TrickBot Banking Variant Actively Spreading
Overview:
SonicWall Capture Labs Threat Research Team recently found a new variant sample and activity in June for the TrickBot malware family. This family has been well known for many years, mainly focused on stealing victim’s online banking information. This variant has been written by developers with slick development skills wrapping its core functionality with a “Squirrel Shooting Game” code base to throw off initial analysis. It is often called a banker, however its modular structure allows it to freely add new functionalities without modifying the core bot. This particular variant uses an RSA encryption schema to protect certain areas of its core code along with custom xor encrypted strings. TrickBot also has the ability to continually update itself by downloading new modules from the C&C server and change its configuration on the fly. A picture of the game wrapped malware:
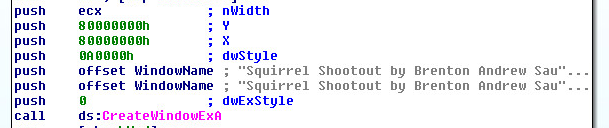
Game Wrapper: Squirrel Shootout by Brenton Andrew Saunders.
The game wrapped malware only serves as an analysis trick to throw off Security Researchers and others that want to try and analyze its code base. The game code doesn’t ever execute.
Sample Static Information:
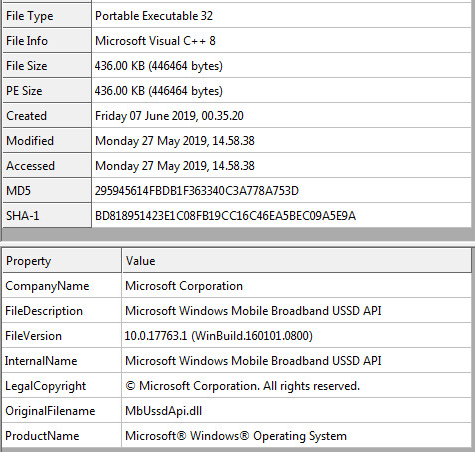 The sample tries to mask itself as an internal component to the Windows Operating System listed as:
The sample tries to mask itself as an internal component to the Windows Operating System listed as:“Microsoft Windows Mobile Broadband USSD API” naming itself as “MbUssdApi.dll”
however, it executes as an .exe not injected as a .dll.
Packer & Compression Information:
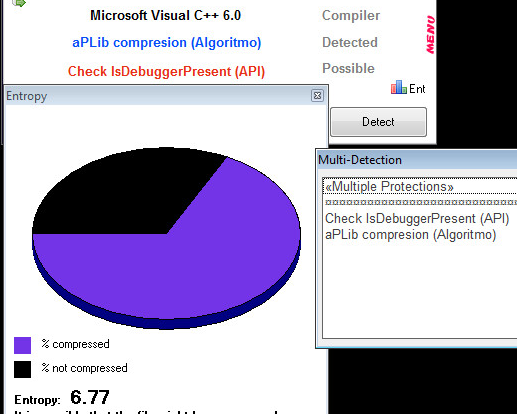
C&C & Network Activity:
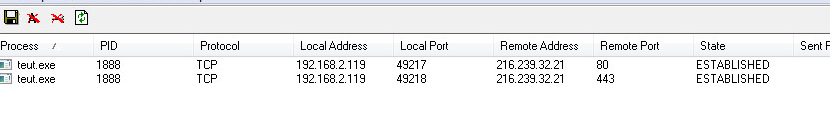
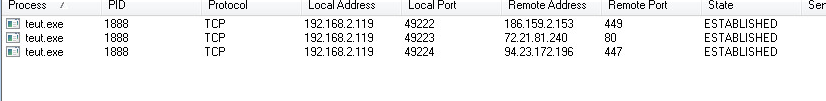 The sample makes connections to multiple IP Addresses:
The sample makes connections to multiple IP Addresses:- 216.239.32.21
- 186.159.2.153
- 72.21.81.240
- 94.23.172.196
The longer the sample is able to run the more IP Addresses are generated and connected too. At first initial analysis we’ve seen the sample connect to over ten IPs. As you close each connection the sample seems to auto rotate the IP Addresses that are established.
Process Creation:
Right Click the picture below to open the image in a new tab. This will allow you to see the commands easier.

Command Line Execution List:
- cmd /c powershell Set-MpPreference -DisableRealtimeMonitoring $true
- cmd /c sc stop WinDefend
- cmd /c sc delete WinDefend
- AppData\Roaming\chromedata\teut.exe
The commands that are executed will disable RealtimeMonitoring, stop the service “WinDefend”, and try to delete the service after its terminated. Once finished it will execute a new process called “teut.exe” which is just the original .exe above just in a new location.
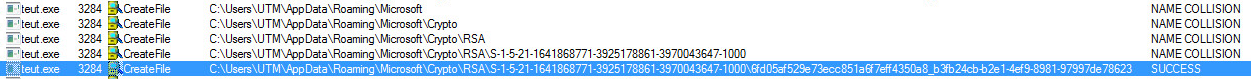
RSA Key Material:
The key Information can be found in the following directory:
AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1641868771-3925178861-3970043647-1000\
Your directory may have other random numbers after /RSA/
Right Click the picture below to open the image in a new tab.
Debugging System:
The sample was tested and debugged on (x86) – 32 Bit, Windows 7 Professional.
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: TrickBot.A_4 (Trojan )




