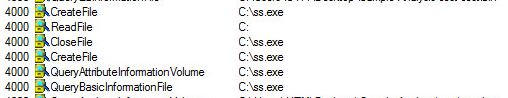Project "Androm" Backdoor Trojan
Overview:
SonicWall Capture Labs Threat Research Team analyzed a new sample found in (Feb. 2020) for a project named: “Androm” a backdoor Trojan. Trojans appear to contain benign or useful functionality, but also contain code paths that are hidden from normal operation that violate the intended security policies of the user or system administrator. The code paths may include embedded, non-replicating, and/or replicating code snippets. The technical impact, would be to execute unauthorized code or commands on the victims machine.
Sample Static Information:
As we look through the PE File format. We are searching for corrupted data. Corruption from a memory dump will be highlighted in red. The GIF below verifies the no red policy. This tells us we have a complete sample for analysis. This should theoretically make analysis easier. Depending on if its packed, protected, encrypted or armed. We know one thing is true, we will not have to rebuild a memory dumped file and this is great news:
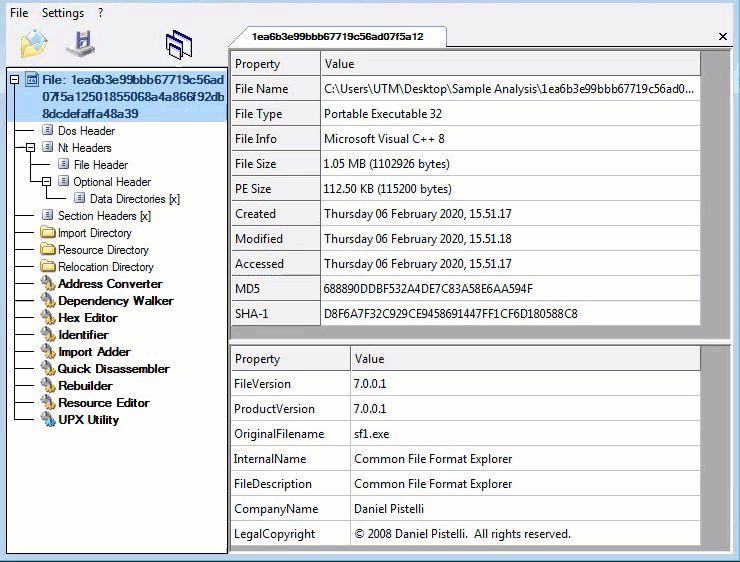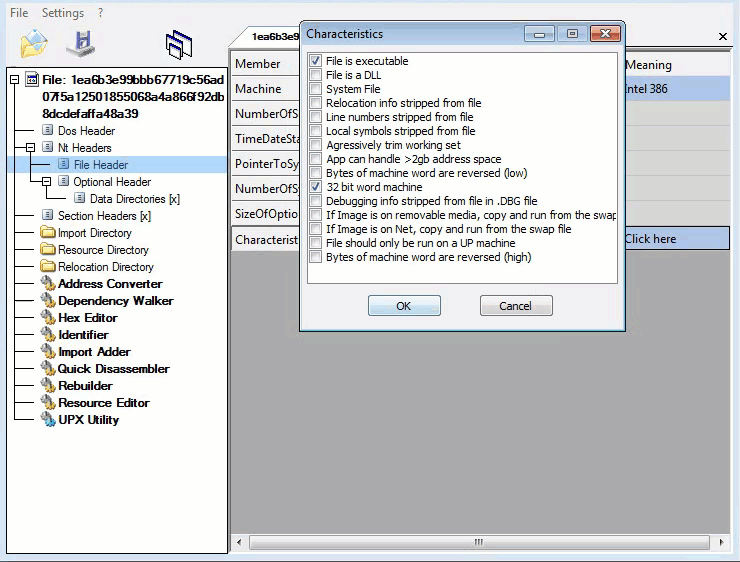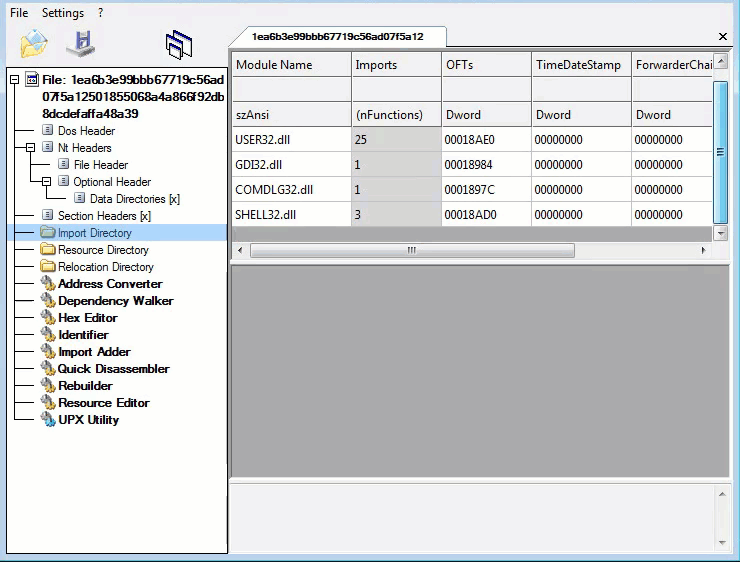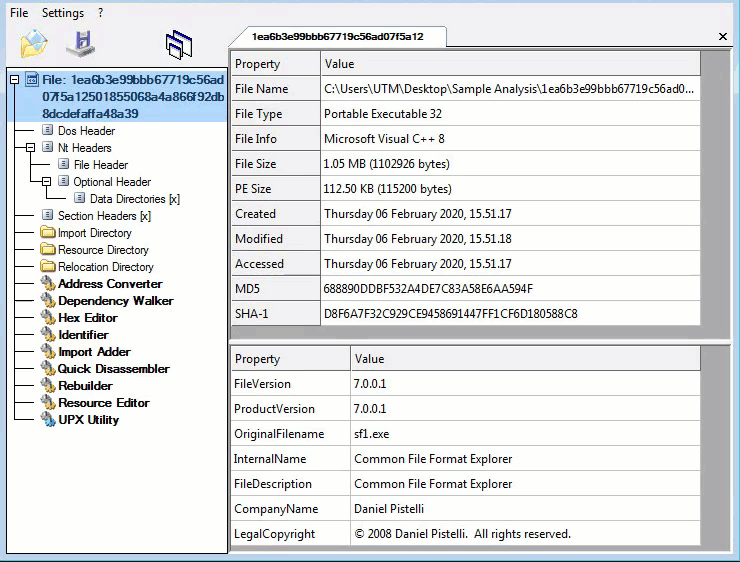
Metadata:
A Look Into The Samples Starting Routine:
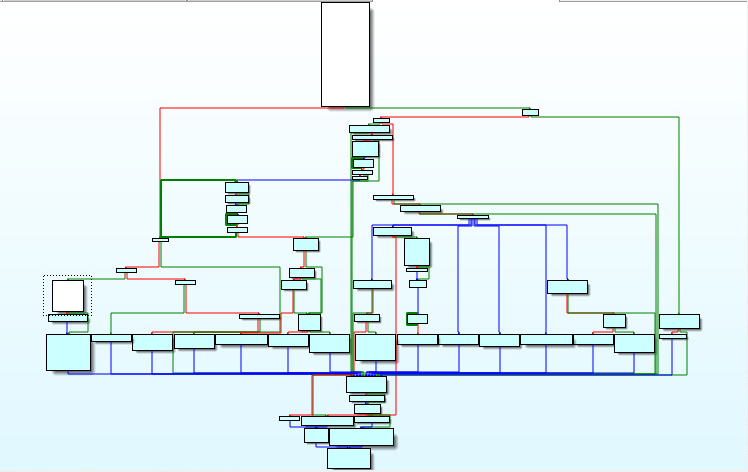
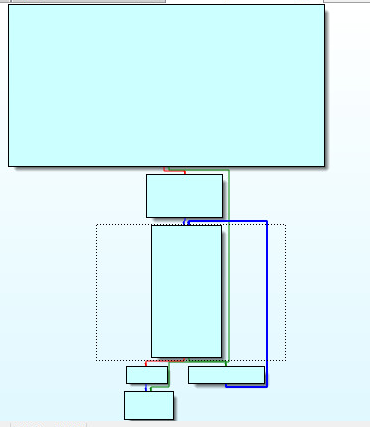
Windows GUI applications need to register a windows class before creating a graphical window. This is completed by the use of the RegisterClassExA windows API. This function uses a structure called WNDCLASSEXA to accomplish this. There are twelve members inside WNDCLASSEXA, one is ultra important. The member (WNDPROC lpfnWndProc) is the heart of any Windows GUI application. The windows procedure processes messages sent to a window. Here we can see the code path of the Windows Procedure:
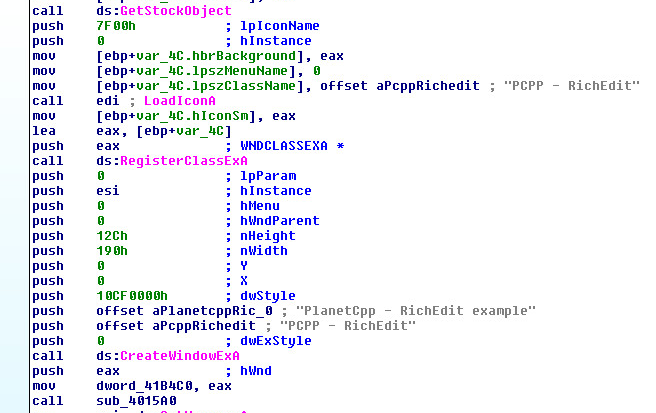
As we open the sample for the first time in Ida Pro, we clearly see normal operation of the application such as LoadIconA, RegisterClassExA, CreateWindowExA and reference to “PlanetCpp – RichEdit example strings”:
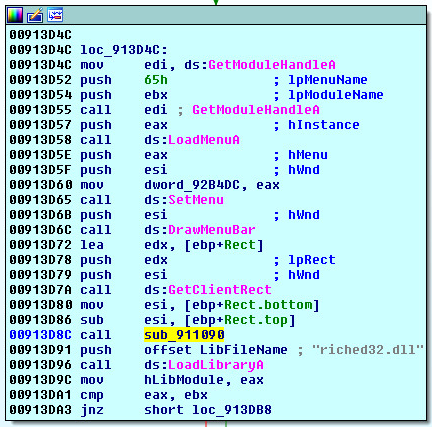
The hardest part of analyzing any Trojan is finding the hidden (Call or Pointer) to the malware code. We can see this call here (sub_911090). Looking up at the window procedures picture above. We can see the location of this call within the WNDPROC code path in (white) on the left of the picture above:
Encryption & Decryption Routines:
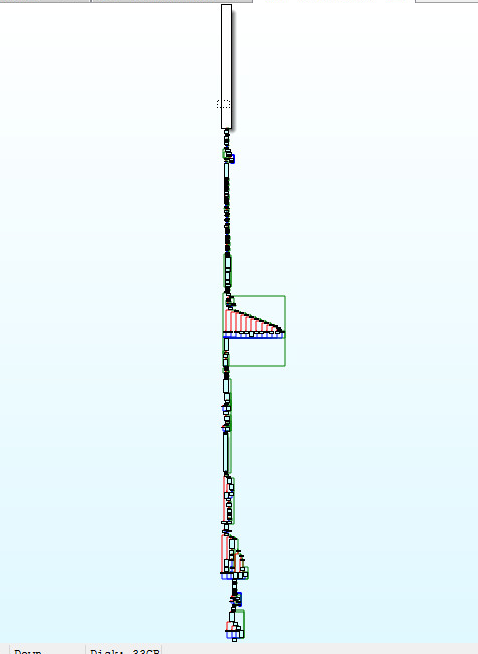
After stepping through the application and setting your favorite breakpoints you will arrive to an encrypted code cave:
The code caves instructions will cycle through the decryption loop, its only one while loop. However, its nested deep inside the sample:
The largest section of the decryption logic places many xor and shift operations on the encrypted code cave to decode the encrypted buffers data:
Once the data has been decrypted, you will see the following decoded code cave:
Malware Logic:
Stepping into the code caves buffer and following the logic. You will see the following instructions:
The instructions above, show the starting area of the malware architects logic. We can see the whole payload here:
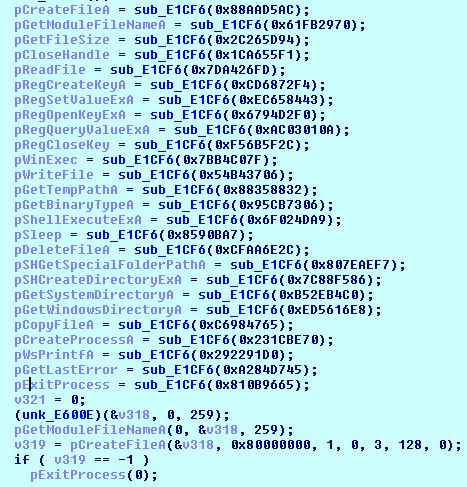
The first few calls will find each Windows API by Hash:
API Hashes:
There are currently 104 Windows API Hashes that are needed to understand the Malware’s logic above:
HASH DESCRIPTION
——————————————–
0x7BB4C07F WinExec
0x3867269F Wow64DisableWow64FsRedirection
0x7DD9B6D8 Wow64RevertWow64FsRedirection
0x13398F97 IsWow64Process
0x887753C1 GetCurrentProcess
0x18AE55D2 GlobalAlloc
0x8B8A0B81 GlobalReAlloc
0xC962E0DD GlobalFree
0x533FF50C GetFileAttributesA
0x3B9403BF MultiByteToWideChar
0x88AAD5AC CreateFileA
0x7DA426FD ReadFile
0x54B43706 WriteFile
0x2C265D94 GetFileSize
0x1CA655F1 CloseHandle
0x61FB2970 GetModuleFileNameA
0x231CBE70 CreateProcessA
0x540559D3 ReadProcessMemory
0xD485A88C WriteProcessMemory
0x7C03517B VirtualAllocEx
0x9E5A8833 VirtualAlloc
0x4FAEF192 VirtualFree
0x659005B0 GetThreadContext
0xE59005B2 SetThreadContext
0xAAF2FD77 ResumeThread
0x8590BA7 Sleep
0x759DF562 TerminateProcess
0xFD0B55A7 OpenProcess
0xF88DDF46 CreateToolHelp32SnapShot
0x3F347695 Process32First
0x93E12339 Process32Next
0x810B9665 ExitProcess
0x243CB902 GetTickCount
0xD6D48E5A CreateThread
0xB430264A GetCurrentDirectoryA
0x850A2076 VirtualAllocExNuma
0xA0568251 IsDebuggerPresent
0x44155EB6 OutputDebugStringA
0x44155ECC OutputDebugStringW
0x3467D7DA CheckRemoteDebuggerPresent
0xE5360DD3 GetCurrentThread
0x659005B0 GetThreadContext
0xD3C98A82 GetVersionExA
0xCFAA6E2C DeleteFileA
0xCFAA6E42 DeleteFileW
0xC6984765 CopyFileA
0x9016C35B GetUserDefaultUiLanguage
0xDD3D54EE GetSystemInfo
0x4A6A0E7 GlobalMemoryStatus
0xF63D4C20 GetDriveTypeA
0x112A6907 GetLogicalDrives
0x485D688D GetDiskFreeSpaceA
0xC34F9FC1 FileTimeToLocalFileTime
0x6C9A05ED FileTimeToSystemTime
0x89EEB6C5 SystemTimeToFileTime
0xC6DFD663 CompareFileTime
0x263546AE GetLocalTime
0x2DBE5D94 GetFileTime
0x930E608E GetComputerNameA
0xCA8E9498 WaitForSingleObject
0x6F45D8C8 CreateRemoteThread
0xB52EB4C0 GetSystemDirectoryA
0xB52EB4D6 GetSystemDirectoryW
0xED5616E8 GetWindowsDirectoryA
0x88358832 GetTempPathA
0x95CB7306 GetBinaryTypeA
0x83259FD6 GetStartupInfoA
0x5B8D5E53 CreateMutexA
0xC964A8DD LocalFree
0xA284D745 GetLastError
0x46218786 NtUnmapViewOfSection
0xE110E5ED NtQueryIntoProcess
0xCC926BD FindWindowA
0x9E8D13D2 CharUpperA
0x292291D0 WsPrintfA
0x7D9D5BE1 GetWindowThreadProcessId
0x6794D2F0 RegOpenKeyExA
0xF56B5F2C RegCloseKey
0xAC03010A RegQueryValueExA
0xCD6872F4 RegCreateKeyA
0xEC658443 RegSetValueExA
0x659084F0 RegEnumKeyExA
0x6457C825 RegDeleteValueA
0x3BDD8993 GetUserNameA
0x8A9044D OpenProcessToken
0x8B03CAA1 GetTokenInfo
0xFC759D60 ConvertStringSecurityDescriptorToSecurityDescriptorA
0x807EAEF7 SHGetSpecialFolderPathA
0x6F024DA9 ShellExecuteExA
0x3CBE3BD0 SHCreateItemFromParsingName
0x7C88F586 SHCreateDirectoryExA
0x5923AEC4 CoInitialize
0x3ADA792E CoCreateInstance
0x4CE5ED53 CoGetObject
0x3AC7B3B4 CoUninitialize
0xD0488B42 GetAdaptersAddresses
0xE3C6DAB4 InternetOpenA
0x9A280099 InternetConnectA
0x73FA8F2B HttpOpenRequestA
0x2C244C89 InternetCloseHandle
0x81716702 InternetCrackUrlA
0x1BBF63F7 InternetReadFile
0xAA02D728 HttpSendRequestA
0x870EDA86 HttpQueryInfoA
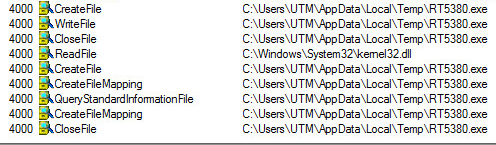
Files Executed:
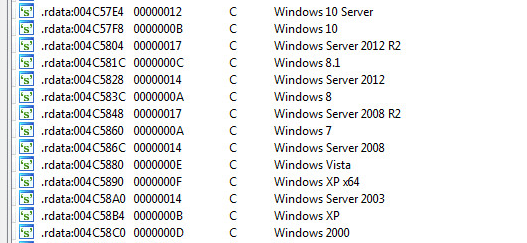
Systems Supported By This Trojan:
Summary:
Lets turn back to the APIs listed above and pick out a few to talk about and see if we can understand a summary of what this sample is doing:
WinExec, CreateFileA, CreateProcessA, DeleteFileA, DeleteFileW, CopyFileA, GetDriveTypeA, GetLogicalDrives, GetComputerNameA, RegCreateKeyA, GetUserNameA, ShellExecuteExA,
SHCreateDirectoryExA, InternetConnectA, HttpSendRequestA
The sample can execute pre-programmed commands with (WinExec & ShellExecuteExA), Create new processes with (CreateProcessA), Create and Read files with (CreateFileA), Delete files, Copy files, Get Hard Drive Information, The Computer Name, The User Name, Create and Delete Directories, Add and Edit Registry Keys, and Send, Receive requests and responses over the wire.
The processes it drops and executes provides the malware components to be modular in design. Such as the key-logging and remote viewing capabilities.
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Androm.H_2 (Trojan)
Appendix
Sample Hash: 1ea6b3e99bbb67719c56ad07f5a12501855068a4a866f92db8dcdefaffa48a39