Oracle Endeca Server RCE Vulnerability
Overview:
Oracle Endeca Server is a hybrid search-analytical database. It organizes complex and varied data from disparate source systems into a flexible data model that reduces the need for upfront modeling. Oracle Endeca Server is designed for discovery. Through its flexible data model, columnar storage, and in-memory analytics, it unifies search, navigation, and analytics to deliver fast answers on structured and unstructured data.
A command execution vulnerability exists in Oracle Endeca Server. The vulnerability is due to the controlSoapBinding web service exposing the createDataStore method which contains a flaw that allows for the injection of arbitrary commands.
A remote, unauthenticated attacker could exploit this vulnerability by sending a specially crafted request to the affected server. Successful exploitation could result in arbitrary command execution with elevated privileges.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2013-3763.
Common Vulnerability Scoring System (CVSS):
Base score is 10.0 (AV:N/AC:L/Au:N/C:C/I:C/A:C), based on the following metrics:
• Access vector is network.
• Access complexity is low.
• Level of authentication required is none.
• Impact of this vulnerability on data confidentiality is complete.
• Impact of this vulnerability on data integrity is complete.
• Impact of this vulnerability on data availability is complete.
Temporal score is 8.3 (E:F/RL:OF/RC:C), based on the following metrics:
• The exploitability level of this vulnerability is functional.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
Oracle Endeca Server uses commands to manage the database. The command-line interface executes commands in a remote system by sending a SOAP request. SOAP (Simple Object Access Protocol) is a specification for exchanging information with web services. Messages are sent over HTTP using a POST request using XML (eXtensible Markup Language) to structure the data.
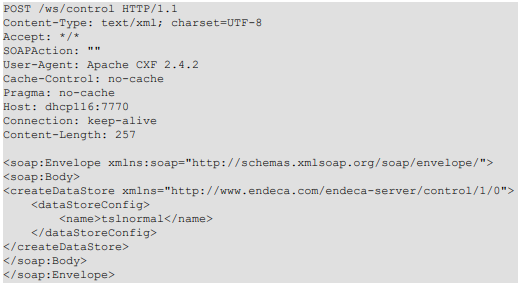
A typical request sent to the SOAP interface will have the following structure:
A command execution vulnerability exists in Oracle Endeca Server. The vulnerability is due to insufficient validation of SOAP requests sent to the target server. When the vulnerable web application, endeca-server-7.4.war, receives a request to createDataStore function from the user, it uses the value of the dataStoreConfig tag as the parameters to pass to external commands. Inside the dataStoreConfig tag, there may be a dataFiles tag, otherwise the server will use the value from the name tag to build a dataFiles variable. The web application will use this variable to build an external command. The parameters are not sanitized before they are used. If the value of the name or dataFiles includes a double quote character (") (encoded as quot or #34 or #x22) the vulnerable program interprets the double quote as a terminator character for a text string and will treat the rest of the parameter as a continuation of the command line. If the following string contains characters that serve as command line separators on the target operating system (such as ampersand “&”, pipe “|”, backtick “`”, a dollar-parenthesis sequence “$(“and a semicolon “;”), it is possible to inject a shell command and execute it on the target system.
By crafting a malicious request, a remote, un-authenticated attacker can exploit this vulnerability to execute arbitrary commands on the affected system. The executed commands will run in the security context of SYSTEM.
Triggering the Problem:
• The target host must have the vulnerable product installed.
• The attacker must have network connectivity to the Oracle Endeca Server.
Triggering Conditions:
The attacker sends a malicious request to the affected service on the vulnerable system. The crafted request to the createDataStore function contains a malicious name or dataFiles tag value. The vulnerability is triggered upon processing the malicious request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• SOAP/HTTP, over port 7770/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 4691 Oracle Endeca Server Remote Command Execution 2
Remediation Details:
Listed below are several actions, which may be taken in order to minimize or eliminate the risks posed:
• Limit network connectivity to the affected communication service to trusted users only.
• Detect and filter malicious traffic using the signature provided above.
• Apply the vendor-provided patch to eliminate the vulnerability.
The vendor, Oracle, has not issued a security advisory to address this vulnerability:
Vendor Advisory