OpenSSL Elliptic Curve Public Key Denial of Service
Overview:
A denial-of-service vulnerability has been reported in the OpenSSL library. The vulnerability is due to insufficient validation in BN_mod_sqrt() function.
A remote attacker could exploit the vulnerability by sending crafted packets to an OpenSSL server or any application using OpenSSL libraries. Successful exploitation could result in denial of service conditions on the affected service.
This issue affects OpenSSL versions 1.0.2, 1.1.1 and 3.0.
• Fixed in OpenSSL 3.0.2 (Affected 3.0.0,3.0.1).
• Fixed in OpenSSL 1.1.1n (Affected 1.1.1-1.1.1m).
• Fixed in OpenSSL 1.0.2zd (Affected 1.0.2-1.0.2zc).
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-0778.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 6.1 (AV:N/AC:L/Au:N/C:N/I:N/A:C/E:POC/RL:OF/RC:C).
Base 5.0 (AV:N/AC:L/Au:N/C:N/I:N/A:P):
• Access vector is NETWORK
• Access complexity is LOW
• Level of authentication required is NONE
• Impact of this vulnerability on data confidentiality is NONE
• Impact of this vulnerability on data integrity is NONE
• Impact of this vulnerability on data availability is COMPLETE
Temporal 3.7 (E:POC/RL:OF/RC:C):
• The exploitability level of this vulnerability is PROOF OF CONCEPT
• The remediation level of this vulnerability is OFFICIAL FIX
• The report confidence level of this vulnerability is CONFIRMED
Technical Overview:
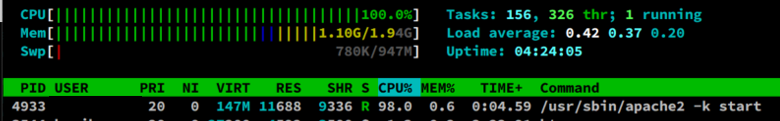
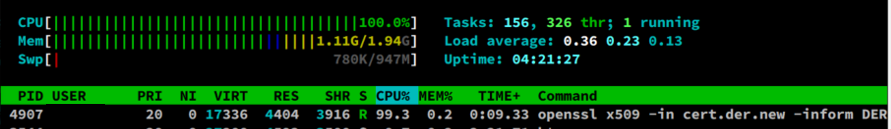
The vulnerability comes from BN_mod_sqrt() the interface function, which is used to calculate the modulo square root, and expects that the parameter p should be a prime number, but there is no check in the function, which may lead to an infinite loop inside. This function is used when parsing certificates in the following format:
• When the certificate contains the elliptic curve public key in compressed format.
• Certificates with explicit elliptic curve parameters whose base points are encoded in a compressed format.
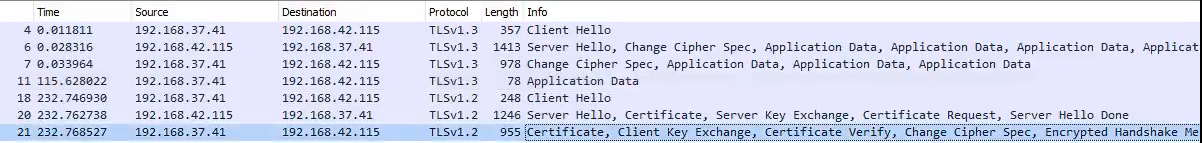
In short, this function is called when the point coordinates need to be decompressed when parsing the certificate. So the outside world can trigger an infinite loop by crafting a certificate with an illegal explicit curve parameter, causing a DoS attack.
Triggering the Problem:
• Parsing certificates that contain elliptic curve public keys in compressed form.
• Explicit elliptic curve parameters with a base point encoded in compressed form.
• Crafting a certificate that has invalid explicit curve parameters.
• Parsing crafted private keys as they can contain explicit elliptic curve parameters.
Triggering Conditions:
• TLS clients consuming server certificates.
• TLS servers consuming client certificates.
• Hosting providers taking certificates or private keys from customers.
• Certificate Authorities parsing certification requests from subscribers.
• Anything else which parses ASN.1 elliptic curve parameters.
• OpenSSL applications that use the BN_mod_sqrt() where you control the parameter values.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• SSL/TLS, OpenSSL
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 15407 OpenSSL BN_mod_sqrt Function DoS 1
• IPS: 15491 OpenSSL BN_mod_sqrt Function DoS 2
• IPS: 15351 OpenSSL BN_mod_sqrt Function DoS 3
• IPS: 15755 OpenSSL BN_mod_sqrt Function DoS 4
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Apply the IPS signature above.
• Apply the vendor-supplied patch that eliminates this vulnerability.
• Remove write permissions for untrusted users.
The vendor has released the following code changes regarding this vulnerability:
Vendor Code Change