RTF exploits in the wild
SonicWall Threat Research lab is seeing a huge volume of RTF exploits with embedded OLE objects exploiting the Microsoft vulnerabilities (CVE-2017-11882 & CVE-2017-0199 ). CVE-2017-11882 is because of incorrect handling of embedded Equation Editor OLE objects in Office documents and CVE-2017-0199 is due to incorrect parsing of embedded OLE2Link objects. Successful exploitation in both the cases can lead to arbitrary code execution under the context of the host.
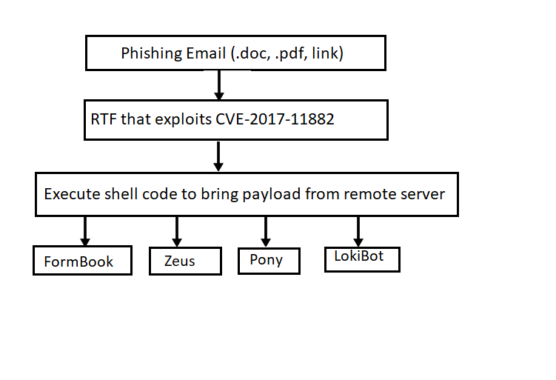
Infection cycle:
This gets started by sending phishing campaign to the target user either with an attachment or a link to a compromised website hosting the malicious document. Malicious document can either be a Word or PDF with embedded (.rtf) Rich Text Format file. Upon launching the main document, embedded .rtf file which actually exploits the above mentioned vulnerabilities get exported & executed. When .rtf file is done exploiting, control returns to the attacker’s specified address where the shell code is present. When shell code gets executed, it brings down the payload from the remote server and execute it on the compromised machine. We see many variants of final payloads getting delivered through these exploits and upon execution they create a reverse shell and give the attacker control over the host.
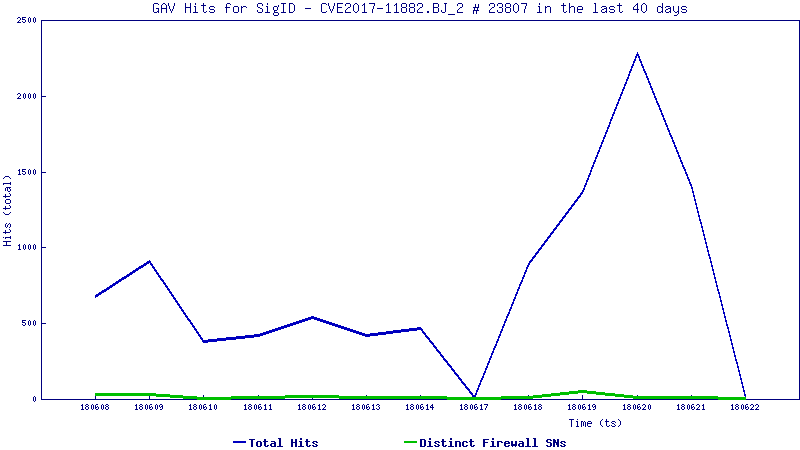
Trend Graph:
The trend line below shows how this attack is being used in the wild today:
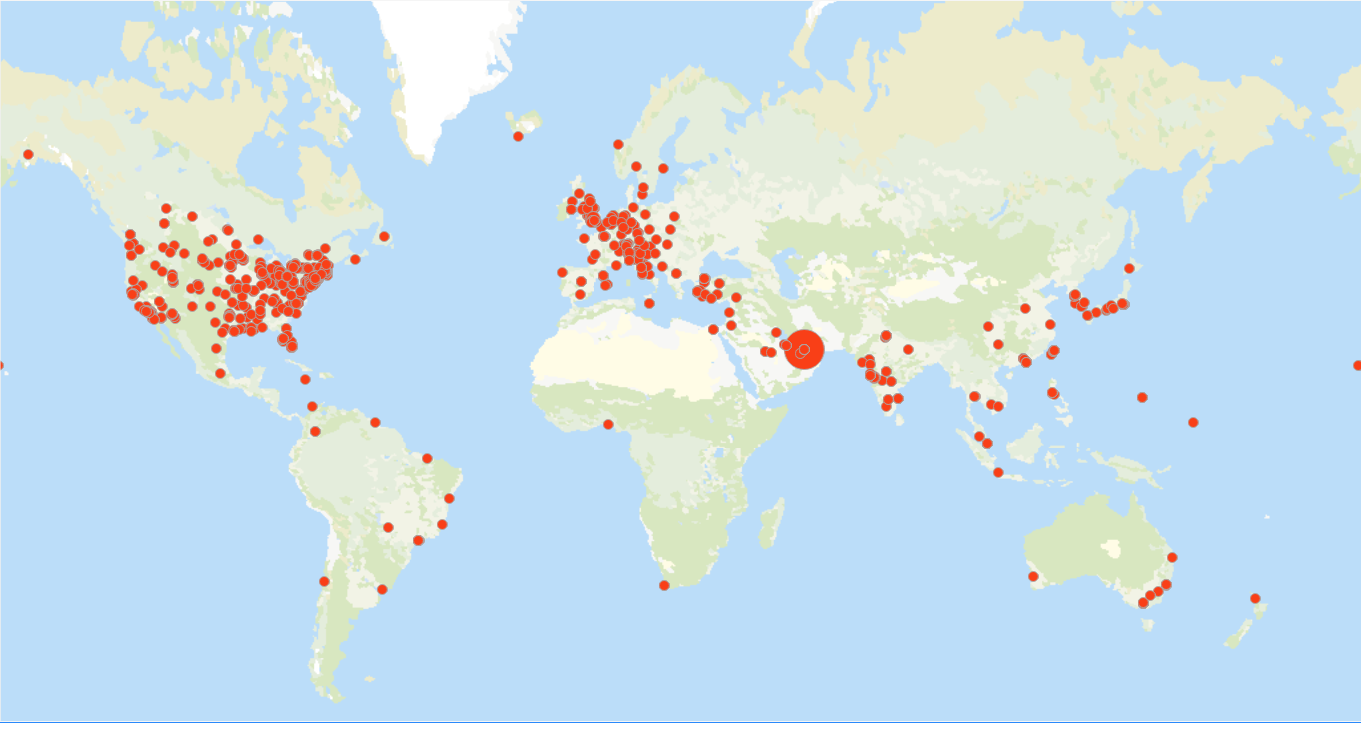
Prevalence Map:
This can be mitigated by using the up-to-date software with all the security patches. Enable protected view for office documents and do not allow editing of RTF files. Review carefully before editing or doing anything that requires Protected View to be disabled.
SonicWALL Threat Research Lab provides protection against this threat via the following signatures
- GAV: 23807 CVE2017-11882.BJ_2
- SPY: 5164 Malformed-File pdf.MP.316




