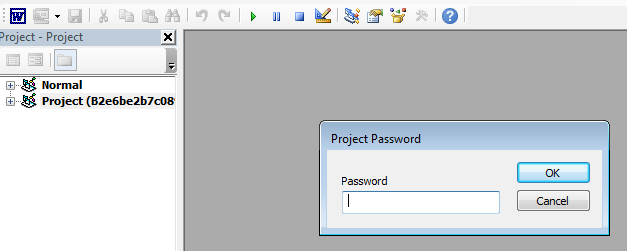
The macro content within the malicious document is protected with a password therefore we were not able to view it using Word.
As always, we urge our users to only use official and reputable websites as their source of information and news. Always be vigilant and cautious when installing software programs particularly if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Downloader.DOC.VBA_2 (Trojan)
- GAV: Trickbot.D_3 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




