Turla Variant GoldenSky
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample and activity for a Turla variant called GoldenSky. Turla has many names since 2014, aka: Turla, Snake, Venomous Bear, VENOMOUS Bear, Group 88, Waterbug, WRAITH, Turla Team, Uroburos, Pfinet, TAG_0530, KRYPTON, Hippo Team, Pacifier APT, Popeye, SIG23, Iron Hunter, MAKERSMARK.
Turla is known for targeting government organizations, military and diplomatic targets using a complex collection of malware and interesting command-and-control (C2) implementations.
Common tools include remote-access trojans (RATs), [Kazuar and Carbon] and HyperStack remote procedure call (RPC)-based backdoors. These tools often include several layers of obfuscation and defense-evasion techniques.
The RATs transmit the command-execution results and exfiltrate data from the victim’s network, while the RPC-based backdoors including HyperStack use the RPC protocol to perform lateral movement, issue and receive commands on other machines within the local network.
The upgrades seen in the campaign largely revolved around creating built-in redundancies for remote communication.
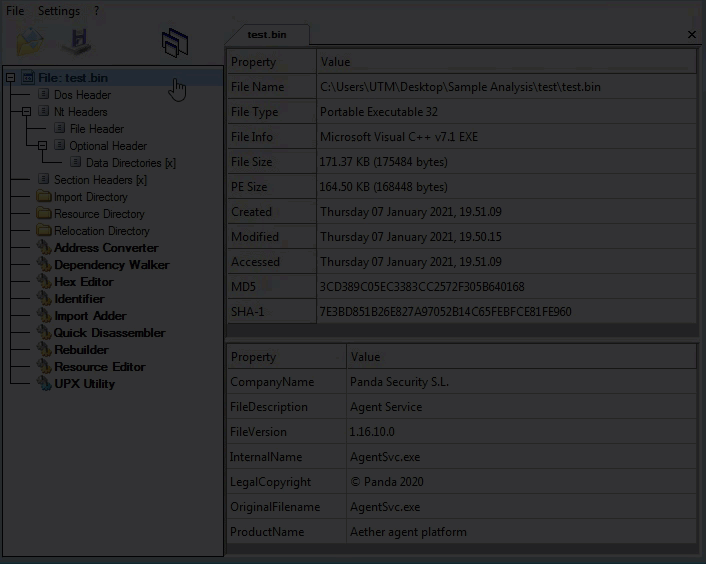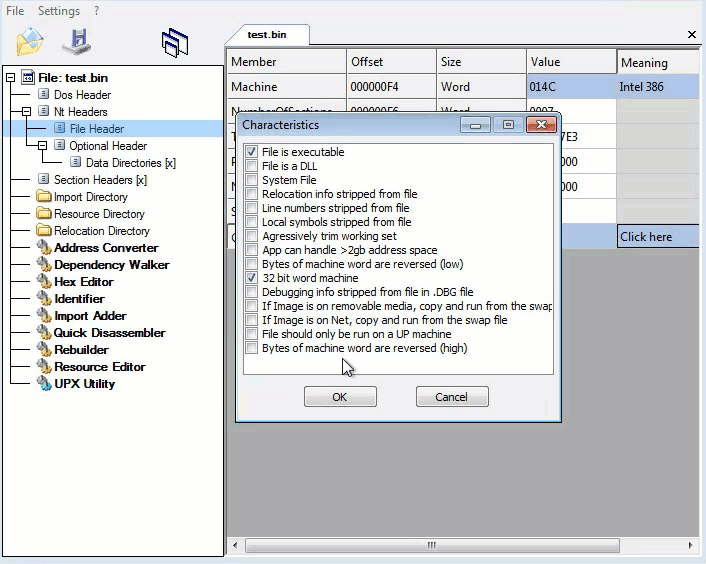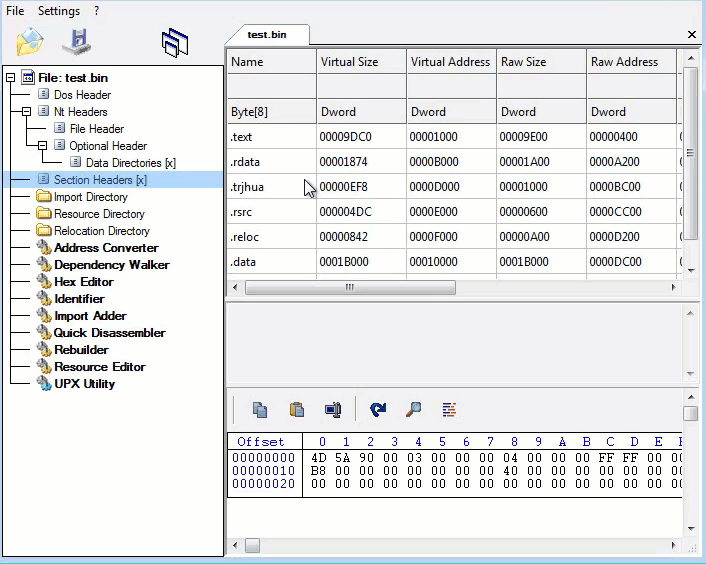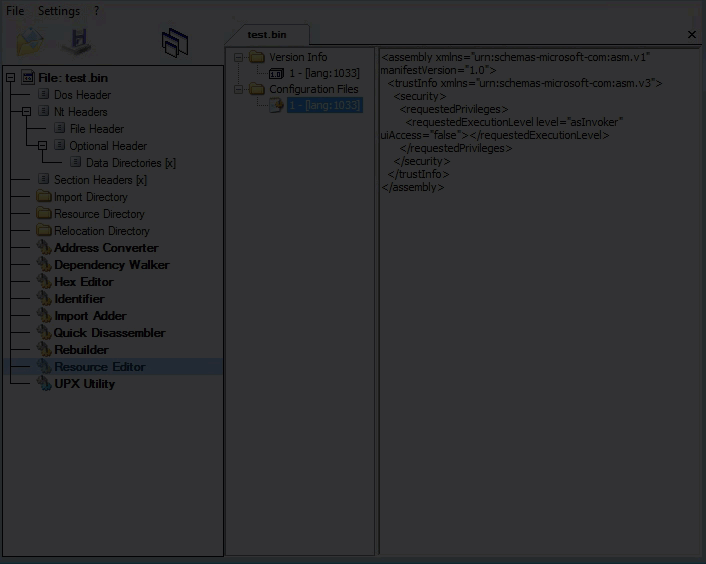
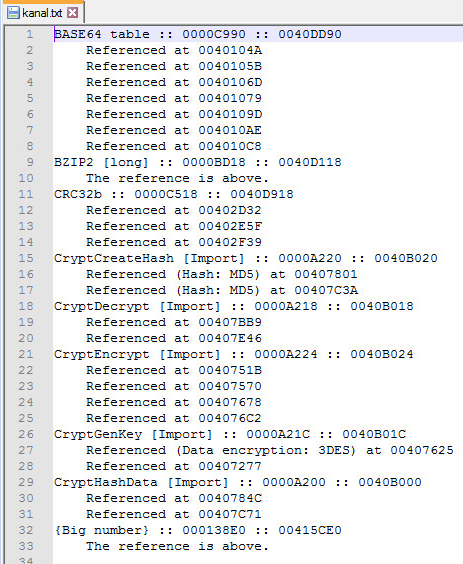
Sample Static Information:
Encryption Signatures:
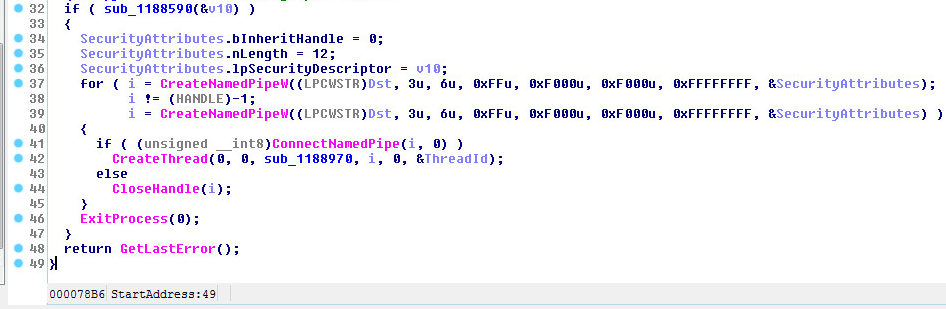
Dynamic Information:
Inter-process communication (IPC):
The Pipe OpenMode:
PIPE_ACCESS_DUPLEX, The pipe is Bi-Directional; Both server and client processes can read from and write to the pipe.
The Pipe nMaxInstances are set to:
PIPE_UNLIMITED_INSTANCES(255), which is misleading, you can only have a total of 256 pipe instances.
The number of bytes for the Pipe (Input & Output) buffer are set for 0xF000 or 61,440 Bytes.
Reading and Writing to the Pipe:
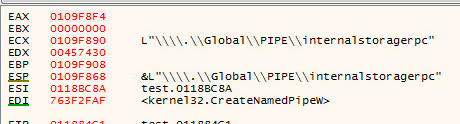
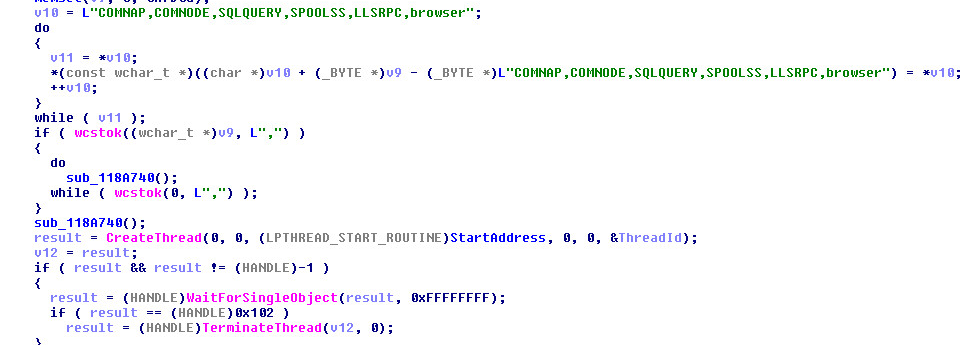
Pipe Name:
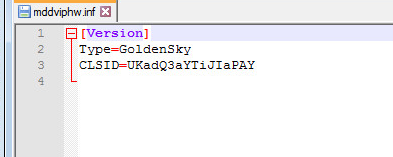
INI File:
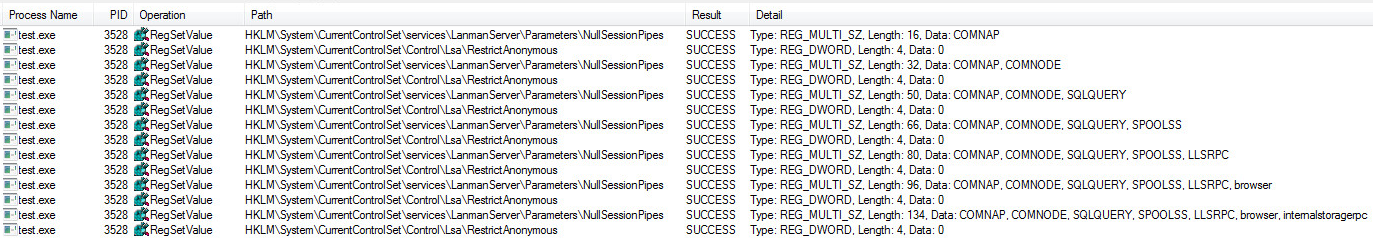
Pipe Registry Key Settings:
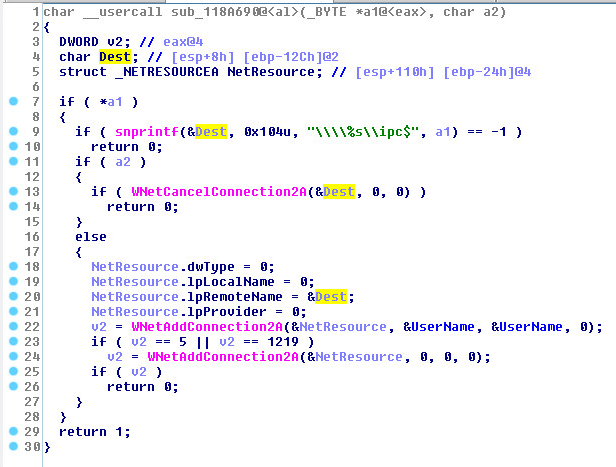
NET Resources:
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Goldensky.D (Trojan)
Appendix:
Sample SHA256 Hash: 48dced47372853658202b286920bb4fd0ab16de7c5d5b736eac84eee023d569f