Parse Server DatabaseController RCE Vulnerability
Overview:
Parse platform, provides SDKs for various environments (Android, iOS, PHP, .NET, …) as well as managed cloud data storage. When creating mobile apps a lot of the development time goes into managing and scaling the data backend, and building out user authentication, push notifications, and/or social media integration. Parse SDKs and cloud storage allow mobile app developers to quickly build functionality and focus efforts on user facing features.
Parse Server is an open source backend that can be deployed to any infrastructure that can run Node.js:
• Parse Server uses MongoDB or PostgreSQL as a database.
• You can deploy and run Parse Server on your own infrastructure.
• You can develop and test your app locally using Node.
A prototype pollution vulnerability has been reported in Parse Server. This vulnerability is due to improper input validation for the DatabaseController.
A remote, unauthorized attacker could exploit this vulnerability by sending a crafted request to the target server. Successfully exploiting this vulnerability could result, in the worst case, in remote code execution.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-24760.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.7 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 10.0 (AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is changed.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.7 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
A remote unauthenticated attacker uses this exploit to inject properties in Object.prototype, or modify existing ones. Successful exploitation could result in; denial of service as the software encounters objects with unexpected properties, or properties with unexpected values. In the worst case it could lead to the execution of arbitrary code on the target server.
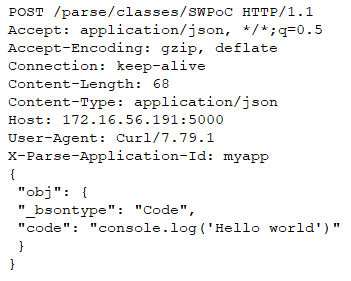
An attacker could for instance leverage the prototype pollution vulnerability to unlock a code path in the Node.js BSON module which evaluates arbitrary Javascript code. MongoDB uses the BSON format for storing data internally, and over the network. The name “BSON” is based on the term JSON and stands for “Binary JSON”. It is a binary form for representing simple or complex data structures, including associative arrays (also known as name-value pairs), integer indexed arrays, and a suite of fundamental scalar types. The BSON format also includes a Code data type to store Javascript code. You can store such an object in Parse Server by sending the following HTTP request:
When the object is later retrieved from Parse Server via an HTTP GET request, it is deserialize by the function deserializeObject() in lib/bson/parser/deserializer.js from Node.js BSON module. When encountering a Code data type the function takes one of two code paths, depending on the value of the boolean options[‘evalFunctions’]. By default this property is undefined and the function returns a string containing the Javascript code; however if options[‘evalFunctions’] is true, the function evaluates the Javascript code and return its result. By polluting Parse Server and injecting the property Object.prototype.evalFunctions an attacker may unlock the second code path and gain code execution on the server.
Triggering the Problem:
• The target system must have the vulnerable product installed and running.
• The attacker must have network connectivity to the affected ports.
Triggering Conditions:
The attacker first stores a crafted object in the target server. The attacker then updates the object using an update operator. The vulnerability is triggered when the target server processes the update request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2653 Parse Server Prototype Pollution RCE
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Blocking the affected ports from external network access if they are not required.
• Filtering traffic based on the signature above.
• Upgrading the product to a non-vulnerable version.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory