Rise of Android malware masquerading Covid related themes
Malware writers often use trending topics to masquerade their malicious creations. Ever since early 2020 the Covid-19 pandemic has given fuel to malware writers and scamsters to use Covid related themes to hide malicious applications. SonicWall Threats Research team has been observing Covid related Android malware since mid-2020. This blog highlights how Android malware trends have corresponded with the rise in Covid related mortality rate in different parts of the world.
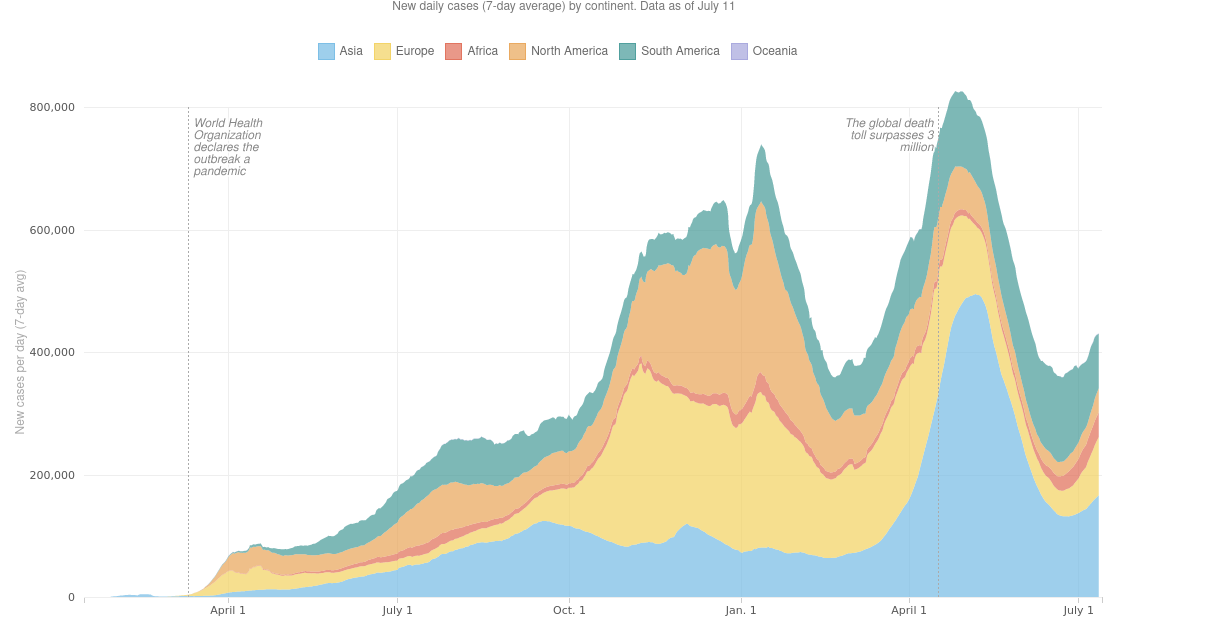
The graph below shows Covid related deaths as seen in different parts of the world between April 2020 and July 2021 where peaks were visible in the following months –
- March, 2020
- August-September, 2020
- November-December, 2020
- January, 2021
- May-June, 2021
Covid related Android malware trends – 2020
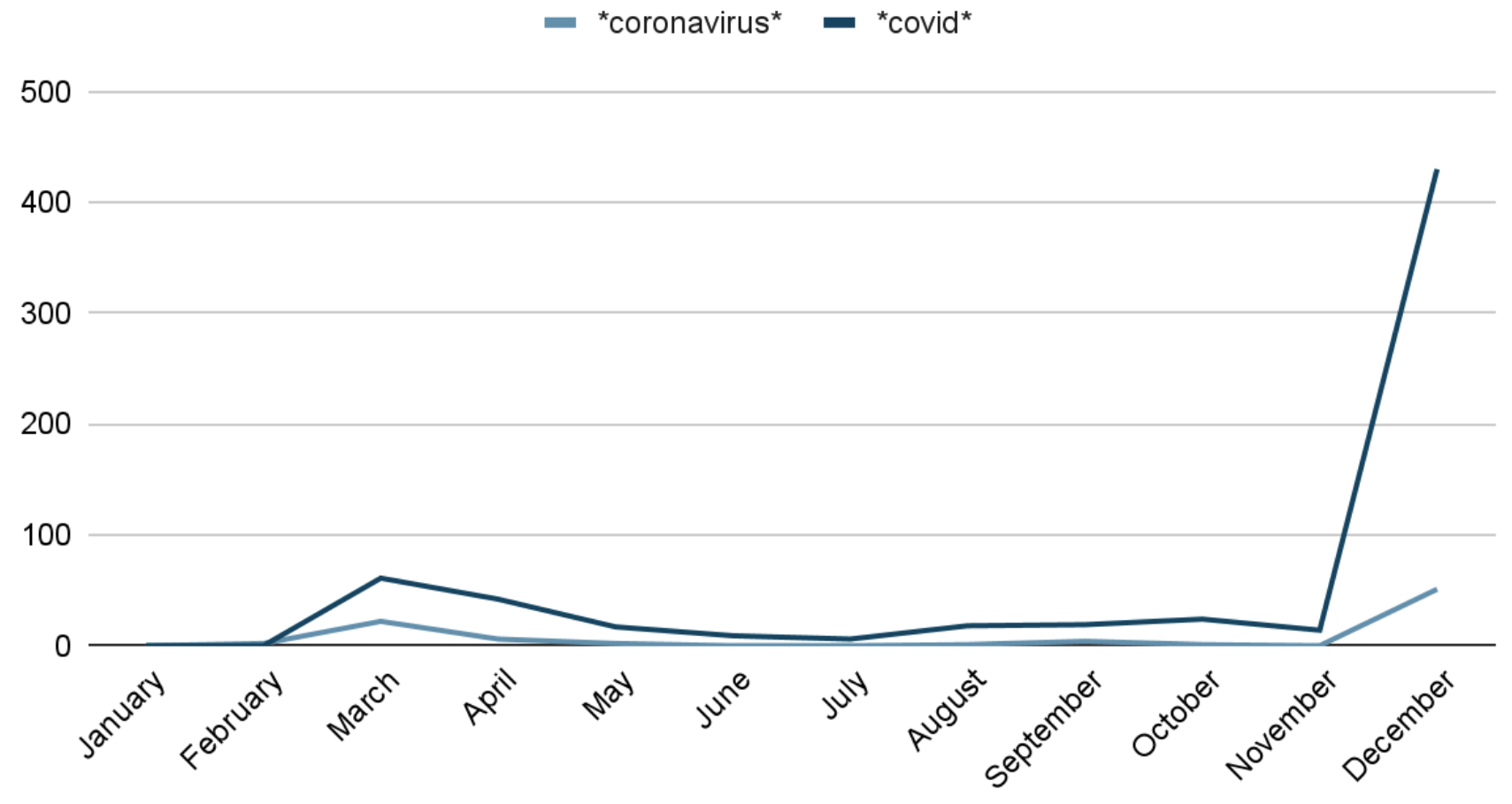
- Keywords – Coronavirus, Covid
The graph below shows malicious Android apps with the application name and package name containing the keywords – Coronavirus, Covid. This graph has few peaks that coincide with the graph that shows Covid related deaths seen worldwide.
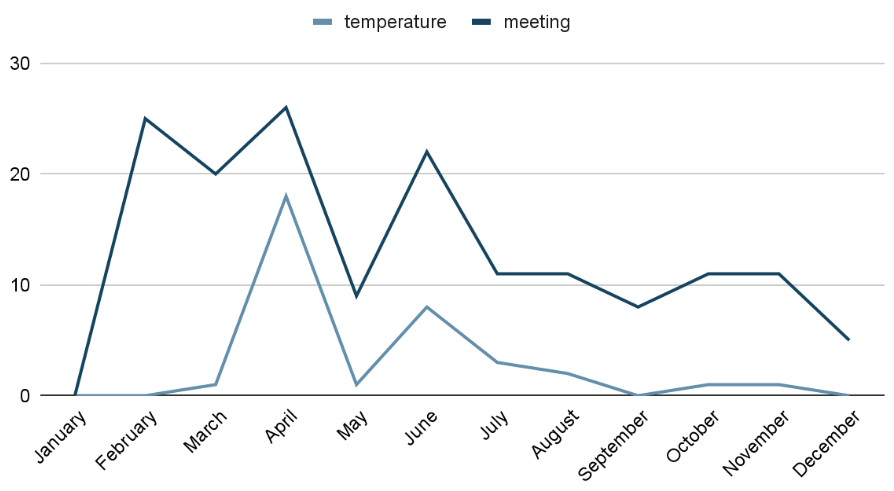
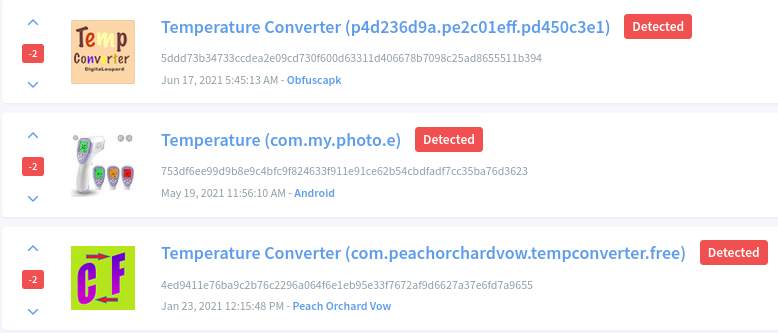
- Keywords – Temperature, Meeting
Working from home became a common practice for a lot of workforce around the world. As a result online meeting related apps became very popular. As a result we see a number of malicious Android apps with names related to online meetings rise during few months that coincide with peaks related to Covid related infections.
During the first peak in March, high body temperature was one of the main symptoms of Covid infection, as a result malicious apps that claim to check the temperature also became popular among malware writers. Peak in numbers for fake temperature related malicious Android apps coincide with the first graph related to Covid infections.
Covid related Android malware trends – 2021
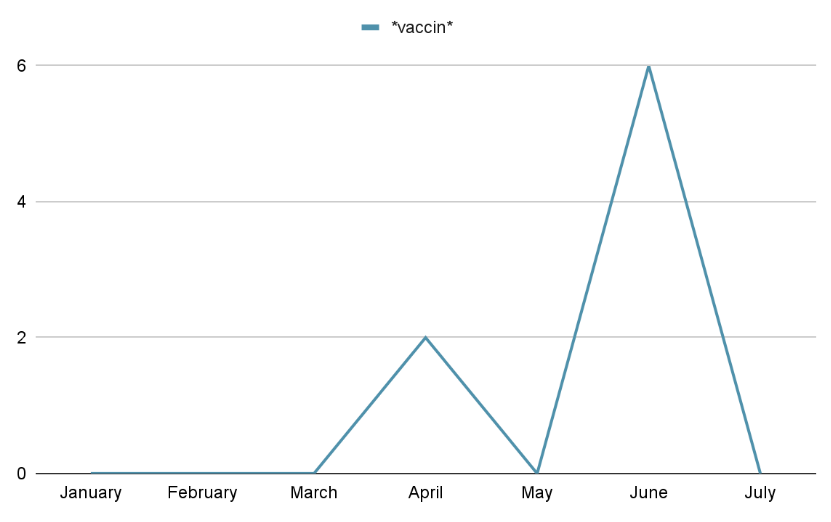
- Keywords – Vaccination
Vaccinations started in the early months of 2021 all over the world and slowly ramped up as time progressed. Shortly we started seeing vaccination themed malicious android malware as anticipated
Covid related Government Apps
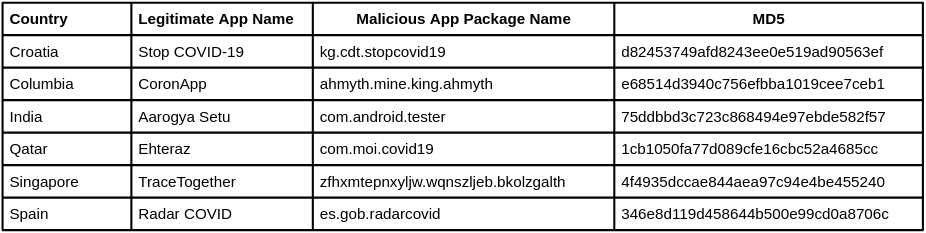
Countries all around the world developed apps on multiple platforms to monitor and trace people who got infected during the pandemic. Unsurprisingly malware writers used this opportunity to masquerade malicious apps using the name of legitimate government applications. Below are malicious counterparts of legitimate government apps:
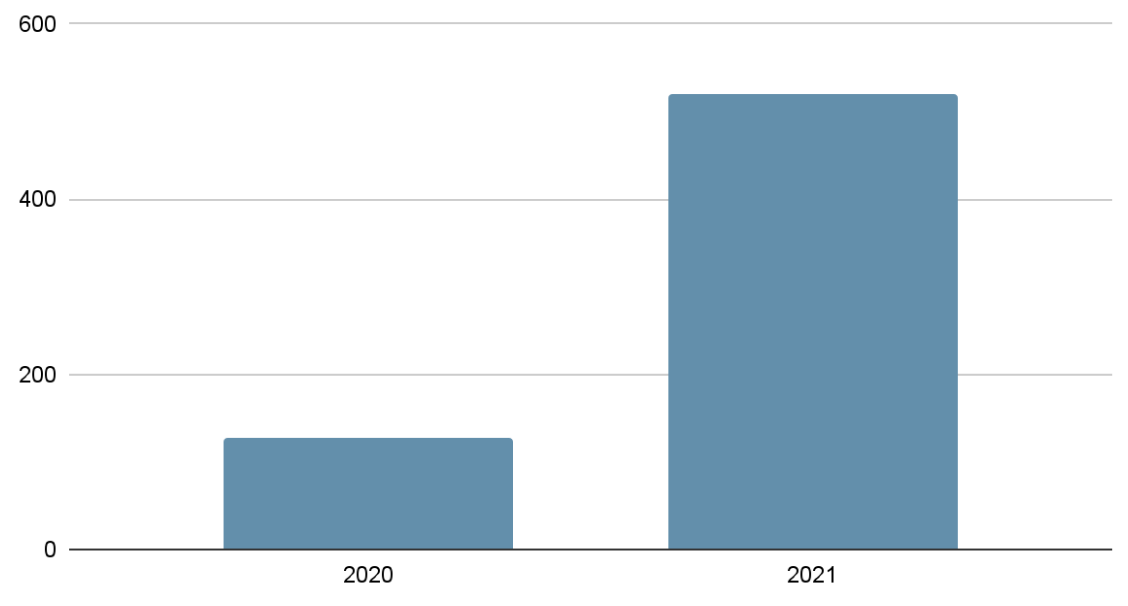
Among the government Covid related apps, Aarogya Setu from India was the one that was masqueraded the most. We have seen malicious apps passed as Aarogya Setu apps for both 2020 and 2021:
It is safe to say that Covid has been a very lucrative topic for malware writers as they have used this label to hide their malicious creations. While the pandemic is far from over, Covid related malware is expected to rise as time passes.
Sonicwall Capture Labs provides protection against multiple threats associated with Android Covid related malware, some of the signatures are listed below:
- AndroidOS.Cerberus.COVID
- AndroidOS.Cerberus.COVID_2
- AndroidOS.HiddenAd.COVID
- AndroidOS.CoronaTracker.BNK
- AndroidOS.Corona.IR
- AndroidOS.Corona.IR_3
- AndroidOS.CoronaVirus.Spy
- AndroidOS.Banker.COVID_2
- AndroidOS.CoronaTracker.RSM
References
- https://www.ajmc.com/view/a-timeline-of-covid-19-vaccine-developments-in-2021
- https://en.wikipedia.org/wiki/COVID-19_apps