TerraMaster Remote Command Execution Vulnerability
TerraMaster Technology is a Chinese company that specializes in computer software, network attached storage (NAS), and direct attached storage (DAS).TerraMaster’s products are sold in more than 40 countries. Its main products are personal/home cloud storage, small/medium Business Network Storage, enterprise network storage server, home/SOHO RAID storage, video professional RAID storage.
TerraMaster NAS Remote Command Execution Vulnerability | CVE-2022-24990
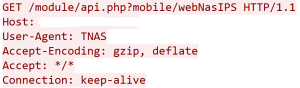
TerraMaster NAS 4.2.29 and earlier allows remote attackers to discover the administrative password by sending “User-Agent: TNAS” to module/api.php?mobile/webNasIPS and then reading the PWD field in the response.
SonicWall Capture Labs Threat Research Team observed attackers targeting this vulnerability in the wild.
The CVSS(Common Vulnerability Scoring System) score is 7.5 with Vector: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is none.
- Impact of this vulnerability on data availability is none.
TerraMaster NAS devices running TOS version 4.2.29 suffer from a vulnerability which allows remote unauthenticated attackers to execute commands as root. Following is an example of a way this could be exploited.
The module webNasIPS is vulnerable due to the way it processes requests when the User-Agent is TNAS . When the ‘webNasIPS’ function of ‘mobile ‘ class is initiated by the api.php , it ignores the authentication check and returns sensitive information. The response contains information regarding password hash , TOS firmware, default gateway, interface’s IP and mac address.
The PHP object instantiation could lead to unauthenticated remote command execution with root privileges.
SonicWall Capture Labs provides protection against this threat via following signature:
- IPS 15830:TerraMaster NAS Information Disclosure
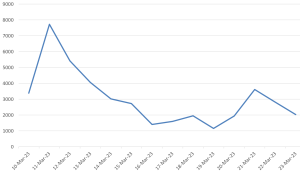
Threat Graph