Old Microsoft Office vulnerability CVE-2017-11882 actively being exploited in the wild
Attacks exploiting an one and half year old vulnerability in Microsoft office (CVE-2017-11882), are active in the wild again.
A remote code execution vulnerability exists in Microsoft Office software when the software fails to properly handle objects in memory. An attacker who successfully exploits the vulnerability could run arbitrary code in the context of the current user.
The vulnerability is caused by the Equation Editor, which fails to properly handle OLE objects in memory. This allows the attacker to execute arbitrary code in RTF files without interaction. Microsoft had patched this on 11/14/2017 . Recently Sonicwall Capture Labs threat research team observed a wave of exploits in the wild attacking this vulnerability.
The malicious rtf file has equation object

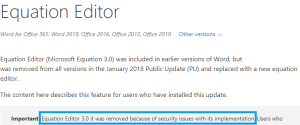
Microsoft has this warning about equation editor.
In the current wave of attacks, the malicious office document files are attached in the emails. The sender lures the user to open the file. The file has some content but the in background it exploits this vulnerability to download malicious payload on the victims computer.
The spam emails look like this:
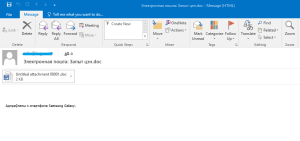
The file when opened looks like this
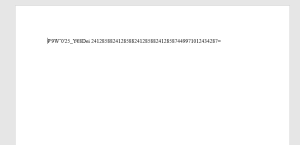
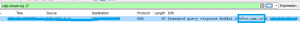
The rtf file drops file and contacts the attacker-controlled server.
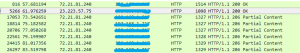
![]()
These types of attacks are a reminder to the importance of keeping systems updated with latest security patches.
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
- SPY 5046 Malformed-File rtf.MP.22
- GAV MalAgent.J_37354
- GAV CB_3 (Exploit)
- GAV H_12144 (Trojan)
- GAV CB_4 (Exploit)
- GAV CB_5 (Exploit)
- GAV CB_6 (Exploit)
- GAV BX_10 (Exploit)
- GAV BS_4 (Exploit)
- GAV AS (Exploit)
SonicWall Capture Advanced Threat Protection (ATP) with RTDMI provides protection against this threat.
Threat Graph:

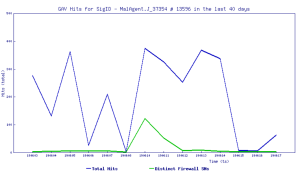
IoC:
Rtf files :
760ff63642a0c236c4d1f88a8a6c94de1d4087010d3373a6122ab48fa505aed3
2af097a6fe6cc30943ef386c8950787492c5a20ae5de2d15b7d8a248b0c44a8c
cf00a1c2a61cc6a684e768b71bbca78436a28d37e8f982af409eaea1881f1f1f
ab618f0fc42cd3dd63d4901a678cfef419ee06ee374d6425d2ea27668c207b62
b865e203294170ed4de563371dee3a5c4e42d3bf19345ae72c5b2b463121edfb
5b5e9b8165cc731fe242796422dabd8721433a07426de4717f248e3c250439a5
Email:
9ccb84d16ff5ea5b1837bfe4951934b3382ce0bc2b9dd2ffd795a75232303831
7ba7a39fc505601966e88c31ecc3521a3f44ab9397ec24f1b2d5c136fe8c60c2




