Threat actors are misusing Coronavirus scare to spread malicious executable
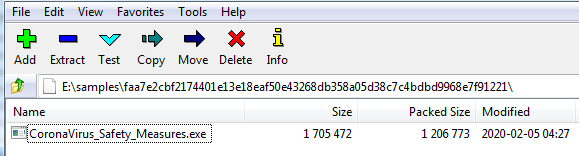
Today, everyone is aware about the deadly coronavirus (2019-nCoV) that was first reported from Wuhan – China, on 31 December 2019 and now spreading world wide. While the world is fighting against this deadly coronavirus and running various awareness campaigns and sharing document related to precautionary measures, cyber threat actors are taking this as an opportunity to get benefits from the fear of people by distributing malware files and claiming them as awareness supporting document for the coronavirus. SonicWall RTDMI ™ engine has recently detected an archive file which contains an executable file named “CoronaVirus_Safety_Measures.exe”. The archive is delivered to the victim’s machine as an email attachment:
After diving deep into the executable file, we found that the file belongs to GOZ InfoStealer family which was first detected by SonicWall RTDMI ™ engine on Nov 22, 2019.
“The GOZ InfoStealer is known for stealing user data from installed applications, along with victim’s system information, which is then sent to the threat actor over Simple Mail Transfer Protocol”
The malware author is continuously updating the malware code and changing its infection chain. SonicWall CaptureLabs Threats Research team is continuously monitoring the malware variants:
First Variant:
This variant uses image stenography as a part of its infection chain and sends the stolen data to the malware author’s email address over Simple Mail Transfer Protocol (SMTP).
Second Variant:
The JavaScript file is delivered to the victim’s machine as an email attachment which drops and executes the GOZ InfoStealer. The major change observed in this variant is, the malware author is using his own email address for sending and receiving stolen data.
Recent Variant:
An AutoIt compiled binary is delivered to the victim’s machine inside an archive, as an email attachment which executes the GOZ InfoStealer on victim’s machine. The AutoIt compiled binary is named “CoronaVirus_Safety_Measures.exe” to mislead the victim.
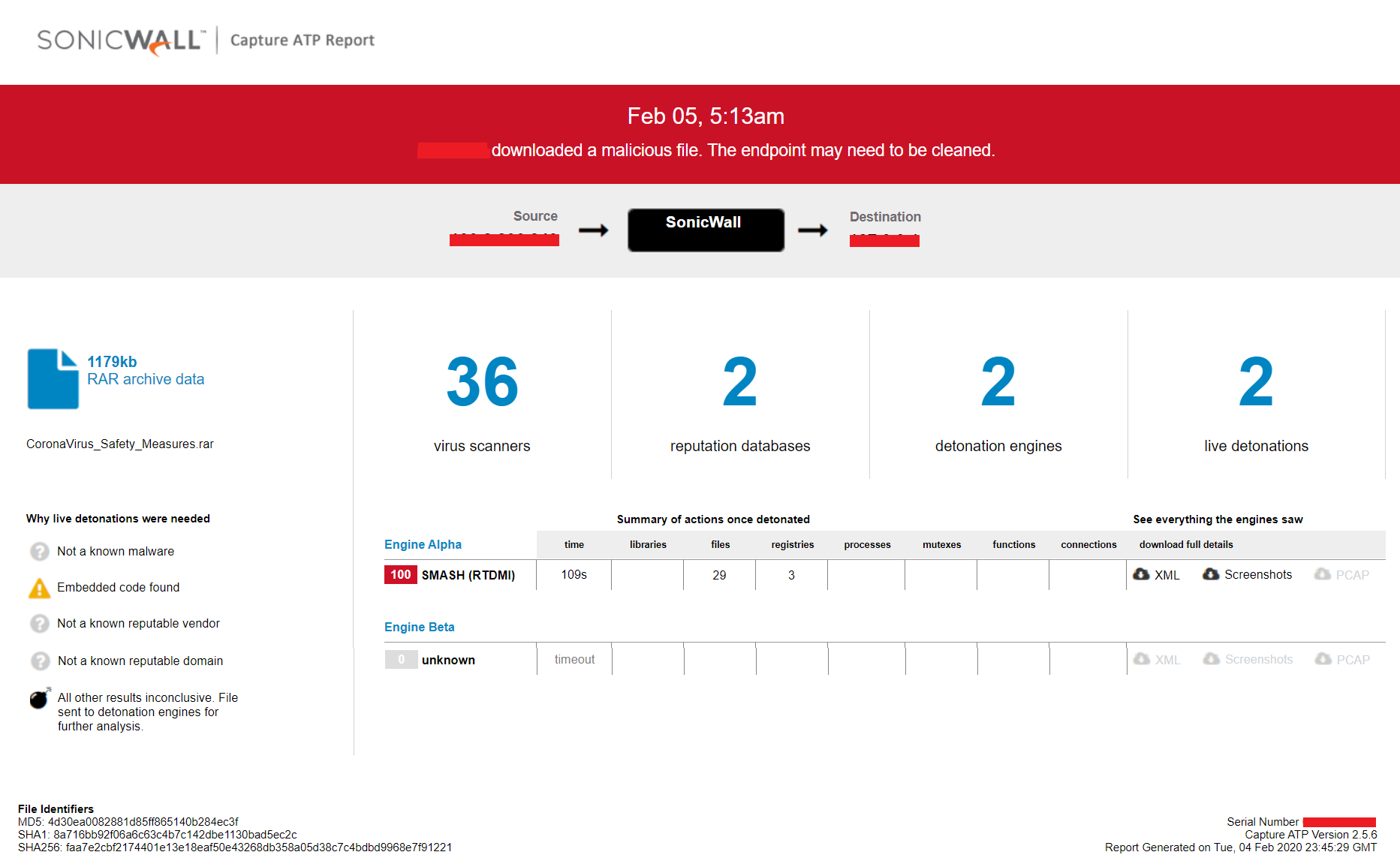
Evidence of the detection by RTDMI engine can be seen below in the Capture ATP report for this file:
Additional Remark:
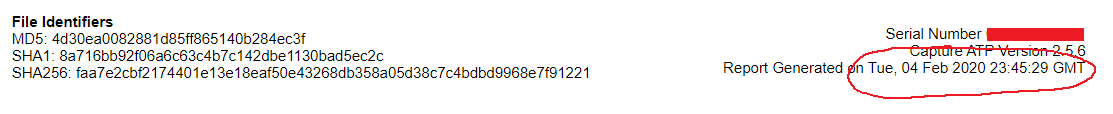
Please note that the RTDMI engine analyzed and gave us a verdict for these samples as ‘Malicious’ on February 04, 2020 as visible in the report:
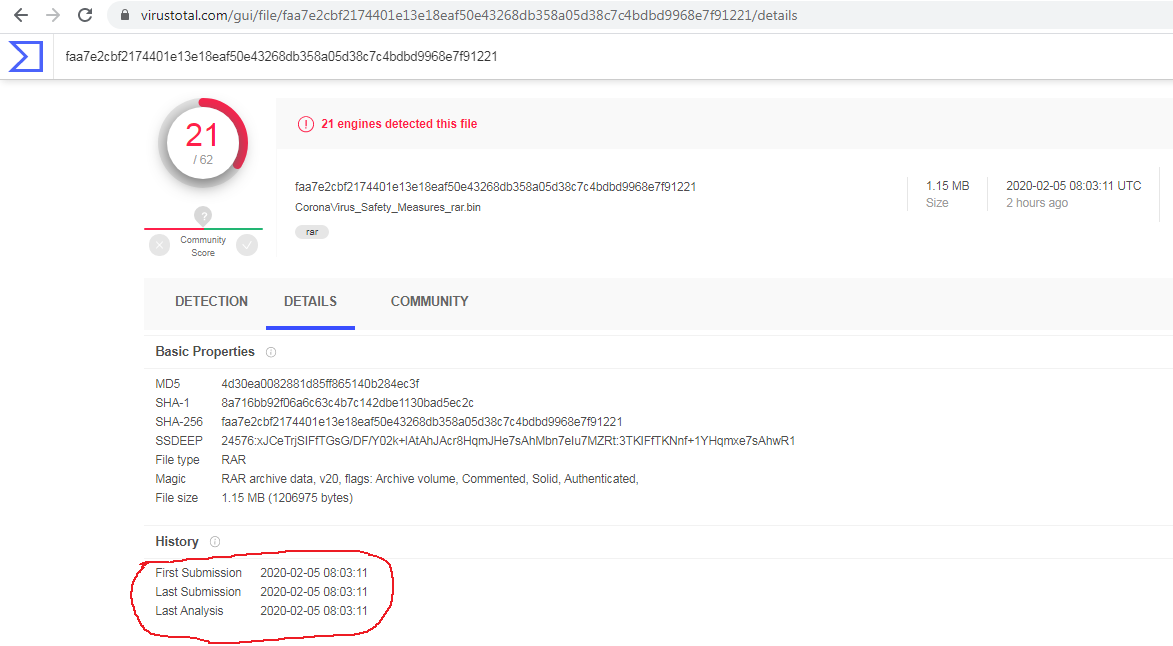
Whereas the sample was first seen on Virustotal 8 hours later – on February 05, 2020 – as evident by the ‘First Submission’ date: