Oracle E-Business Suite Infinite Loop Vulnerability
Overview:
Oracle E-Business Suite is a collection of applications for Enterprise Resource Planning (ERP), Customer Relationship Management (CRM), and Supply Chain Management (SCM) and contains several product lines intended for specific use cases. The E-Business suite utilizes Oracle’s Weblogic application server and Oracle database technologies and is generally operated using a combination of web interface and Java Web Start (JWS) applets executed on a client’s system. By default, the Oracle E-Business interface is accessible via HTTP on port 8000/TCP or HTTPS on port 4443/TCP.
An infinite loop vulnerability has been reported in the Sales Offline component of Oracle E-Business Suite. The vulnerability is due to improper handling of requests by the authentication component of Sales Offline.
An unauthenticated, remote attacker can exploit this vulnerability by sending a crafted request to the target server. Successful exploitation causes an infinite loop, consuming large amounts of CPU resources and possibly leading to denial of service conditions on the target server.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2021-2190.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 6.5 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H/E:U/RL:O/RC:C).
Base score is 7.5 (AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is none.
• Impact of this vulnerability on data integrity is none.
• Impact of this vulnerability on data availability is high.
Temporal score is 6.5 (E:U/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is unproven.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
One of the applications in the E-Business Suite is called Sales Offline, an additional module for the main sales application that leverages a Microsoft Excel document template with macros to allow users to work with and update Oracle sales data without the need to have a persistent connection to the Oracle E-Business instance. On current versions of the client the synchronization is primarily handled by Oracle Web Applications Desktop Integrator, a framework for synchronizing data between E-Business Suite applications and Excel. Synchronization with Sales Offline results in a request to the following URL:
/OA_HTML/BneUploaderService
The request will contain a reference to an “integrator” which tells the Desktop Integrator service which application will handle the upload and in turn will locate a Java class that implements the BneAbstractUploader interface for that application. The Java class that handles this for Sales Offline, AslUploader, builds and sends a request to aslUploadEngine.jsp to actually handle the updated data.
It is important to note that it appears as if legacy versions of the Sales Offline client would send requests directly to aslUploadEngine.jsp for synchronization and also would initially load “lookup” data from the server by sending a request to aslLookupDown.jsp. In current versions this data is already included in the downloaded template.
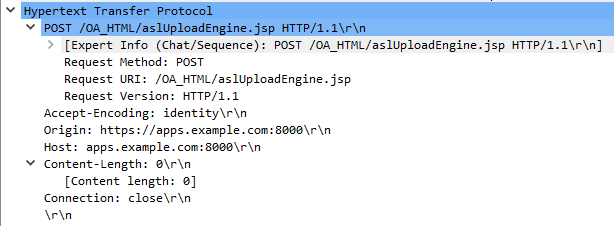
An infinite loop vulnerability exists in Oracle E-Business Suite. The vulnerability is due to improper handling of HTTP POST requests with a Content-Length request header value of 0. Ordinarily, when the aforementioned AslUploader class sends a request to aslUploadEngine.jsp, it sends an HTTP POST request with several request parameters in the query portion of the request-URI and places the file sent in the original request to BneUploaderService in the request body. This file, and therefore the request body to aslUploadEngine.jsp, is expected to contain a username, a password which is typically unused, a “Resp key”, and some synchronization preferences and each of these items is expected to be followed by a CRLF sequence (\x0d\x0a). These items in the request body are parsed by the included JSP file aslAuthincps.jsp which begins by attempting to first skip over any lines in the request body that only contain a CRLF to locate the username. This is performed by entering a loop which calls readLine() on the ServletInputStream object from the request and checking to see if the number of bytes read is fewer than three, exiting the loop when three bytes or more are read from a line in the request body.
However, aslAuthincps.jsp fails to check if the HTTP request body actually contains any data, the length of which should be specified in the Content-Length header. As a result, if an attacker sends an HTTP POST request to aslUploadEngine.jsp or aslLookupDown.jsp, which also includes aslAuthincps.jsp, where the Content-Length header is missing or has a value of 0, the aforementioned loop will never exit due to the fact that readLine() will always return -1 and never satisfy the condition that it must return 3 or greater to exit the loop, causing an infinite loop and consuming excessive CPU resources, potentially leading to denial of service conditions.
A remote, unauthenticated attacker can exploit this vulnerability by sending an HTTP POST request without a Content-Length header or with a Content-Length header value of 0. Successful exploitation results in an infinite loop condition, causing excessive CPU usage and potentially leading to denial of service conditions on the target server.
Triggering the Problem:
• The server must have the vulnerable product installed and running.
• The attacker must have network connectivity to the target server.
Triggering Conditions:
An attacker sends an HTTP POST request without a Content-Length header or a header with a value of 0 to one of the vulnerable endpoints. The vulnerability is triggered when the server processes the request.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP, over port 8000/TCP
• HTTPS, over port 4443/TCP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS:15617 Oracle E-Business Suite Template Component DoS 3
• IPS:15618 Oracle E-Business Suite Template Component DoS 4
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor supplied patch resolving the vulnerability.
• Detect and filter malicious traffic using the signatures above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory