SymmiWare Ransomware will only decrypt after Nov 25th
The SonicWall Capture Labs Threat Research Team have recently spotted a ransomware trojan calling itself SymmiWare. There have been other malware named “Symmi” in the past, however, this ransomware does not appear to be related. SymmiWare is unusual in that the operators are only offering decryption after November 25th 2018. The supplied email address in the ransom note is not currently active but is expected to be after this date.
Infection Cycle:
The trojan uses the following icon:

Upon running the executable the trojan reports the infection to a remote server:
![]()
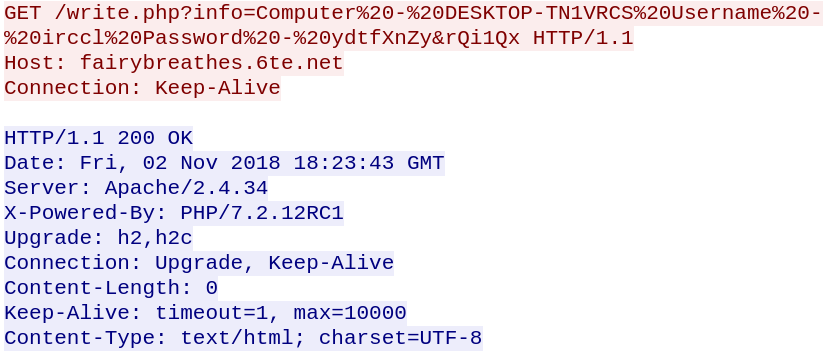
The trojan encrypts files on the system and appends “.SYMMYWARE” to the file extension of each encrypted file. It also drops SYMMYWARE.TXT into every directory containing encrypted files.
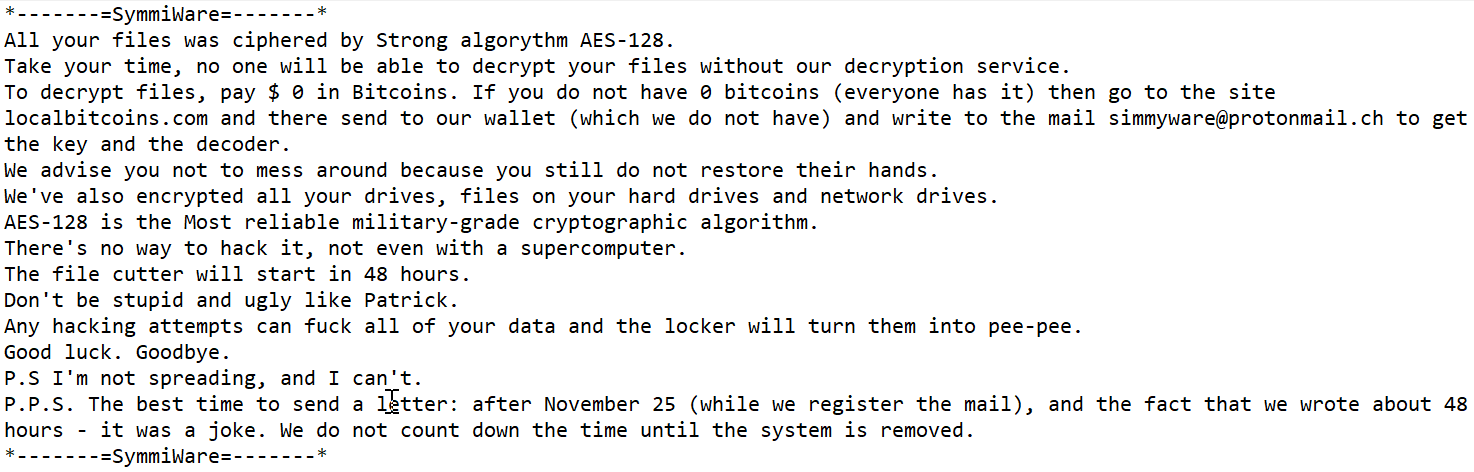
SYMMYWARE.TXT contains the following text:
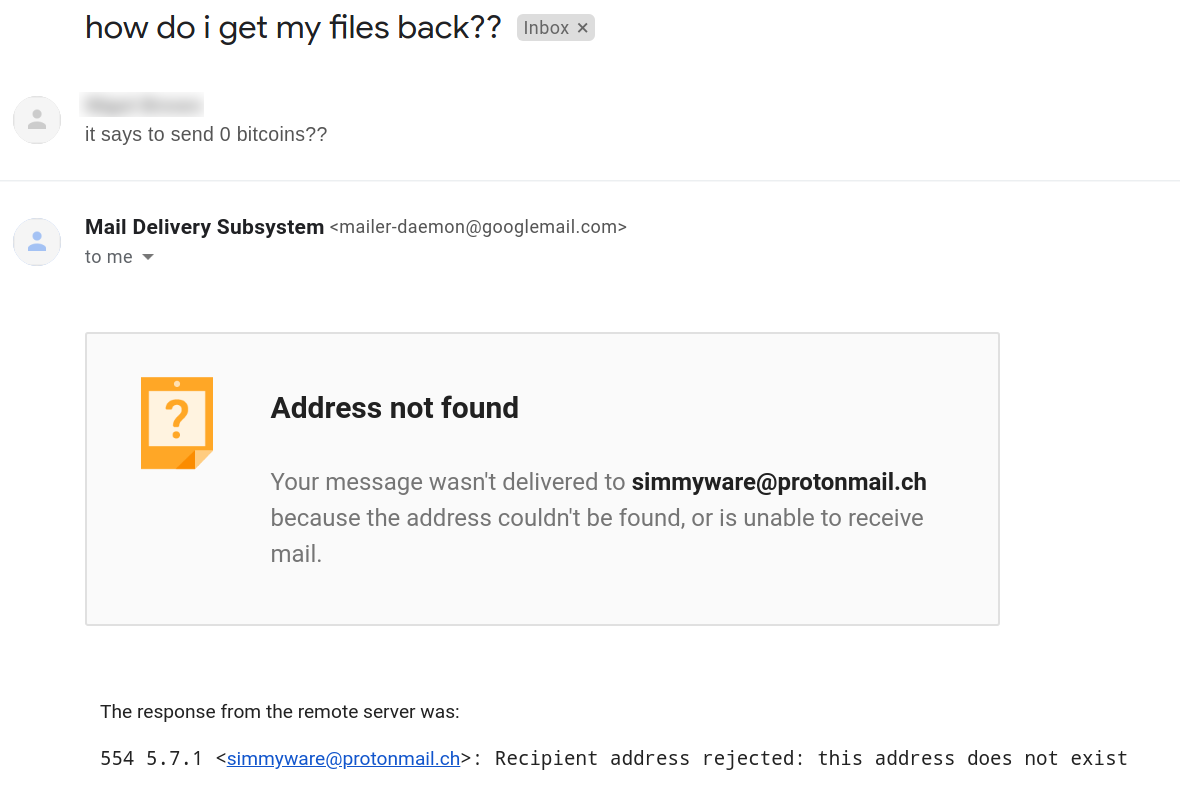
We tried to contact the operators via simmyware@protonmail.ch but as stated in the above message the address is not yet active:
SonicWALL Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: Symmi.RSM (Trojan)




