Oracle MySQL NDB Cluster RCE
Overview:
SonicWall Capture Labs Threat Research Team has observed the following threat:
MySQL is a popular open-source implementation of a relational database that supports the Structured Query Language (SQL) for querying and updating stored data. Communication with the database occurs using the MySQL protocol. As with other database implementations, MySQL supports a number of database storage engines, such as the NDB storage engine.
An index boundary error has been reported in Oracle MySQL. The vulnerability exists in the MySQL NDB Cluster component when handling GSN_CREATE_NODEGROUP_IMPL_REQ signals.
A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted packet to the vulnerable server. Successful exploitation will allow an attacker to execute arbitrary code in the context of the application.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-21490.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.5 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.5 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
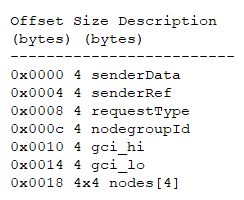
An index boundary error exists in Oracle NDB Cluster Data node. The vulnerability is due to improper validation when handling the incoming signals. More specifically, when the NDB Data node receives a GSN_CREATE_NODEGROUP_IMPL_REQ signal to the SUMA block, the function Suma::execCREATE_NODEGROUP_IMPL_REQ() is called to handle the signal. The vulnerable function will parse the signal data as the CreateNodegroupImplReq format:
The values in the nodes array will be used as indexes to refer to a NDB node object. However, this index value is not validated correctly. If the value is larger than or equal to MAX_NDB_NODES (145), the related memory operation will bypass the boundary of the object array and result in a memory corruption condition.
A remote, unauthenticated attacker can send a malicious GSN_CREATE_NODEGROUP_IMPL_REQ signal to result in the out of boundary read or write condition. Successful exploitation could possibly allow an attacker to execute arbitrary code in the context of the application. A failed weaponized exploit attempt will result in a denial-of-service condition.
Triggering the Problem:
• The target host must have a vulnerable version of the affected product installed and running.
• The attacker must have the means to deliver crafted packets to the target service.
Triggering Conditions:
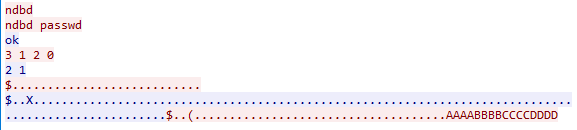
The attacker sends a GSN_CREATE_NODEGROUP_IMPL_REQ signal to the target server. The vulnerability is triggered when the server processes the malicious command.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• ndbd
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2997 MySQL Cluster Data Node RCE 4
Remediation Details:
The actions listed below may be taken in order to mitigate or eliminate the risks associated with this vulnerability:
• Restrict remote connections to trusted hosts only.
• Filter attack traffic using the signature above.
• Upgrade the vulnerable product to a non-vulnerable version.
The vendor released the following advisory regarding this vulnerability:
Vendor Advisory