Sodinokibi ransomware uses Oracle WebLogic exploit to infect servers
The SonicWall Capture Labs Threat Research Team have observed reports of Sodinokibi, ransomware that exploits a deserialization vulnerability in Oracle WebLogic servers (CVE-2019-2725) as its primary infection vector. The exploit has also been used by other attackers to install crypto miners, info stealers and botnets. The attackers charge $1500 USD in Bitcoin for file decryption if the ransom is paid within 7 days. If the ransom is not paid within this period it doubles to $3000 USD.
Infection Cycle:
The trojan uses the following icon:

Upon infection, the following text and background is displayed on the desktop:

It makes the following DNS query:
- breathebettertolivebetter.com
It creates the following files:
- 0vhra-readme.txt (copied to every directory containing encrypted files)
- 2cb12ec9.lock (0 bytes. copied to every directory containing encrypted files)
It adds the following keys to the registry:
- HKEY_LOCAL_MACHINE\SOFTWARE\recfg rnd_ext “.2cb12ec9”
- HKEY_LOCAL_MACHINE\SOFTWARE\recfg pk_key (encryption key related hex values)
- HKEY_LOCAL_MACHINE\SOFTWARE\recfg sk_key (encryption key related hex values)
- HKEY_LOCAL_MACHINE\SOFTWARE\recfg 0_key (encryption key related hex values)
- HKEY_LOCAL_MACHINE\SOFTWARE\recfg stat (encryption key related hex values)
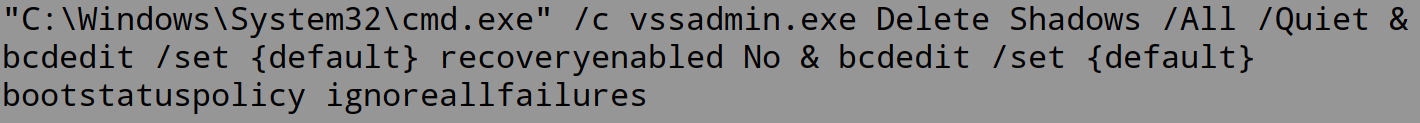
It executes the following command to disable startup repair and remove Windows shadow copies:
It encrypts files on the system and gives each file an extension consisting of a random alphanumeric string. In this case “2cb12ec9“.
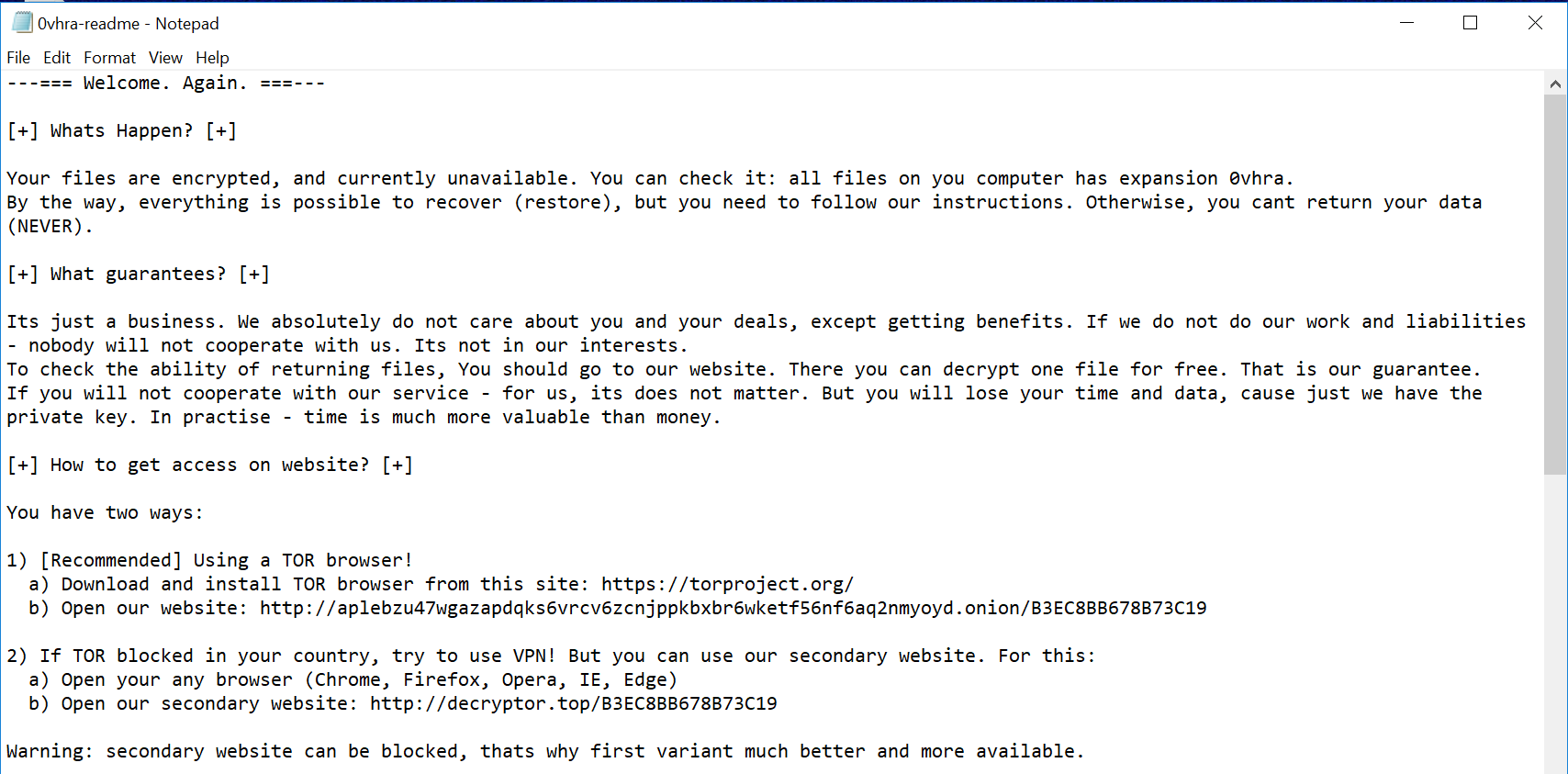
0vhra-readme.txt contains the following message:
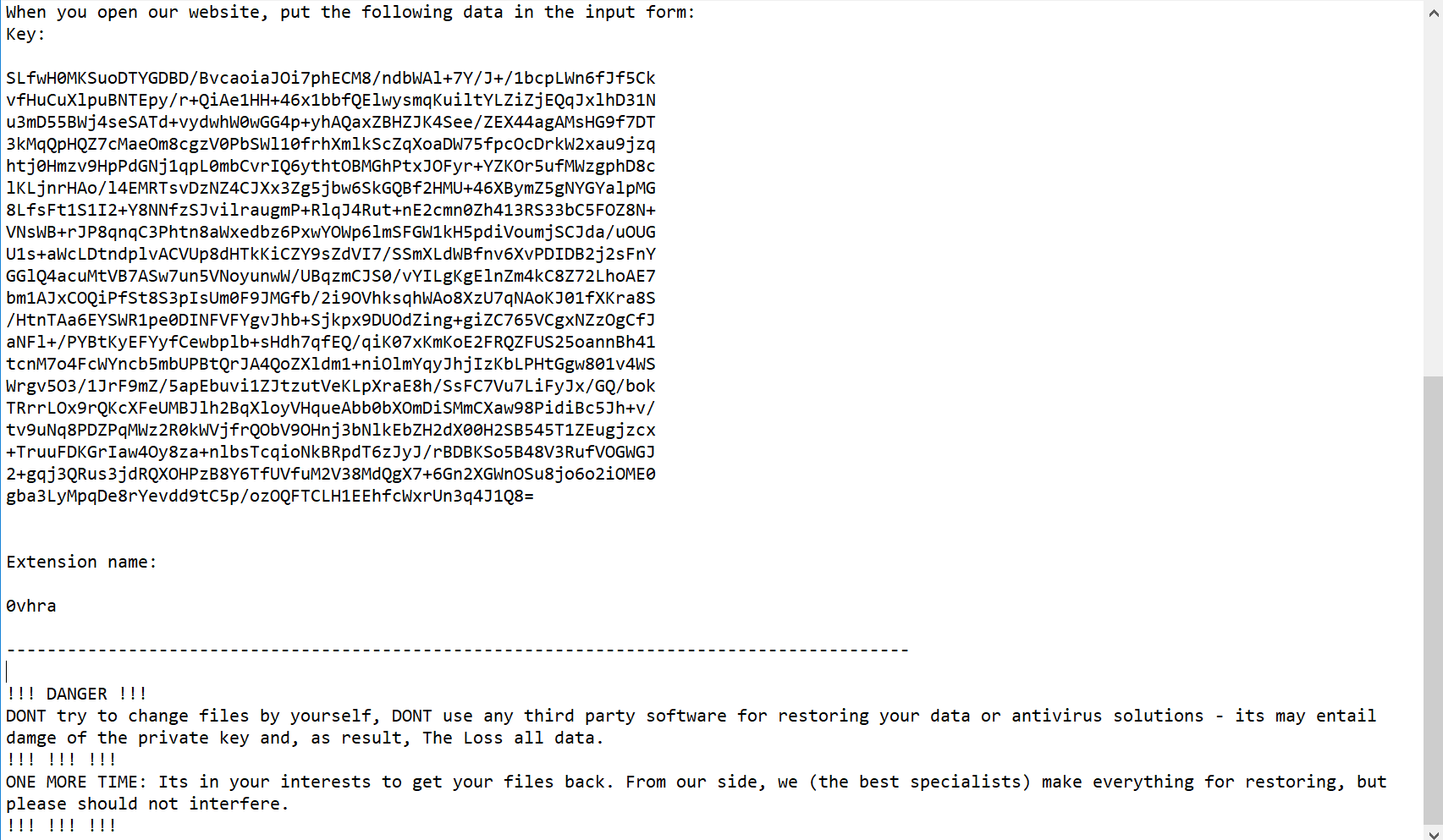
The following link is provided in the message:
http://aplebzu47wgazapdqks6vrcv6zcnjppkbxbr6wketf56nf6aq2nmyoyd.onion/B3EC8BB678B73C19
It is a webpage that is located on the tOR network:
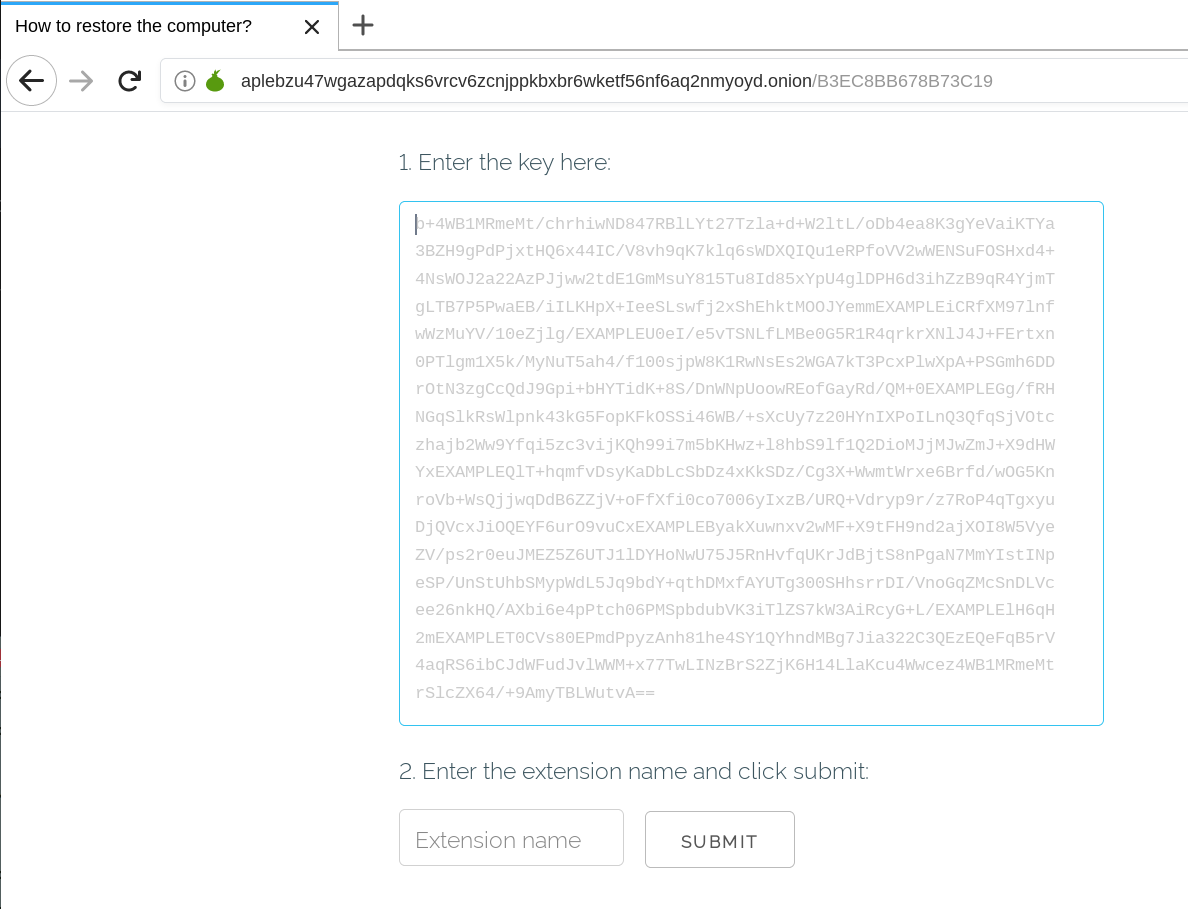
Pressing “SUBMIT” or opening the second link (http://decryptor.top/B3EC8BB678B73C19) leads to the following page:
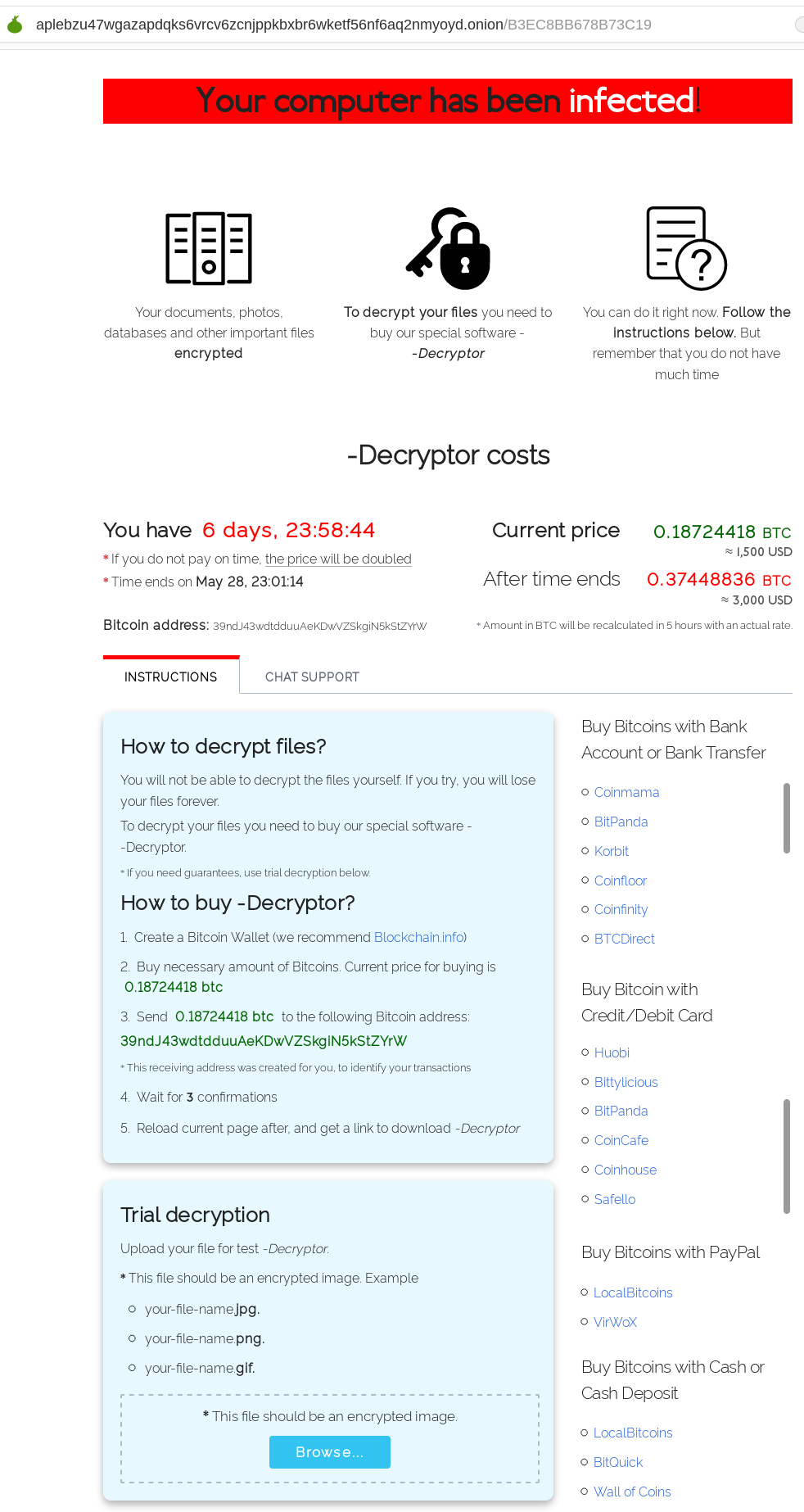
SonicWALL Capture Labs provides protection against this threat via the following signatures:
- GAV: Sodinokibi.RSM_4 (Trojan)
- GAV: Sodinokibi.RSM_3 (Trojan)
- GAV: Sodinokibi.RSM_2 (Trojan)
- GAV: Sodinokibi.RSM (Trojan)
- GAV: Sodinokibi.FN (Trojan)
- IPS: 14180 Oracle Weblogic 10.3.6.0.0/12.1.3.0.0 Remote Code Execution 1
- IPS: 14181 Oracle Weblogic 10.3.6.0.0/12.1.3.0.0 Remote Code Execution 2
- IPS: 14186 Oracle WebLogic Server Insecure Deserialization 9
- IPS: 14187 Oracle WebLogic Server Insecure Deserialization 8
- WAF: 1706 Oracle Weblogic 10.3.6.0.0/12.1.3.0.0 Remote Code Execution
Also, this threat is detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




