TinyPOS a new multi-component POS family actively spreading in the wild.
The SonicWall Capture Labs Threat Research Team observed reports of a new multi-component variant POS family named Tinypos Detected as GAV: Tinypos.A actively spreading in the wild.
Contents of TinyPOS Malware
Infection Cycle:
Tinypos is a multi-component malware family that has been very active in the wild. Multi-component malware is easy to detect because individual components are themselves malicious.
TinyPOS contains following components:
Loaders: this is a downloader component. The core functionality of a loader is to establish communication with C&C servers.
Mappers: Mappers are only responsible for steal types of information from the infected machine.
Scrapers: this component responsible for scraping memory to retrieve Track 1 and Track 2 credit card data during its scan.
Cleaners: wiping malware evidence such as running processes, registry keys and files once the operation is finished.
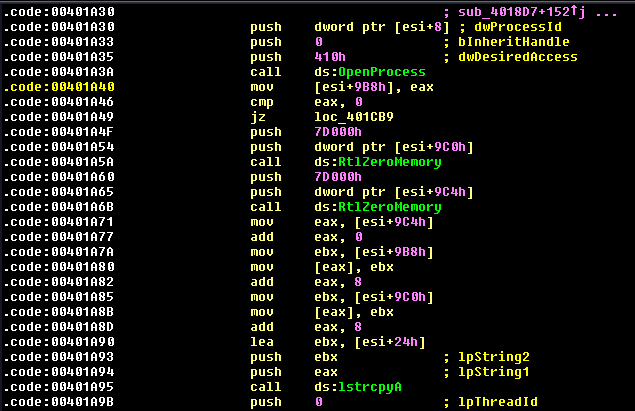
Once the computer is compromised, the malware creates a new process to maintain persistence and then launches a component to monitor for sensitive payment card data.
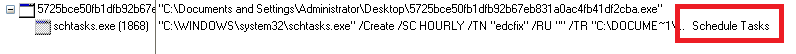
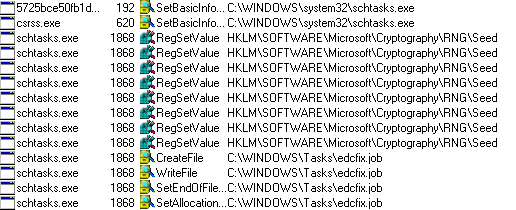
The malware tries to Enumerate POS process by uses API functions calls such as following APIs:
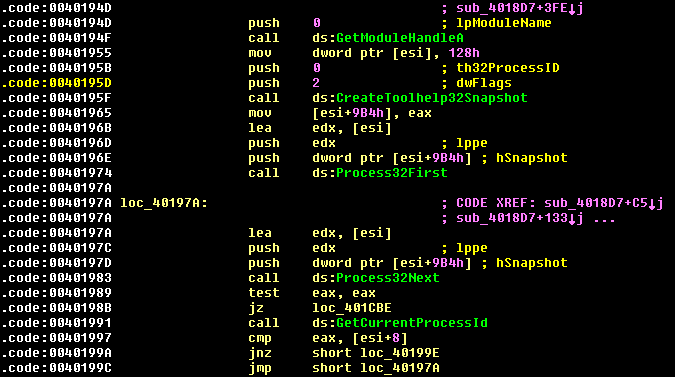
TinyPOS retrieves a list of running processes; the malware is responsible for scraping the memory of current processes on the infected machine for credit card information periodically.
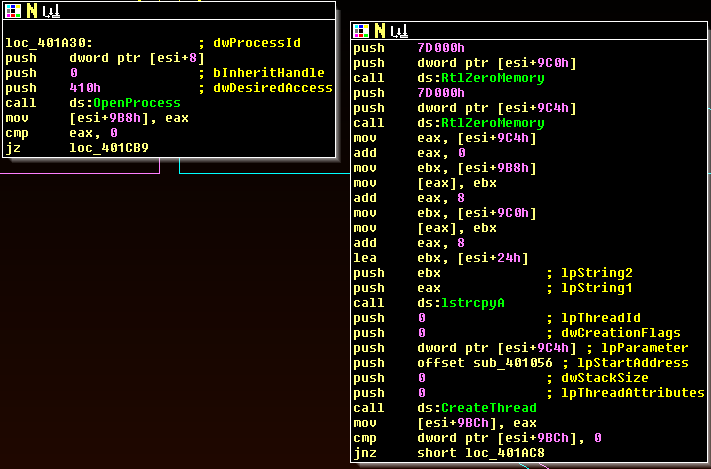
TinyPOS has an exclusion list that functions to ignore certain system processes; it gathers track data by scanning the memory of all running processes except for the following List:
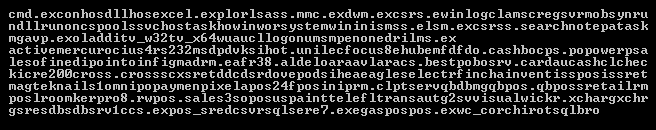
Once it locates payment card data, TinyPOS makes one HTTP request to determine the infected system’s external IP address.
Once the public IP is acquired, TinyPOS tries to verify Credit Cards numbers and then sends track 1 and track 2 credit card data in encrypted format.
TinyPOS tries to Enumerate Credit Card data from POS Software using the Luhn algorithm and then encrypts and sent to one of the given C&C Servers.
Here is an example of Track data:

Command and Control (C&C) Traffic
TinyPOS performs C&C communication over various ports. Requests are made on a regular basis to statically defined IPs such as following:
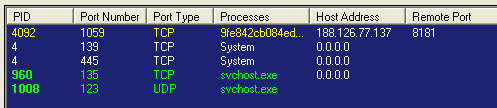
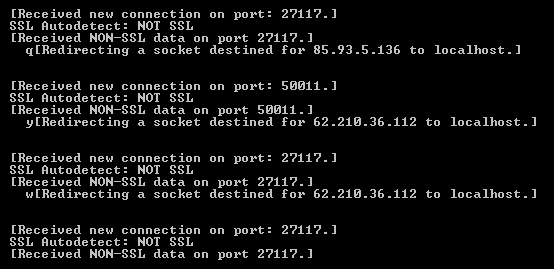
- 43.147.209:40071
- 174.102.20:17771
- 183.160.137:6317
- 183.160.137:8181
- 248.100.188:7454
- 126.77.137:4119
- 126.77.137:4357
- 126.77.137:4358
- 126.77.137:443
- 126.77.137:6317
- 126.77.137:8181
- 126.77.137:9090
- 142.30.201:1192
- 142.30.201:1193
- 142.30.201:17771
- 142.30.201:17799
- 142.30.201:9290
- 28.179.200:10012
- 28.179.200:27117
- 165.16.165:1444
- 165.16.165:1445
- 165.16.165:17771
- 165.16.165:19991
- 165.16.165:22143
- 165.16.165:22144
- 165.16.165:7450
- 165.16.165:7451
- 165.16.165:7453
- 165.16.165:8181
- 165.16.165:8289
- 165.16.165:9090
- 165.16.166:17771
- 165.16.166:443
- 165.16.166:444
- 165.16.199:17771
- 165.16.165:17799
- 228.232.92:1192
- 228.232.92:1195
- 228.232.92:1196
- 184.234.108:10011
- 184.234.108:10012
- 161.40.145:1192
- 161.40.145:1193
- 161.40.145:1195
- 161.40.145:1196
- 161.40.145:1393
- 161.40.145:17771
- 161.40.145:4356
- 161.40.145:4357
- 161.40.145:4358
- 161.40.145:4360
- 161.40.145:443
- 161.40.145:444
- 161.40.145:8181
- 161.40.145:9290
- 8.18.222:1191
- 8.18.222:1192
- 8.18.222:17771
- 210.36.112:27117
- 210.36.112:3341
- 72.84.115:17771
- 93.20.42:1191
- 93.20.42:1192
- 93.5.136:50011
- 197.232.26:17771
- 197.232.26:9090
- 154.199.104:27117
We have been monitoring varying hits over the past few days for the signature that blocks this threat:
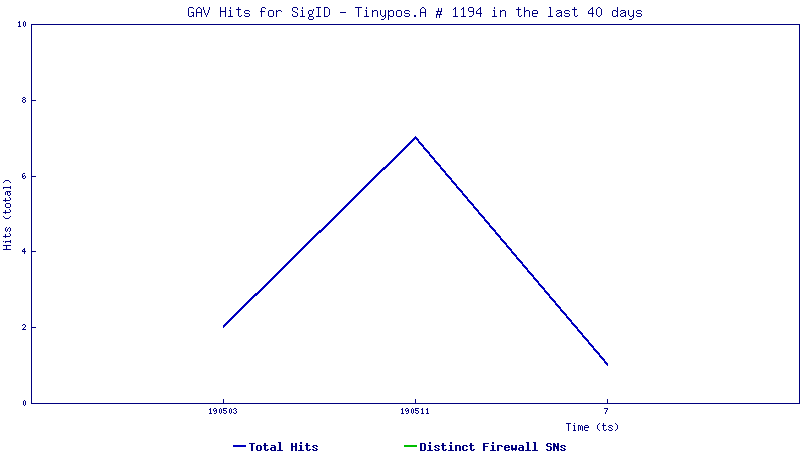
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: TinyPOS.A (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




