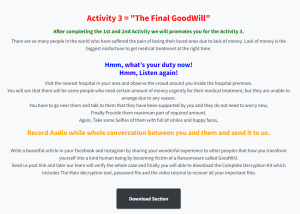
Ransomware not asking for payment but asks the victim to help the needy
This week the Sonicwall Capture Labs Research team analyzed a ransomware sample that is rather unconventional. After encrypting the victim’s files, it does not demand payment but rather asks the victim to carry out certain tasks and submit a video and photo as proof and to post to social media the whole experience.
Infection cycle:
This ransomware arrives as a typical windows executable using the following icons and file properties.
![]()
Once execution, it spawns cmd exe to carry out most of its functionality.
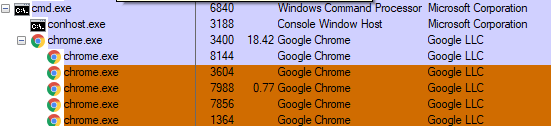
It creates a hidden directory and drops all the related files in the /Users/Public/Windows/Ui folder.
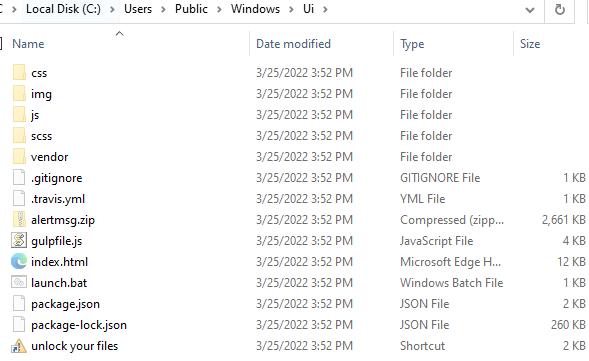
Upon successful encryption of targeted files, it runs the batch file named “launch.bat” which launches the chrome browser in incognito mode which displays an html file with details on what to do to get your files back.
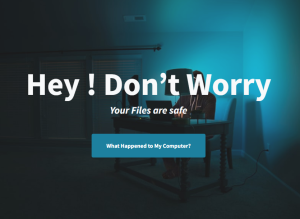
It is a rather long list of demands and the following screenshots show the entire html page as you scroll down the instructions on how to retrieve your encrypted files.
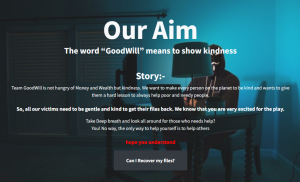
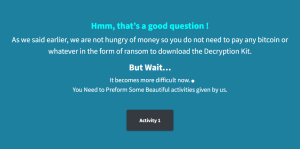
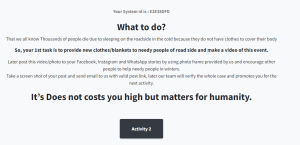
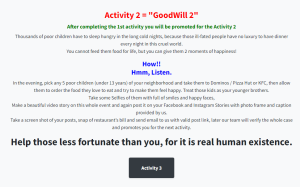
Traditional ransomware will encrypt the victim’s data and demand a ransom, typically in cryptocurrency, in exchange for decrypting the files. But Goodwill Ransomware asks the victims to carry out tasks to help the community and show kindness. Victims need to complete three tasks – provide clothes to the homeless, feed hungry children and pay for the hospital bill of someone in need, all while documenting the events in a form of videos and photos. Upon completing all three tasks, it also wants the victim to post the experience on their social media accounts.
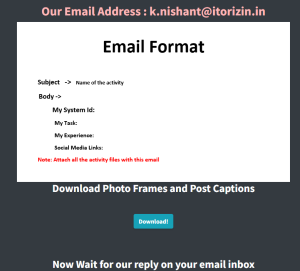
Interestingly, it asks the victim to send the video, photos and link to social media post to an email address with “itorizin.in” domain. Itorizin appears to be a security company based in India and the affiliation to this ransomware is unclear.
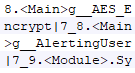
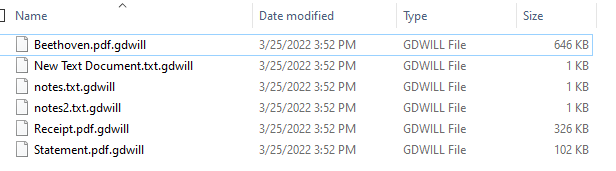
This ransomware uses aes encryption and only encrypts pdf and txt files.
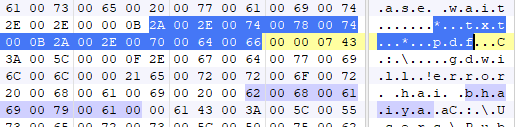
Encrypted files will have the .gdwill file extension.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV:Goodwill.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.