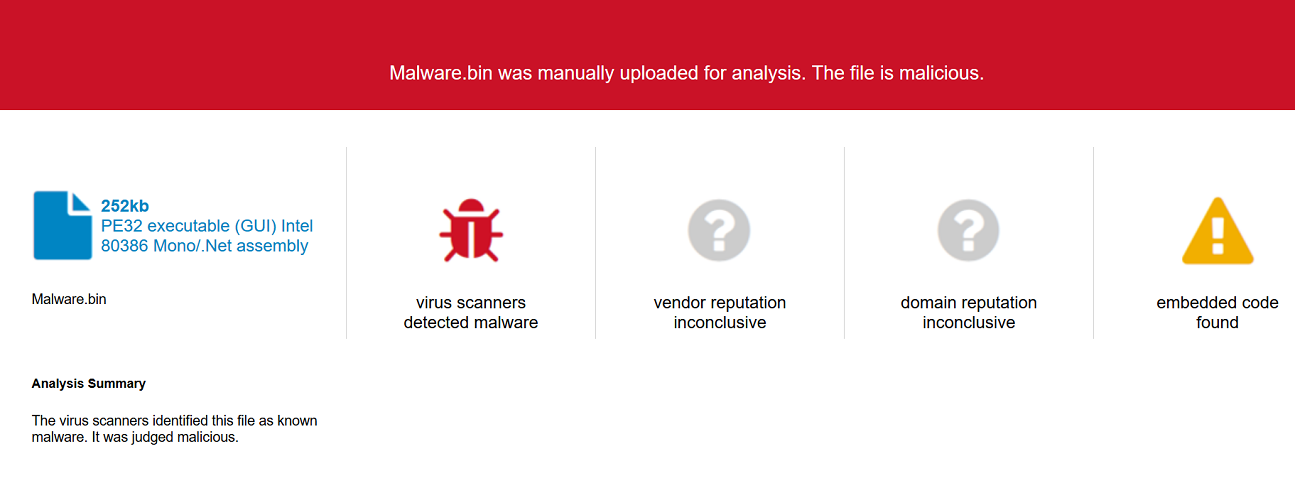
Reha ransomware targeting Arabic speaking countries.
The SonicWall Capture Labs threat research team observed reports of a new variant family of Reha ransomware [Reha.RSM] actively spreading in the wild.

The Reha ransomware encrypts the victim’s files with a strong encryption algorithm until the victim pays a fee to get them back.
The ransomware targeting Arabic speaking countries and designed for very specific region.
Infection Cycle:
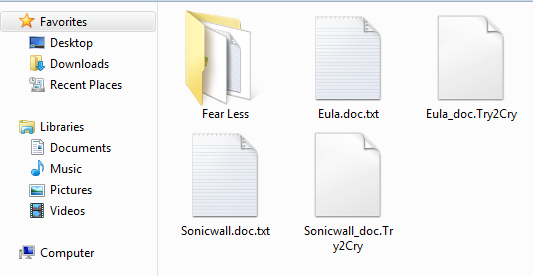
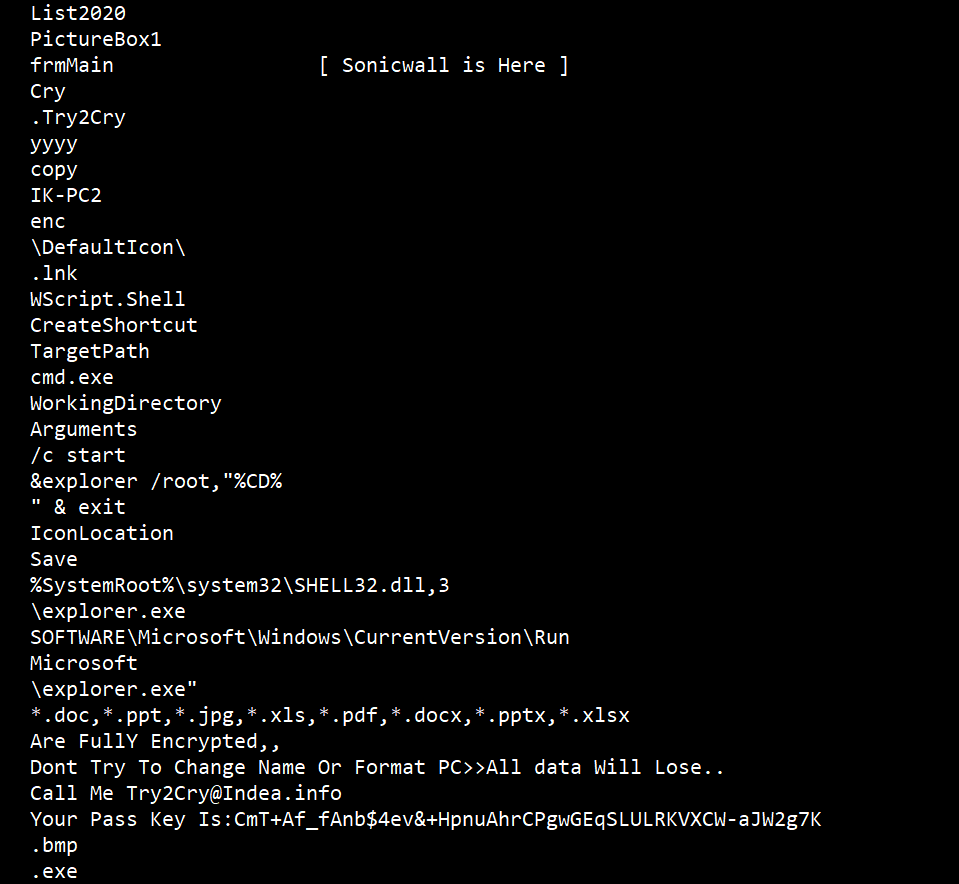
The ransomware adds the following files to the system:
- Malware.exe
- %App.path%\ [Name]. < .Try2Cry >
- %App.path%\ [Name]. < .txt > recovery instruction
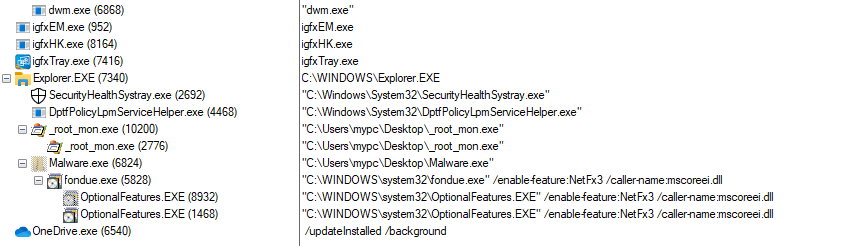
Once the computer is compromised, the ransomware runs the following commands:
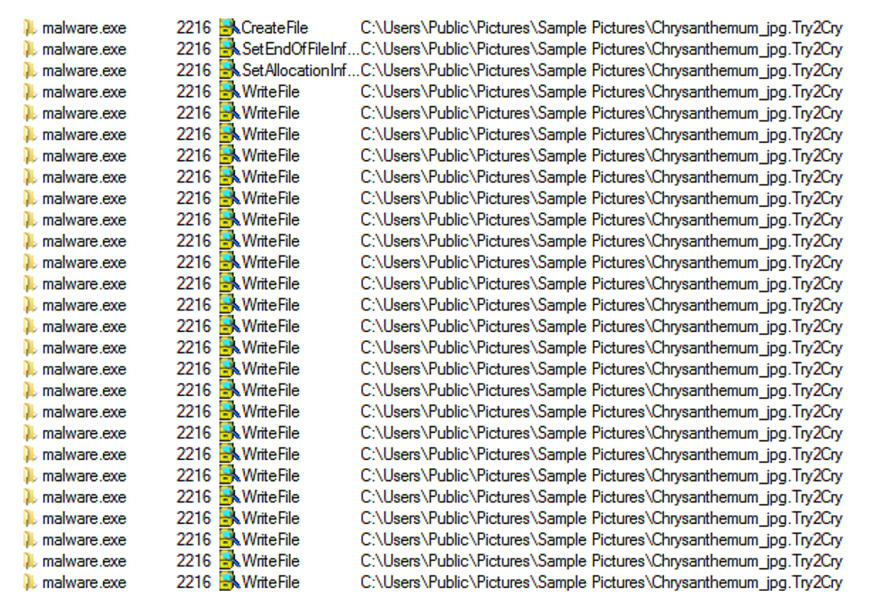
The ransomware encrypts all the files with following extensions and appends the [Try2Cry] extension onto each encrypted file’s filename.
*.doc,*.ppt,*.jpg,*.xls,*.pdf,*.docx,*.pptx,*.xlsx
During our analysis, we have noticed the malware using a packer called DNSgaurd to avoid detection by sandboxes in the wild.
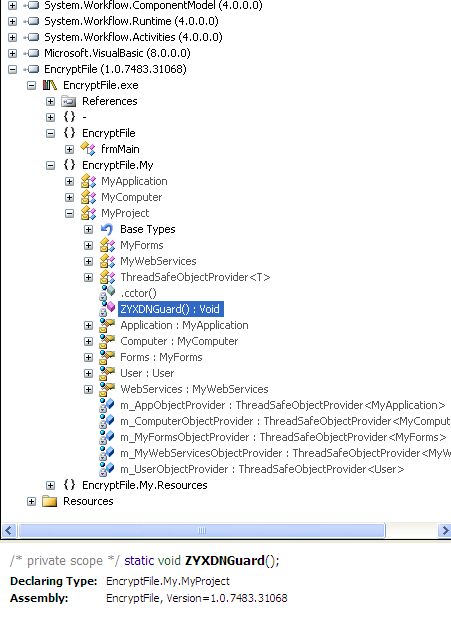
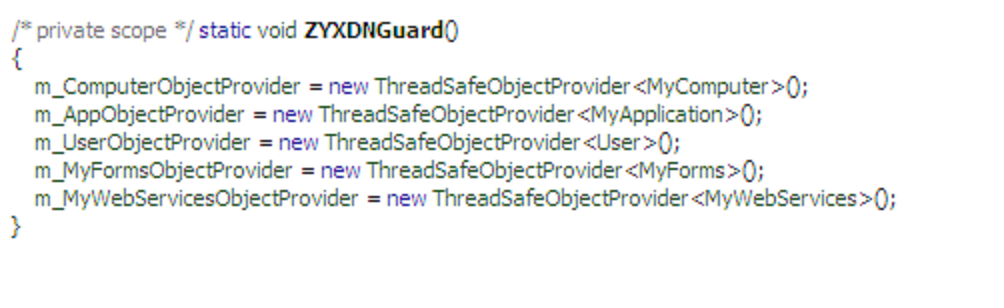
This makes our jobs harder to create a Decryptor tool for this ransomware.
However with some dynamic techniques we were able to inject our tool into the ransomware process and extract some valuable data that proves this is a ransomware.
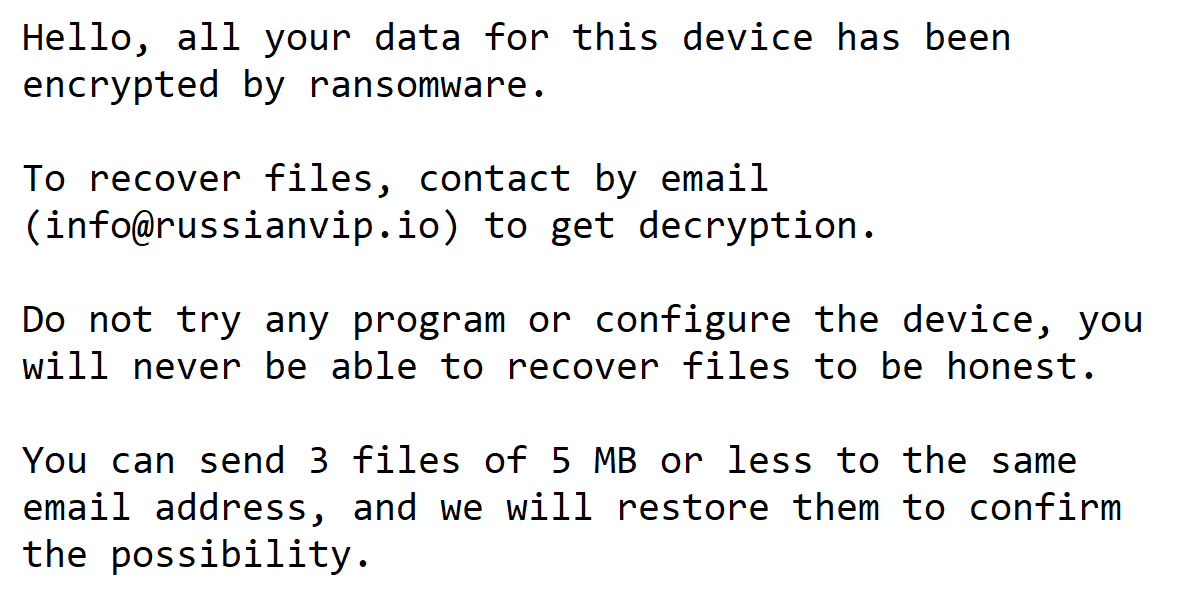
After encrypting all personal documents, the ransomware shows the following picture containing a message reporting that the computer has been encrypted and to contact its developer for unlock instructions.

Translated to English:
We have been monitoring varying hits over the past few days for the signature that blocks this threat:
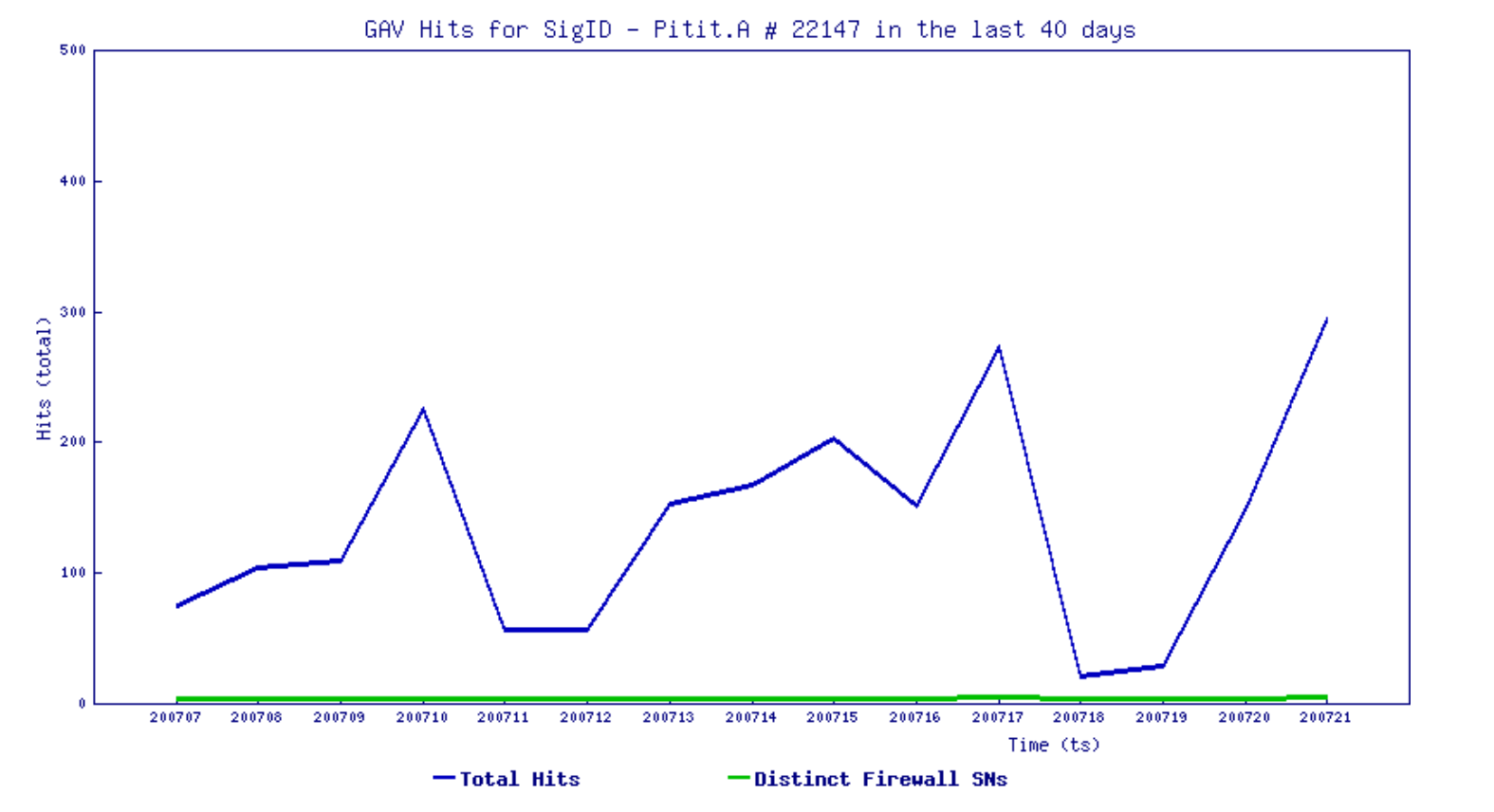
SonicWall Capture Labs threat research team provides protection against this threat via the following signatures:
- GAV: REHA.RSM (Trojan)
- GAV: Invader.H_176 (Trojan)
- GAV: Pitit.A (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.