vBulletin Deserialization RCE Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
vBulletin is written in PHP and uses MySQL as its database management system. It is designed to provide a robust platform for online communities to discuss and share ideas, information, and content. vBulletin is known for its ease of use, flexibility, and scalability, making it a popular choice for both small and large forums.
vBulletin offers several key features that make it a popular choice for forum management. Its user-friendly interface is designed with usability in mind, ensuring that both administrators and users can easily navigate and manage the forum. Powerful administration tools are provided through a comprehensive control panel, which allows administrators to manage and customize various aspects of the forum, including user permissions, content moderation, and appearance. The platform’s extensibility means that it supports a wide range of plugins and add-ons, enabling administrators to tailor their forum’s functionality to meet specific needs. Moreover, vBulletin’s responsive design ensures that the forum displays well and operates smoothly on various devices, such as smartphones and tablets.
A remote code execution vulnerability has been identified in vBulletin due to inadequate validation of the ‘searchprefs’ field, leading to arbitrary deserialization. Exploiting the unserialize() function can be achieved by using PHPGGC to generate a payload or discovering a new gadget chain within the code.
A remote, authenticated attacker could exploit these vulnerabilities by sending crafted requests to the target server. Successful exploitation could result in arbitrary remote code execution under the security context of system.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-25135.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:L/UI:N/S:C/C:L/I:L/A:L), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is low.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.8 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept code.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
Understanding the deserialization remote code execution (RCE) vulnerability in vBulletin necessitates familiarity with several key technologies and concepts. One such concept is deserialization of untrusted data, which refers to converting a serialized data stream back into an object or data structure without properly validating or sanitizing the input. Serialization is the process of converting complex data structures, such as objects, into a format that can be easily stored or transmitted, while deserialization is the reverse process. When an application deserializes untrusted data without proper validation, it can lead to various security vulnerabilities, including remote code execution, denial of service, or unauthorized access to sensitive information.
Another critical concept is the use of gadget chains, typically comprising one or more interconnected objects with specific properties or methods that can be abused during the deserialization process. An attacker crafts a malicious serialized data stream containing references to these objects, along with manipulated data that exploits their properties or methods. When the application deserializes this malicious data, the gadget chain is executed, resulting in unintended behavior or code execution. Furthermore, understanding Object-Relational Mapping (ORM), scalar fields, autoloading, and the serialize() and unserialize() functions is vital for comprehending the intricacies of the vBulletin deserialization RCE vulnerability.
vBulletin’s ORM offers an abstraction layer between the application logic and the database, while scalar fields represent columns in database tables storing single-value data types. Autoloading in vBulletin is a feature that automatically loads required class files as needed, streamlining class file inclusion in the code and promoting a more organized and efficient structure for the application. Lastly, vBulletin utilizes PHP’s built-in serialize() and unserialize() functions to handle serialization and deserialization processes within the application. These functions play a critical role in converting complex data structures, such as objects or arrays, into a storable or transmittable format (serialization) and reversing this process to recreate the original data structures (deserialization).
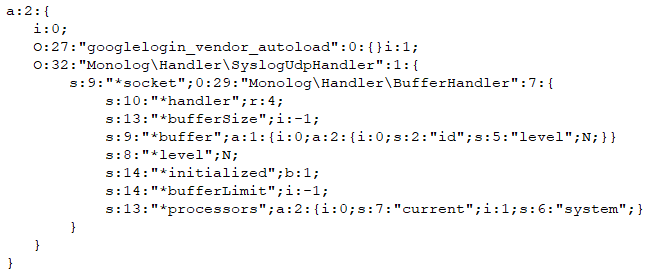
This serialized payload represents a gadget chain using objects from two different libraries: GoogleLogin extension for MediaWiki and Monolog. The payload comprises an array with two objects:
When this payload is deserialized using PHP’s unserialize() function, the objects will be recreated, and their destructors will be called upon script termination or when the objects are no longer needed.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
• The attacker must send malicious serialized payloads containing gadget chains to the application.
• The attacker must use the unserialize() function to deserialize the payload.
Triggering Conditions:
The attacker sends a POST request to the target system. A deserialization vulnerability, such as CWE-502, may arise in an application under certain circumstances. One contributing factor is the application accepting serialized data from untrusted sources without implementing proper validation or sanitization measures. Additionally, the application employs the unserialize() function to deserialize this untrusted data, which can inadvertently instantiate objects containing malicious gadget chains. These gadget chains can be present in the application’s code or in third-party libraries used by the application, making them exploitable during the deserialization process. Furthermore, the autoloader mechanism plays a role in this vulnerability by loading classes required for deserialization. This can lead to unintended consequences or even the execution of malicious code when an attacker exploits the autoloader during a deserialization attack.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 15584 vBulletin Insecure Deserialization
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Updating to a non-vulnerable version of the product.
• Filtering attack traffic using the signature above.
• Apply proper input validation and sanitization to any deserialized data.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory