phpIPAM SQL Injection Vulnerability
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
phpIPAM is a free and open-source web-based IP address management (IPAM) software application. It is designed to help organizations efficiently manage their IP addresses and network infrastructure. The software is built using PHP and a MySQL database and can be accessed through any modern web browser.
With phpIPAM, users can create, manage and organize IP address spaces, subnets, VLANs, and devices. It also provides features such as IP address tracking, advanced search options, and a comprehensive API for integration with other systems. Additionally, phpIPAM offers advanced features like LDAP and Active Directory integration, IPv6 support, VLAN management, and SNMP integration.
This vulnerability allows authenticated admins to perform SQL injection. A successful attack may result from the selection of entire tables and, in certain cases, the attacker gaining administrative rights to a database, writing files to the server leading to Remote Code Execution, XXS Stored, or writing a script to extract data.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-1211.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 7.2 (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 7.2(AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is high.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 6.5 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
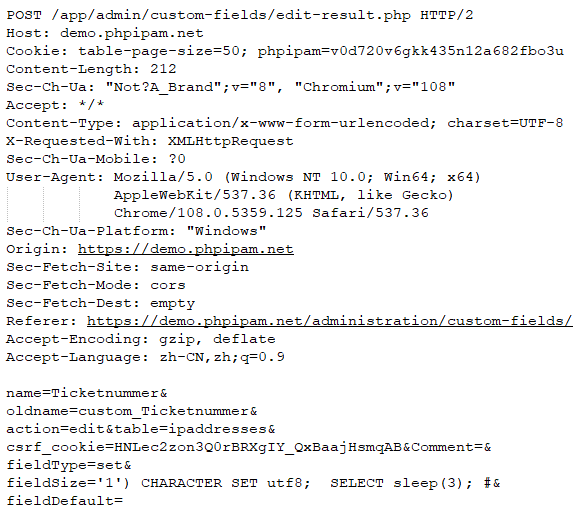
SQL injection is a common vulnerability in web applications that allows attackers to execute arbitrary SQL commands on the server. One such instance is when updating custom fields in the admin panel. Malicious web admins can exploit this vulnerability by using the POST method with the /app/admin/custom-fields/edit-result.php endpoint and passing parameters such as fieldType and fieldSize. By inserting SQL commands into these parameters, the attacker can execute them on the server.
In the example below, the attacker uses the SELECT sleep(3); command to delay the server response by 3 seconds. This may seem like a harmless attack, but attackers can use this technique to cause more serious damage. For instance, they can inject arbitrary SQL commands or even operating system commands using the system command in SQL. This can allow the attacker to gain access to sensitive data, modify or delete data, or even take control of the entire server.
To prevent SQL injection attacks, web developers must take appropriate measures such as validating user input, using prepared statements or parameterized queries, and implementing strict input sanitization. In addition, web admins should regularly update their web application frameworks, libraries, and plugins to ensure they are using the latest security patches. Properly securing web applications is critical to protecting sensitive data and ensuring the integrity of the entire system.
Triggering the Problem:
• The attacker must have network access to the target server.
• The target must be running a vulnerable version of the software.
• The target server must have admin privileges.
Triggering Conditions:
The attacker sends a POST Request with a malicious “fieldSize” parameter. The vulnerability is triggered when the server processes the request. This vulnerability allows authenticated admins to perform SQL injection.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• SSL/TLS (HTTPS)
Example POST Request Packet:
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 18920 PhpIPAM SQL Injection 2
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor supplied patch.
• Detecting and blocking malicious traffic using the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory





