vBulletin Remote command execution vulnerability
vBulletin is a proprietary Internet forum software. It is written in PHP and uses a MySQL database server. Once installed and configured, the forum is accessible via Hypertext Transfer Protocol (HTTP).
vBulletin 5.x through 5.5.4 allows remote command execution via the widgetConfig[code] parameter in an ajax/render/widget_php routestring request ( CVE-2019-16759 )
A remote command execution vulnerability exists in vBulletin . An attacker can exploit this vulnerability by specially crafted httpPOST request. For exploiting authentication is not required therefore it is a pre-auth remote command injection. The commands would be executed with the same privileges as the vBulletin service. This could result in hackers taking over vulnerable web forums.
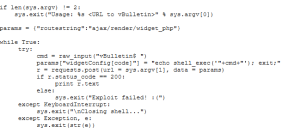
Examining the PoC code we understand that malicious parameters commands could be passed to widgetConfig[code] which will then get posted via the routestring POST request.
The POST request looks like this
![]()
Followed by the exploit code.

Some examples of exploits in the wild

after decoding :
![]()
another example:
![]()
after decoding :
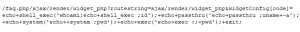
In both examples attacker tries to execute web shell commands.
SonicWall Capture Labs Threat Research team provides protection against this threat with the following signatures:
- IPS 14453 vBulletin widgetConfig Remote Command Execution 1
- IPS 3185 Web Application Remote Code Execution 14
IoCs:
- 182.161.18.135
- 191.37.220.126
- 14.231.65.23
- 129.0.76.131
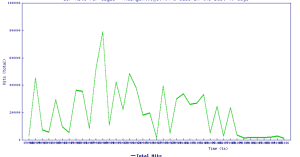
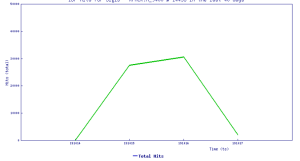
Threat Graph: