Operator of new Phobos variant gives blunt response during negotiation
The SonicWall Capture Labs threat research team have observed a new variant from the Phobos ransomware family. Like Sodinokibi, Phobos is sold on the criminal underground using the ransomware-as-a-service (RaaS) model. It is spread using various infection methods such as vulnerable Remote Desktop connections and spam email attachments. In the past we have seen Phobos primarily targeting businesses. However, recently we have also seen several reports of individuals being hit with this malware. During our analysis of this malware we negotiate ransom payment with the operator.
Infection cycle:
Upon infection, the following files are dropped onto the system:
- %APPDATA%\roaming\microsoft\windows\start menu\programs\startup\db_exec.exe [Detected as: GAV: Phobos.RSM_12 (Trojan)]
- {malware run location}\TempWmicBatchFile.bat
- {desktop}\info.hta
- {desktop}\info.txt
Files on the system are encrypted and given the following extension:
- id[94458690-2589].[helpisos@aol.com].isos
TempWmicBatchFile.bat contains the following script which, when executed, disables system recovery features:
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quiet
exit
info.hta contains the ransom message and is displayed multiple times on the desktop:
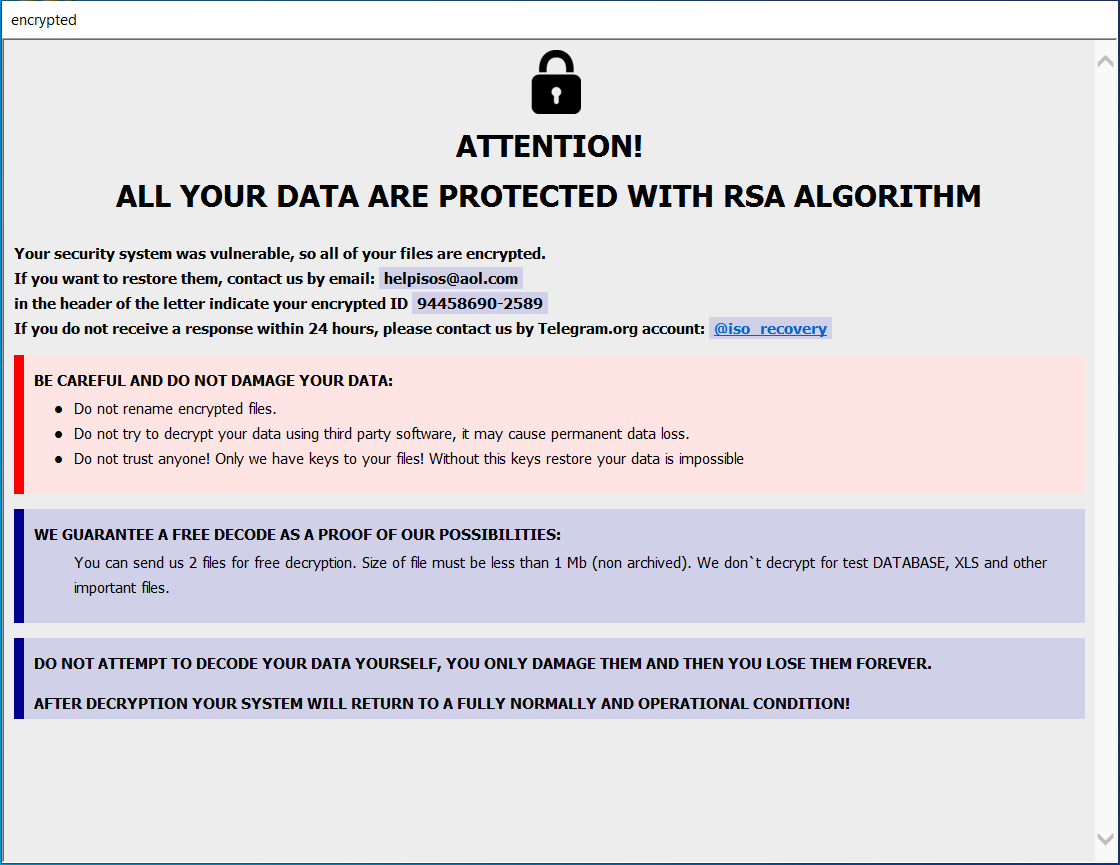
info.txt also contains the ransom message:
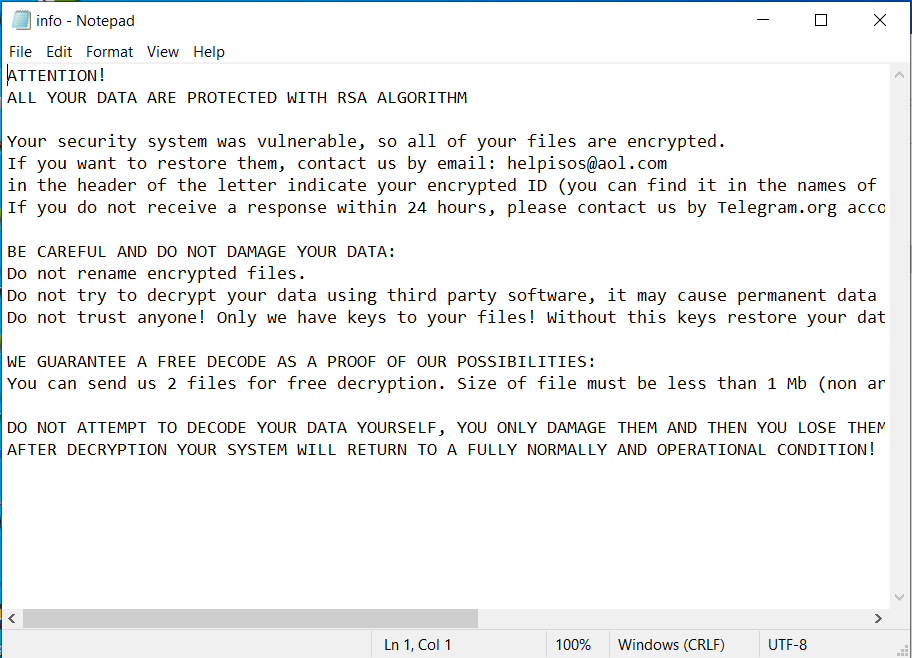
Negotiation:
We attempted to reach out to helpisos@aol.com as instructed in the ransom note but were notified by the email server that the address “couldn’t be found, or is unable to receive mail“. We proceeded to contact @iso_recovery on Telegram and had the following conversation with the operator:
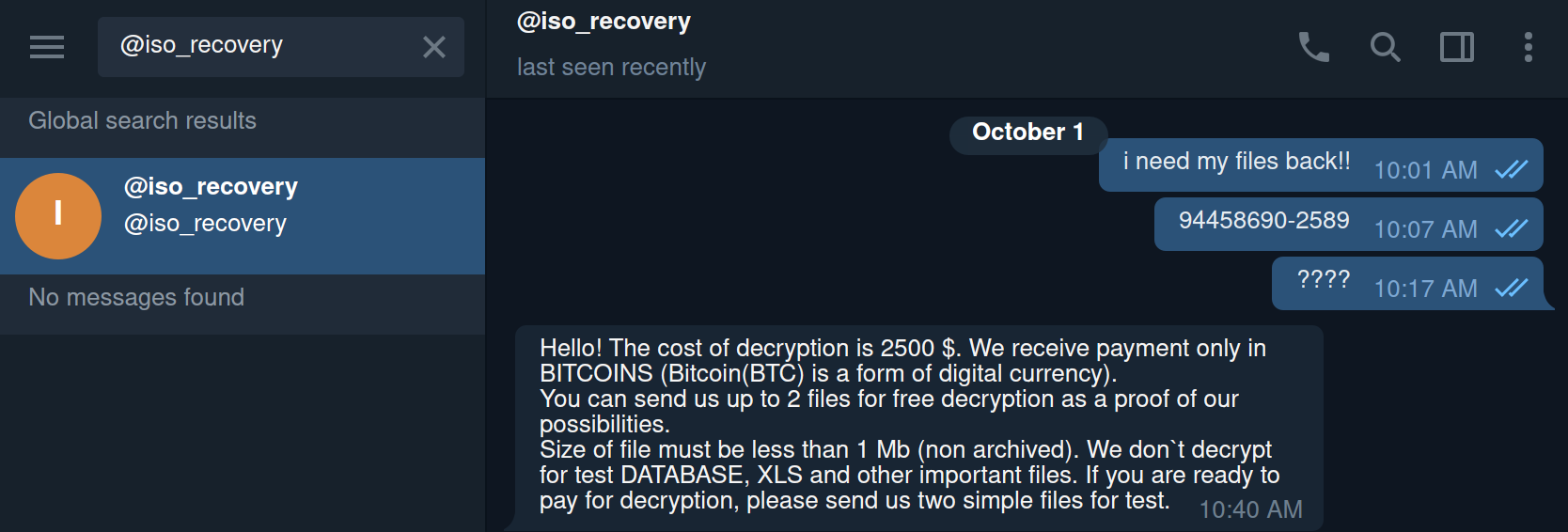
Nowadays, ransom fees for individuals are negotiable. We tried our luck to see how much of a discount is available:
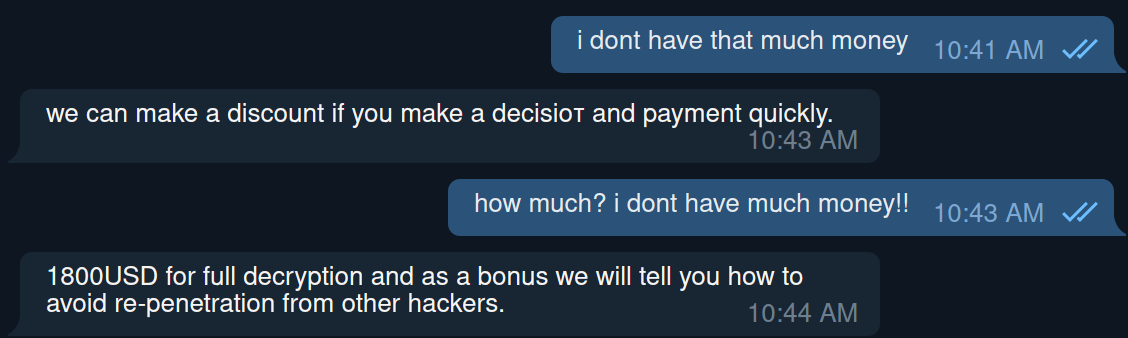
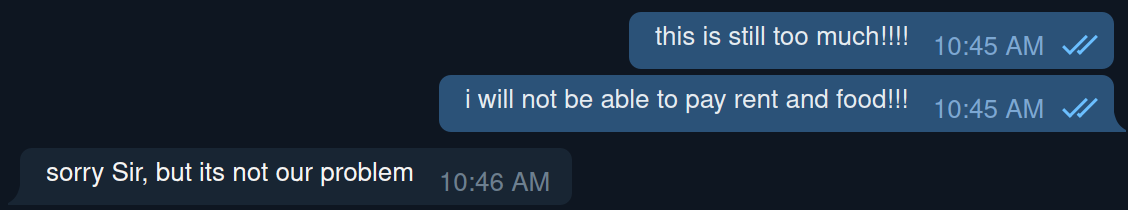
We attempted to push further and enlighten the operator about our “dire financial situation” but received the following blunt response:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Phobos.RSM_12 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




