This Android adware bombards the infected device with a flood of advertisements
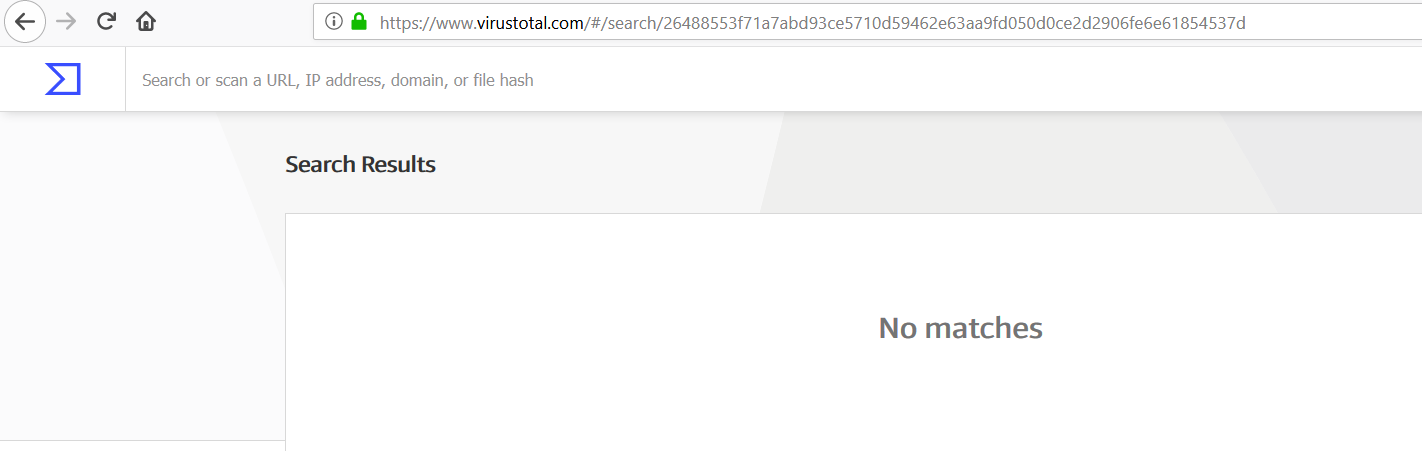
SonicWall RTDMI engine recently detected an AndroidAdware which has an app icon that looks similar to the Settings app icon. The non-existence of this malicious file at the time of detection on popular malware search portals like the VirusTotal and the Reversing Labs indicates the effectiveness of the RTDMI engine.
When a user clicks on the app icon, it starts its execution in the background and hides itself from the app list as shown below:
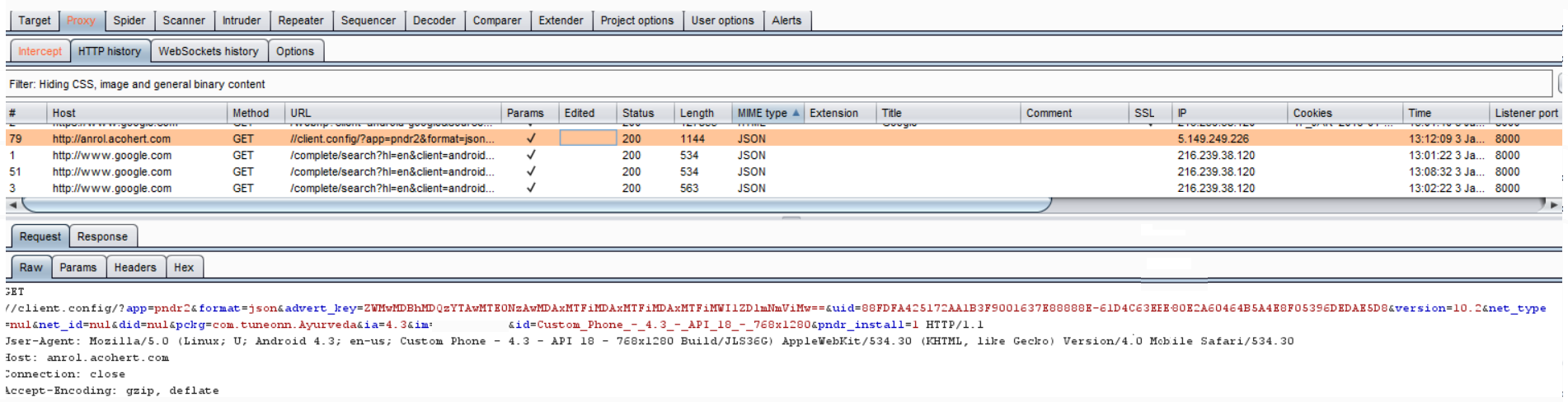
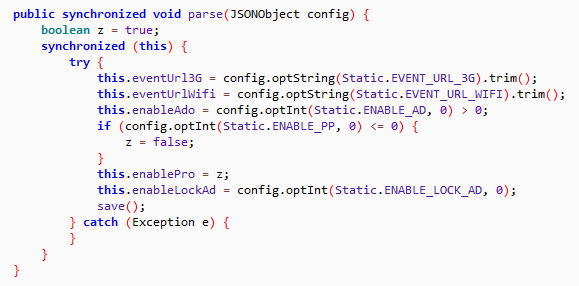
It then connects to a malicious URL, sends victim’s device information and saves the response data into a file named “Config” as shown below:
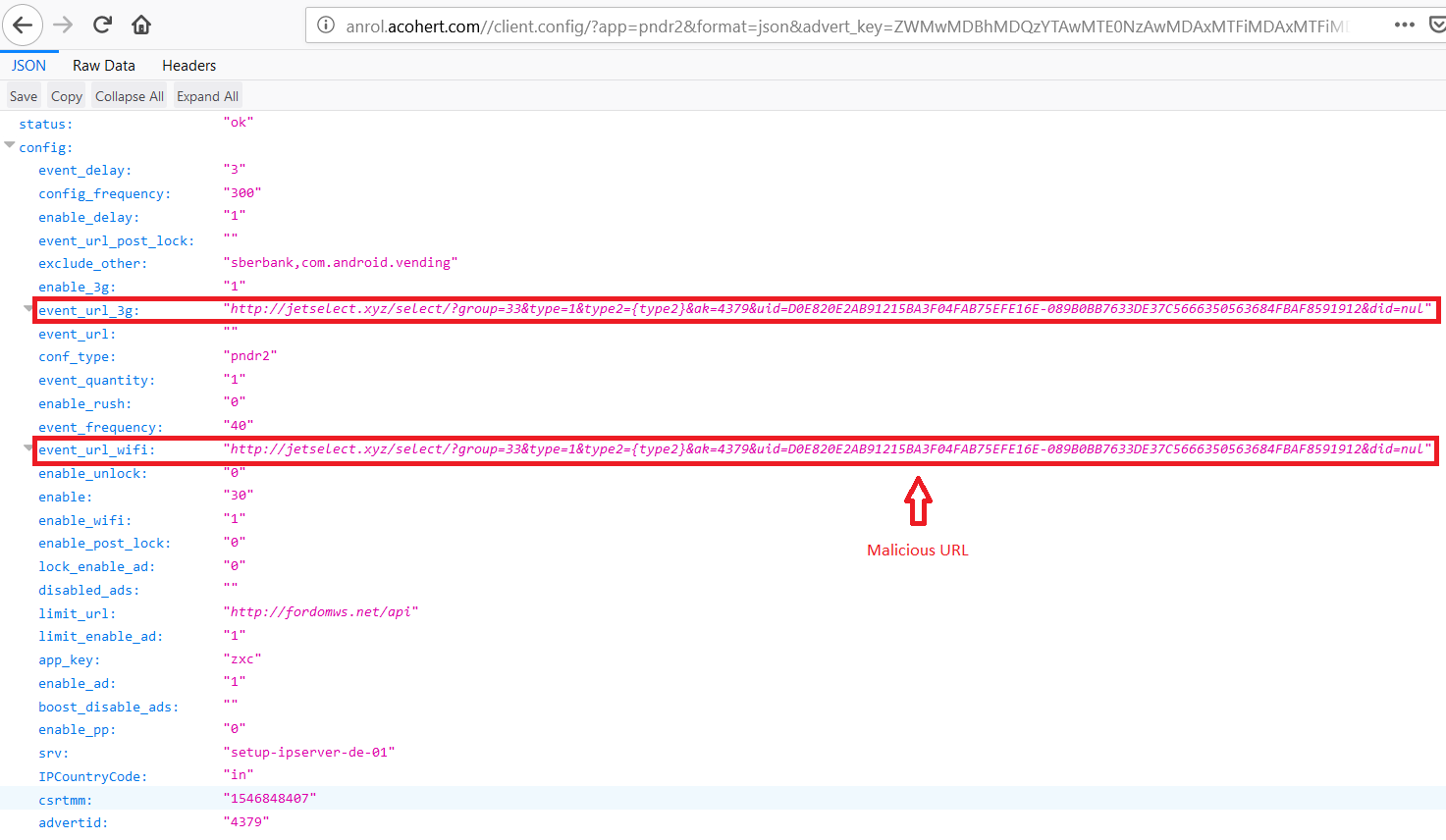
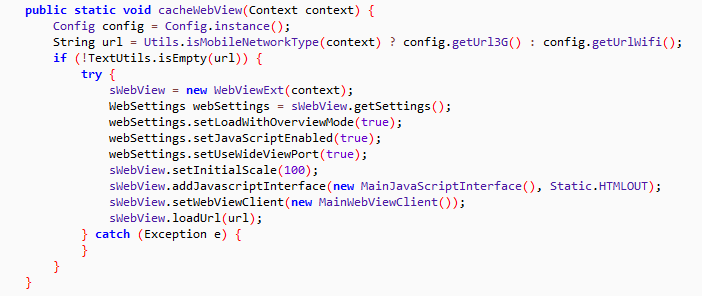
The response data from the server is in JSON format which contains events to identify the victim’s device’s Internet connectivity type (WiFi, Mobile Data) as shown below:
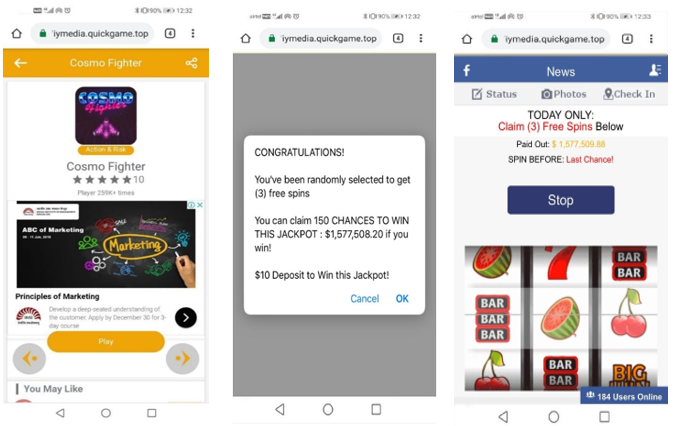
Depending on the victim’s connectivity type, a malicious URL is opened and the victim is flooded with random ads as shown below:
Indicators of Compromise:
- 26488553f71a7abd93ce5710d59462e63aa9fd050d0ce2d2906fe6e61854537d
- 0dd8b10e28064f2313f00077878ae4ac5294e0127678f99dfcfea2a078a1dfdc
- 149a8c0006b0e6a9a9a101b7fdbc14c18ebca68c520c6114a75730bb7f0972bd
- 1a5df9c0ef2630562548c3e00468ff3751aa2852bd0edbdfae7da84581d19084
- 21af8c88f65b04c68b46f7f03e2e61a67b8668bab8350883ad83409369c7bba2
- 3427219c03d7d06b209ad951932e311e6d585f69460da1cf3ba4631d0dee97f7
- 4c8046e9e1726a9f5fbfa254e341e49d8f6889ed599600d4c1950c4b16fd8e36
- 51178010b9ffc2e14aaddf47310b2ce7de98860c8fd9d33d7e4da81c6c1f71aa
- 829226de4d2c91744438e549dac7a6bacea63a4796e345bedf9ec7e54c6a3ba2
- 8a6418a0f647efd5470106c192c9366243e1ab979e48658bb790affafd724de6
- c5a195275cca84707878f5c5b6e802a7612a35d168bfd7dee419499094729683
- d1542dba9da8c3154d4a45e53a62ff9653881f775d5da72e4b6428483e427584
- e271c4e9c432bb816e028e506b69f341472dfe7e502b1c7ce6462ff60032d5d3
- e446d7e8e4af373d474b493c744884ad46e5d450083fd7589b23e136f0678853
- f32c8320446da90a72fc8cea3f3c928735a5dc239ec7f72e0d26df41372332b0
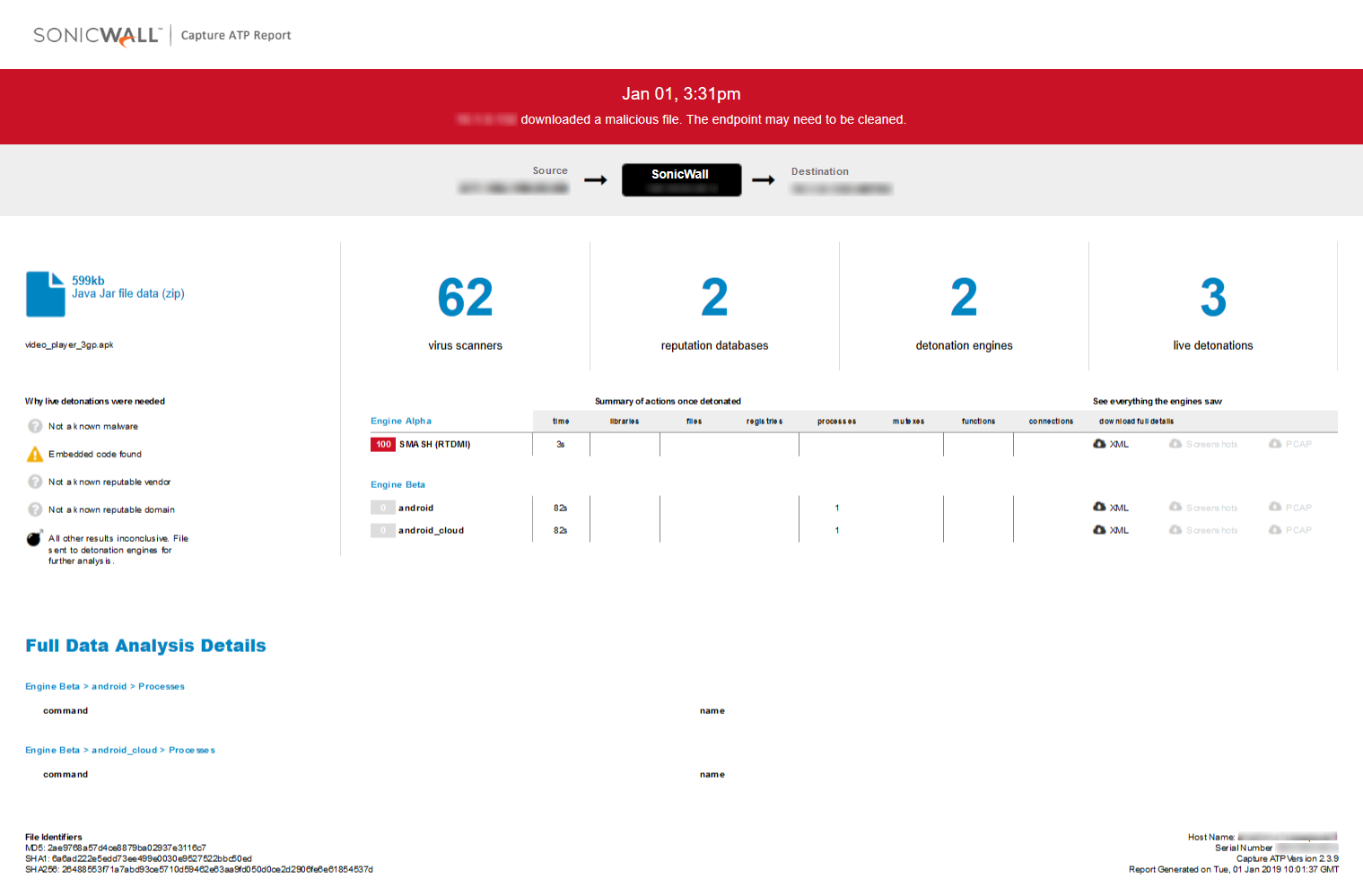
Shown below is the Capture ATP report of the malicious APK file detected by the RTDMI engine: