Payola ransomware operator demands remote access to PC
The Sonicwall threat research team have recently been tracking a new ransomware family called Payola. This family of ransomware appeared in late August 2023. It is written in .NET and is easy to analyze as it contains no obfuscation. Early variants would append ".Payola" to the names of encrypted files but the current variants use 5 random alphanumeric characters. During a direct conversation with the malware operator, remote access to our system was requested in order to retrieve files.
Infection Cycle:
The malware uses the following icon:

Upon execution, the following message is shown on the desktop background:
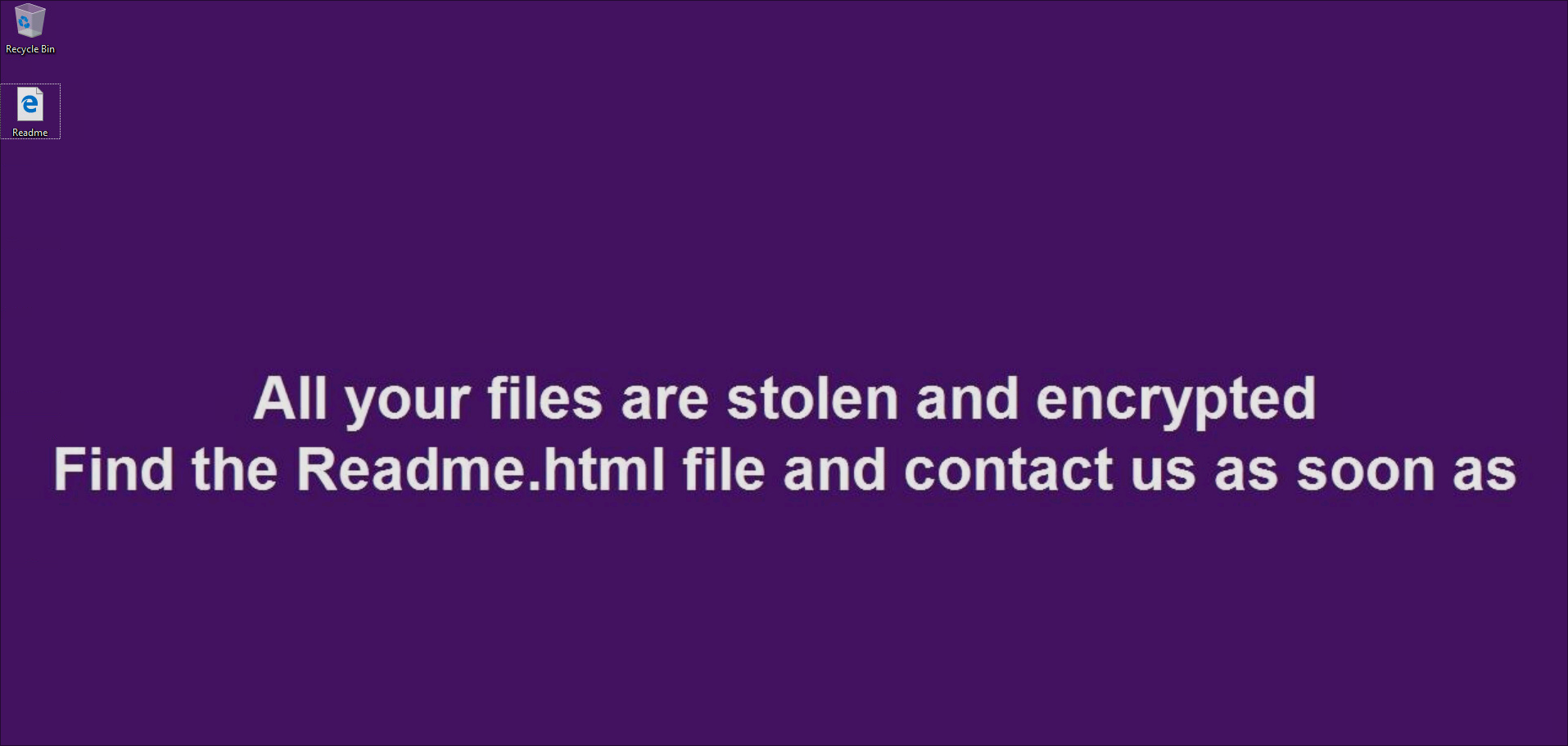
Files on the system are encrypted. Each encrypted file is given a 5 character alphanumeric extension appended to its name eg. image.jpg.PTebc.
The following registry entry is made:
- HKCU\Microsoft\Windows\CurrentVersion\Run Readme {run location}
A file named README.html is dropped into directories where files where encrypted. It contains the following message:
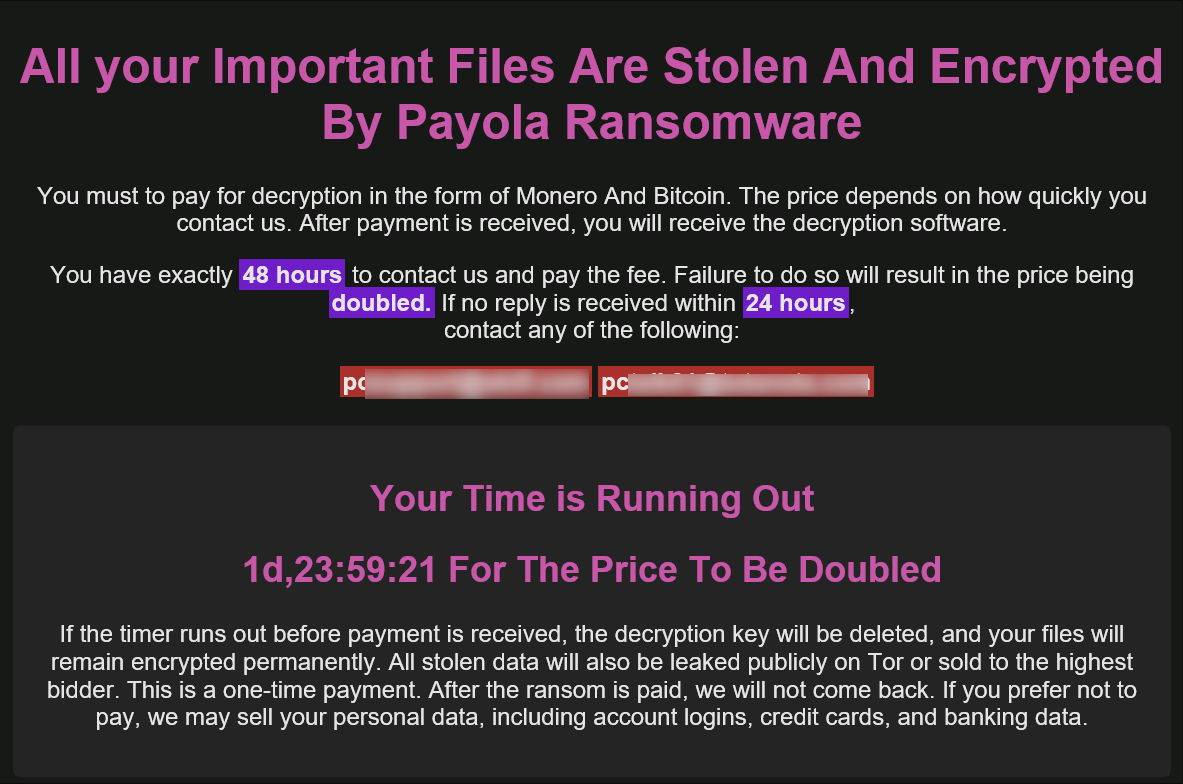
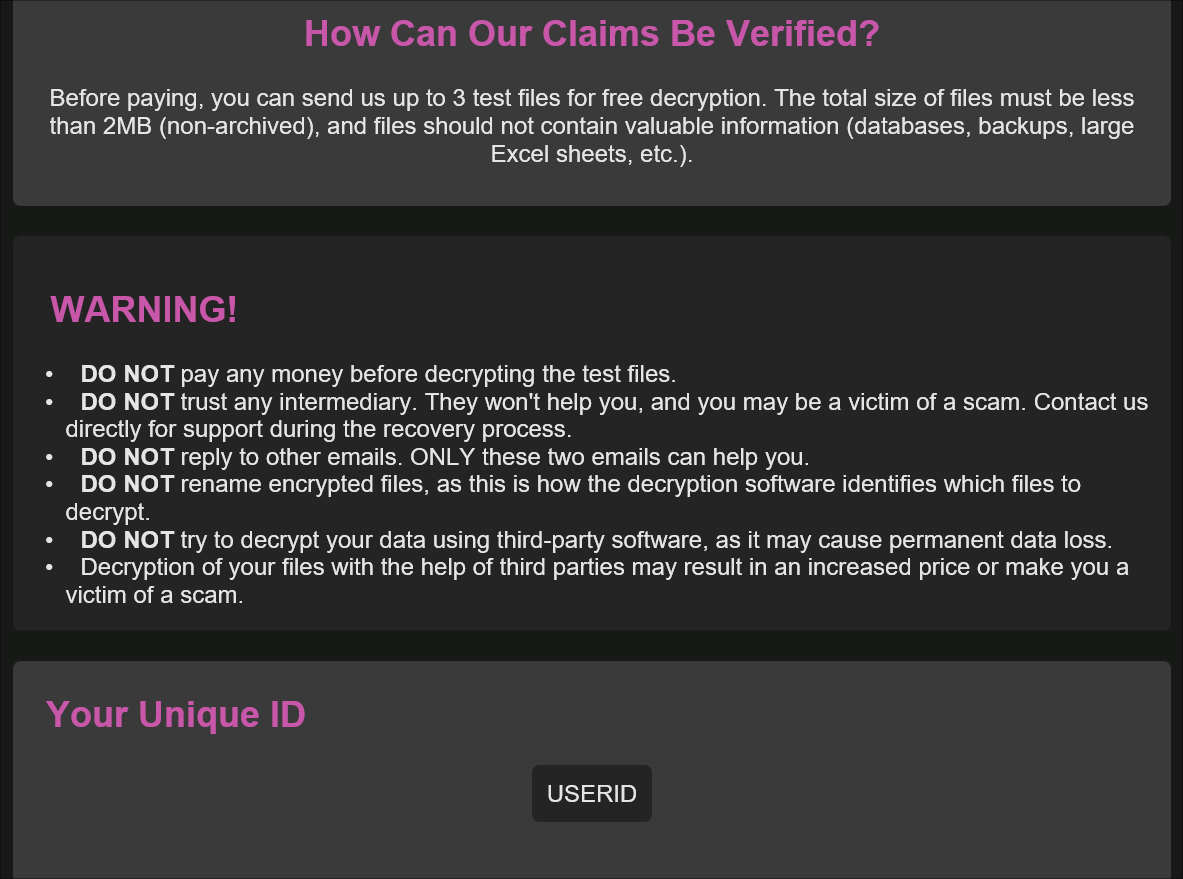
The code is written in .NET and is trivial to decompile. We can easily see its main function and the intended program flow:
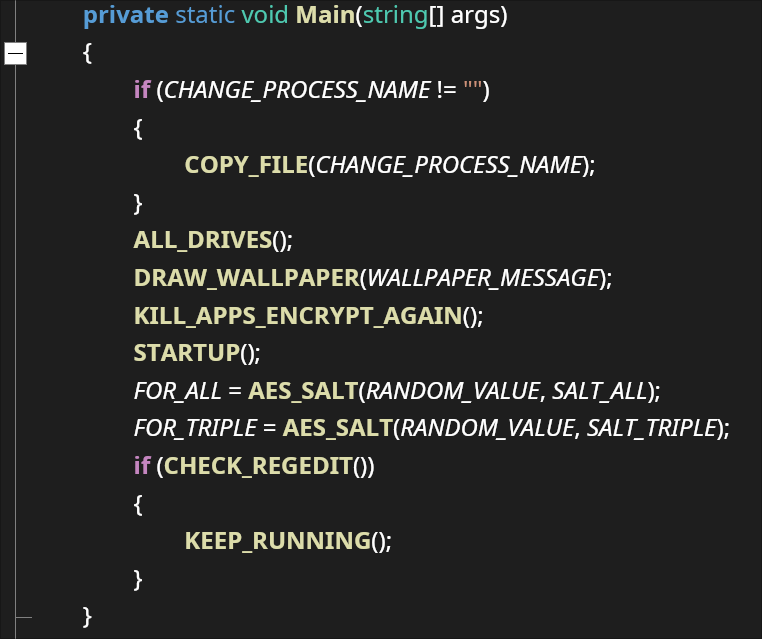
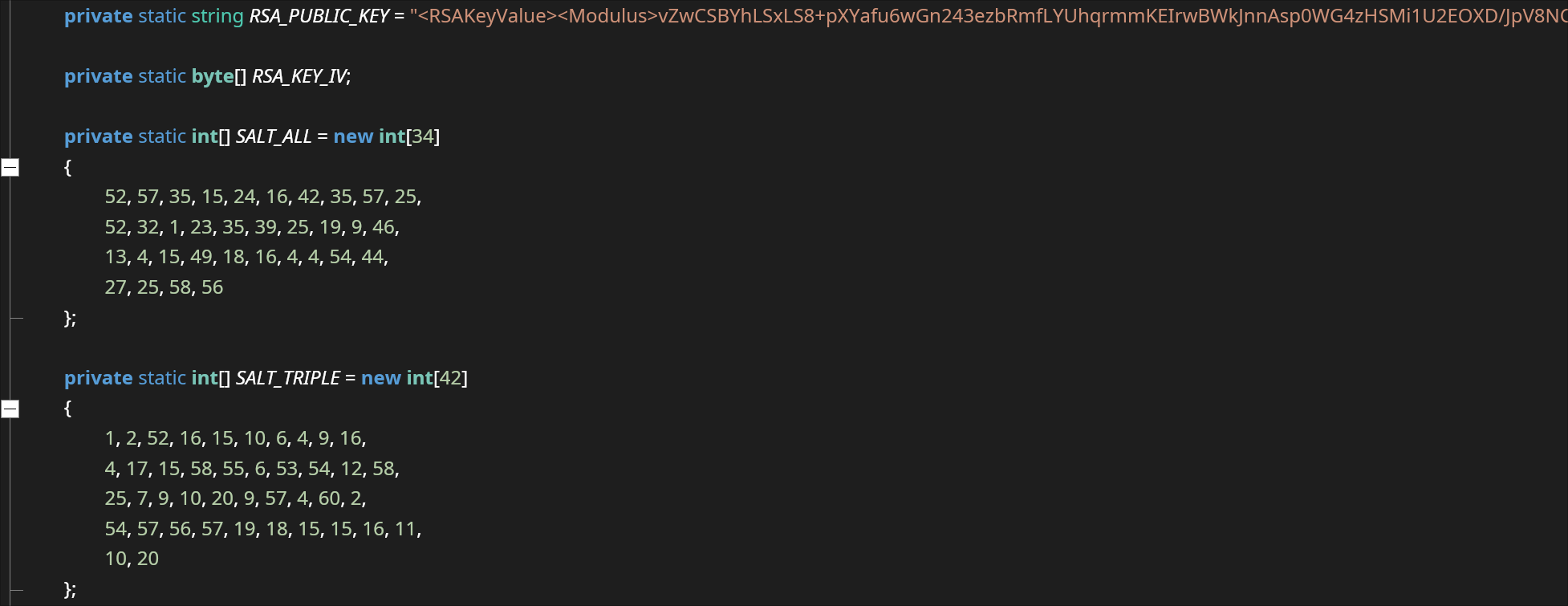
The RSA public key and salt values can be seen:
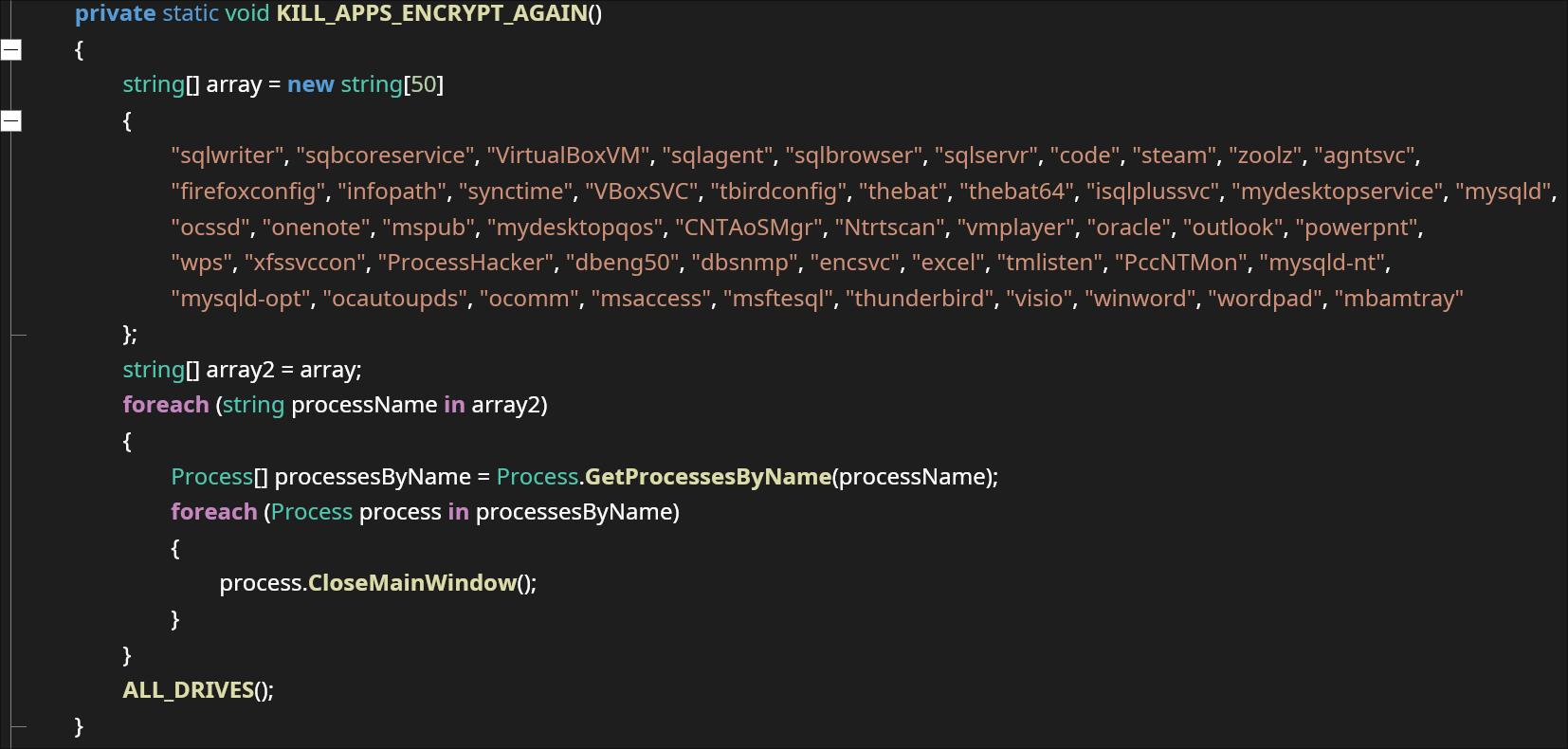
The malware contains a list of programs that will be killed if running:
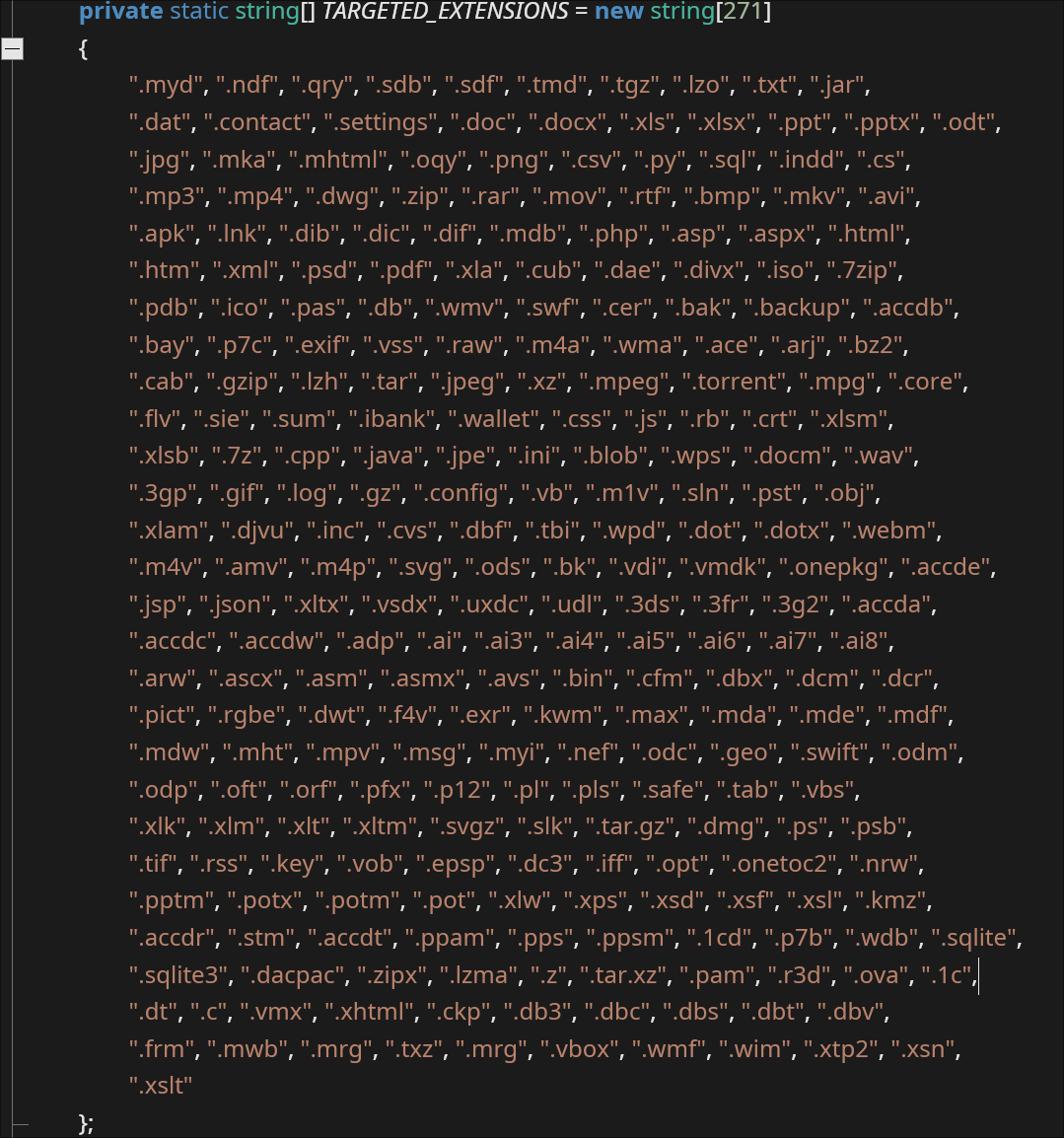
A list of targeted directories and file types are listed in the code:

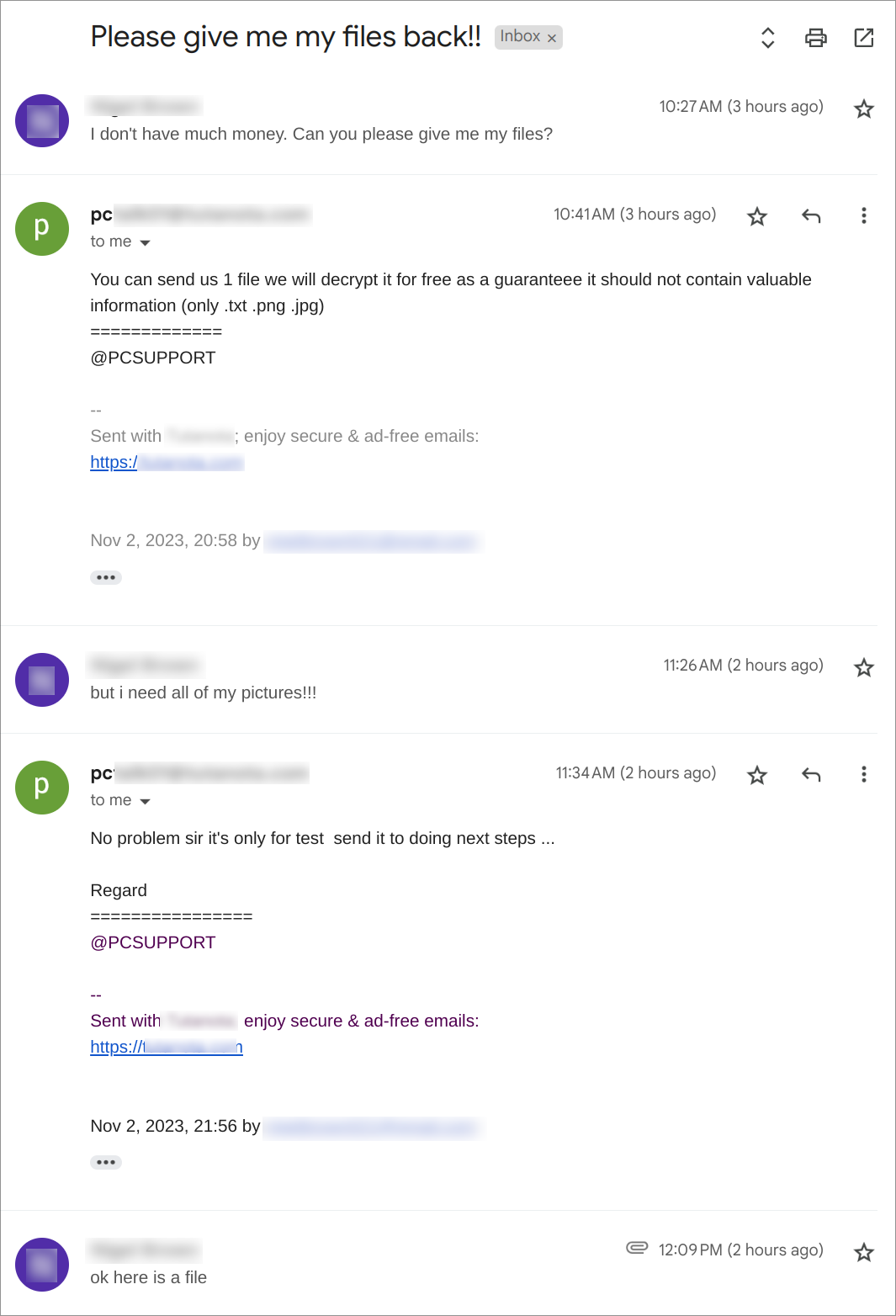
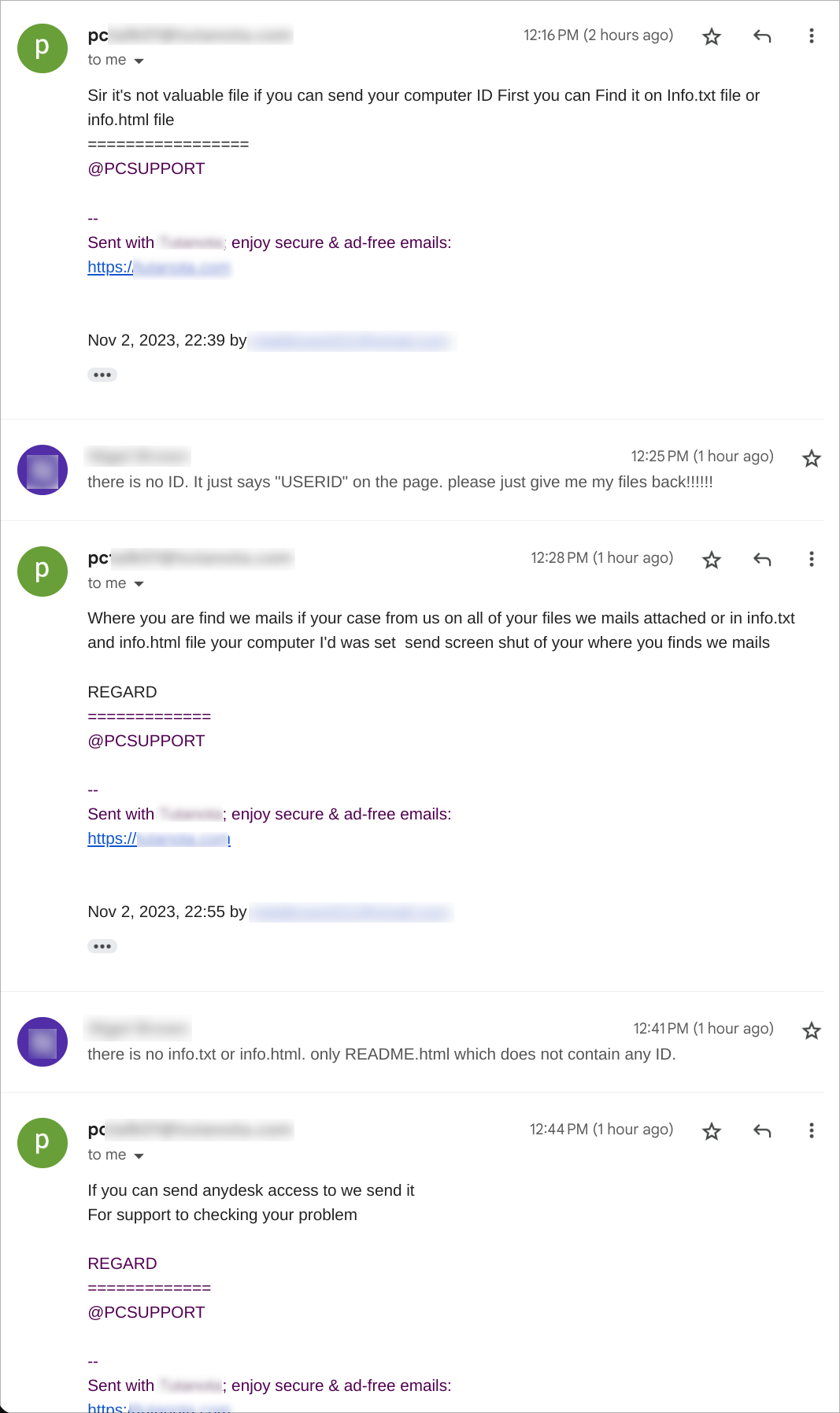
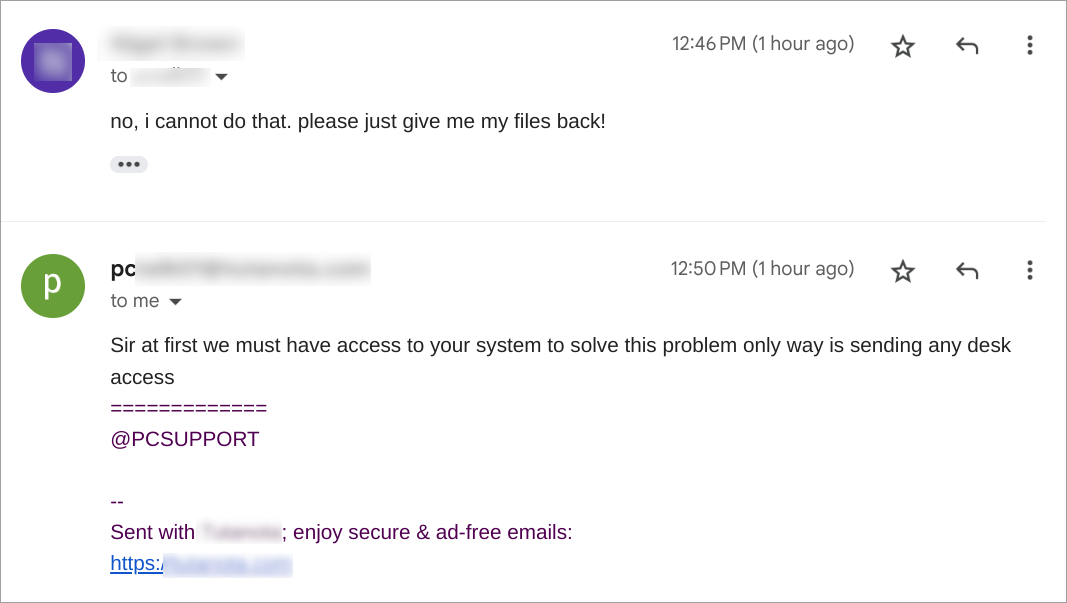
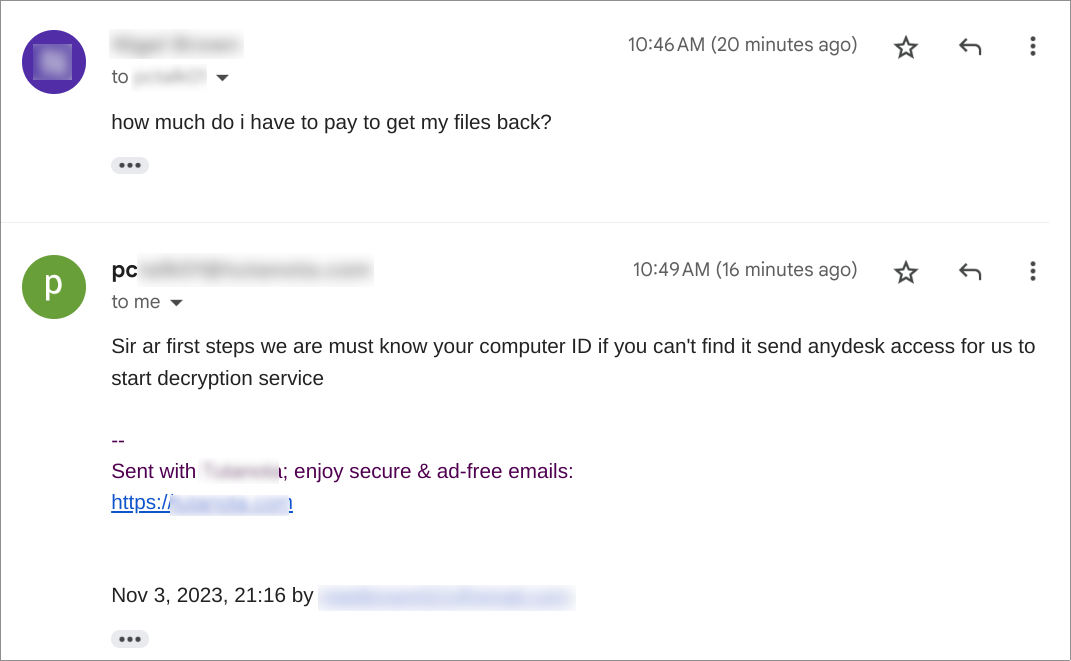
We followed the instructions in the ransom note and got in touch with the operator. We had the following conversation via email where the operator demanded remote access to our system using Anydesk:
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: Payola.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.



