Nemty 1.6 ransomware released. Uses 8192-bit encryption.
The SonicWall Capture Labs Threat Research Team observed reports of a new version of Nemty ransomware being delivered via the RIG exploit kit. Previous versions of Nemty have used a variety of methods to infect users including a phishing techniques using a fake Paypal website. Released in August 2019, Nemty has undergone various changes including using 8192-bit encryption keys to encrypt files. The proposed cost of decryption is 0.17968 BTC (around $1500 USD at the time of writing).
Infection Cycle:
The trojan uses the following icon:
Upon infection, files on the system are encrypted and “_NEMTY_8MD1JU0_” is appended to each filename.
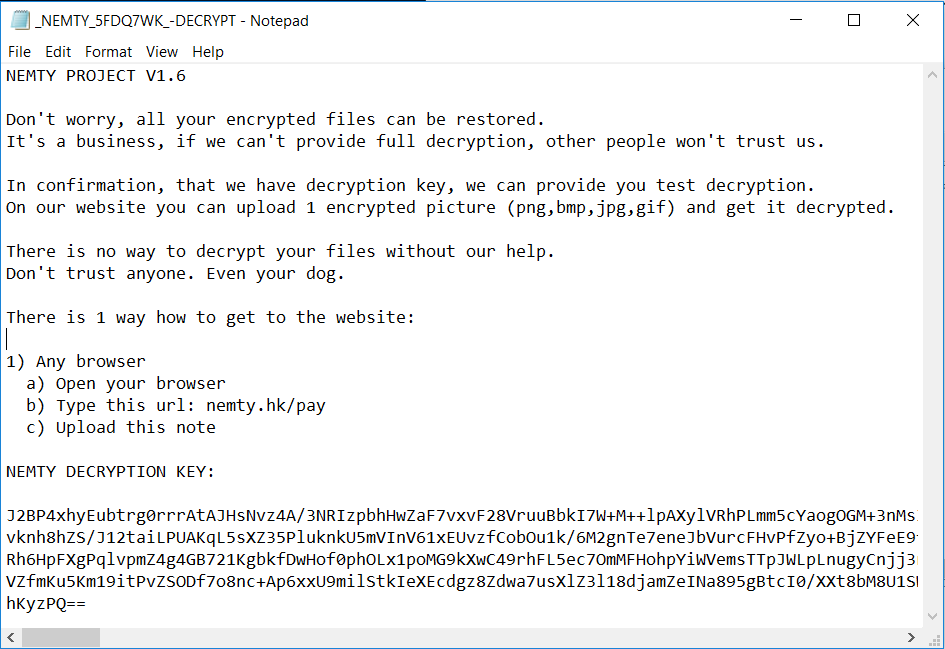
The following ransom note is displayed on the desktop:
The trojan adds the following file to the system:
- %USERPROFILE%\AdobeUpdate.exe (copy of original) [Detected as GAV: Nemty.FN_2 (Trojan)]
The trojan adds the following data to the registry to keep track of crypto key information:
- HKEY_CURRENT_USER\Software\NEMTY
- HKEY_CURRENT_USER\Software\NEMTY fid “_NEMTY_8MD1JU0_”
- HKEY_CURRENT_USER\Software\NEMTY pbkey “BgIAAACkAABSU0ExAAgAA….”
- HKEY_CURRENT_USER\Software\NEMTY cfg “ydtMmiDIWOLCeoUK…..”
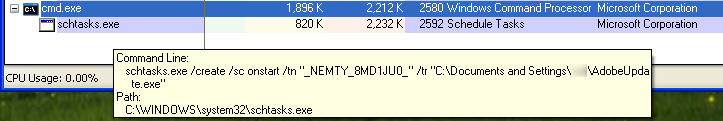
It adds a scheduled task so that it starts up after reboot via the following command:
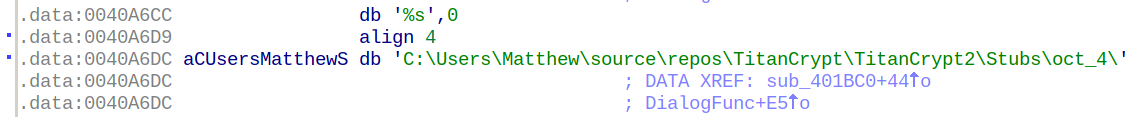
The trojan is packed with TitanCrypt in an attempt to thwart debugging:
The trojan obtains the systems public IP address and geolocation:
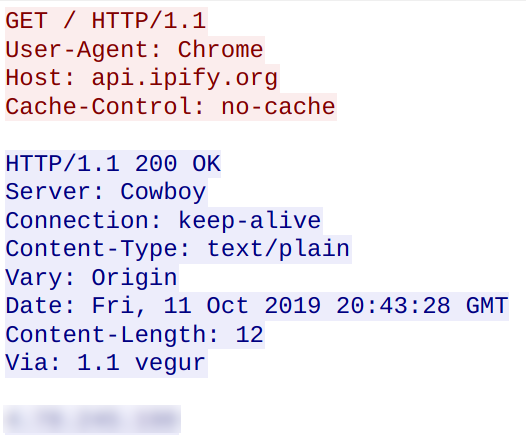
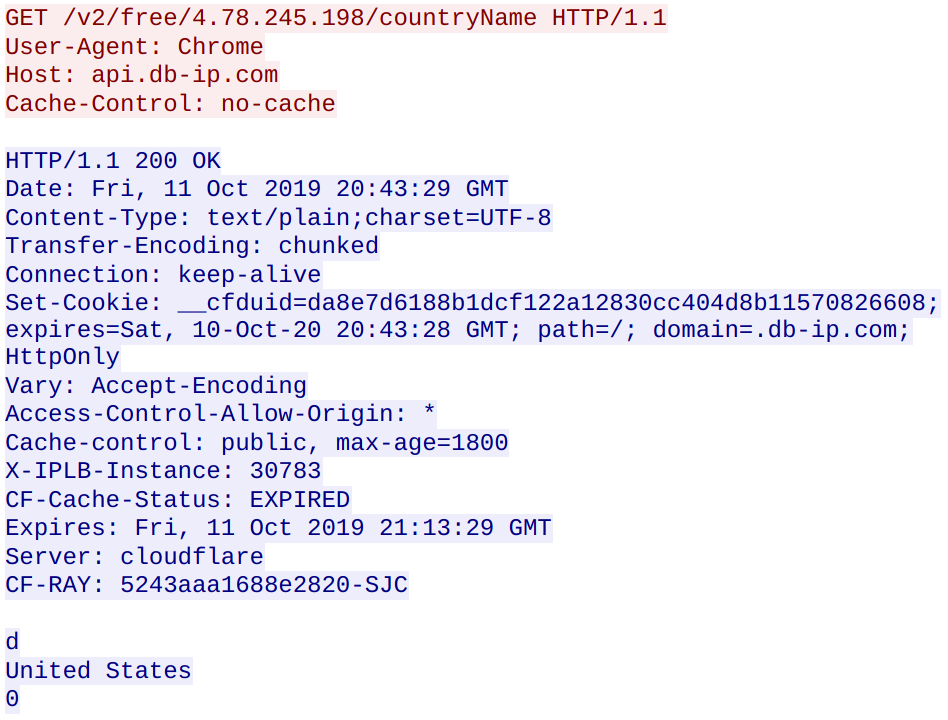
The ransom note contains instructions to go to https://nemty.hk/pay in order to decrypt files.
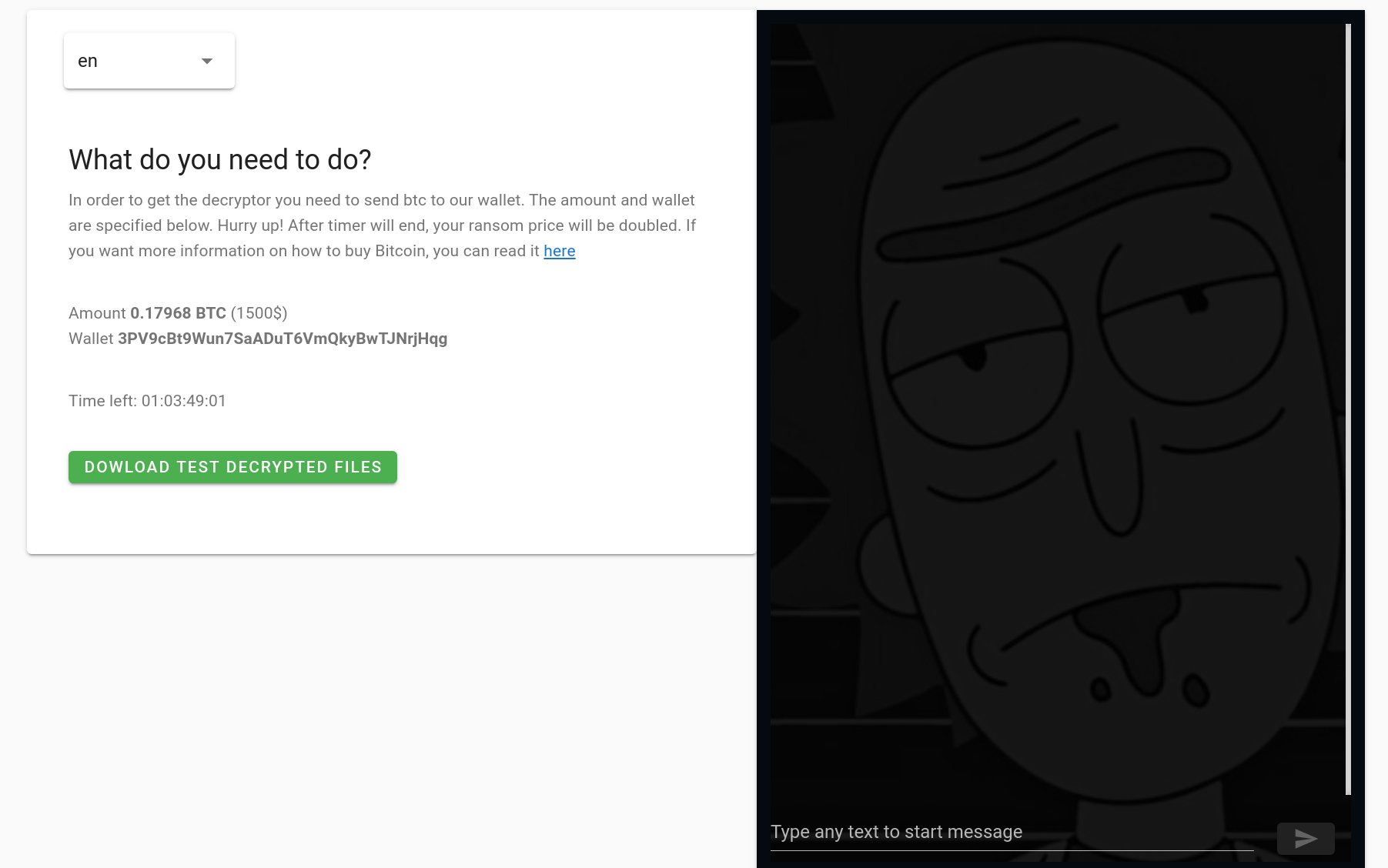
The link leads to a page with the following dialog:
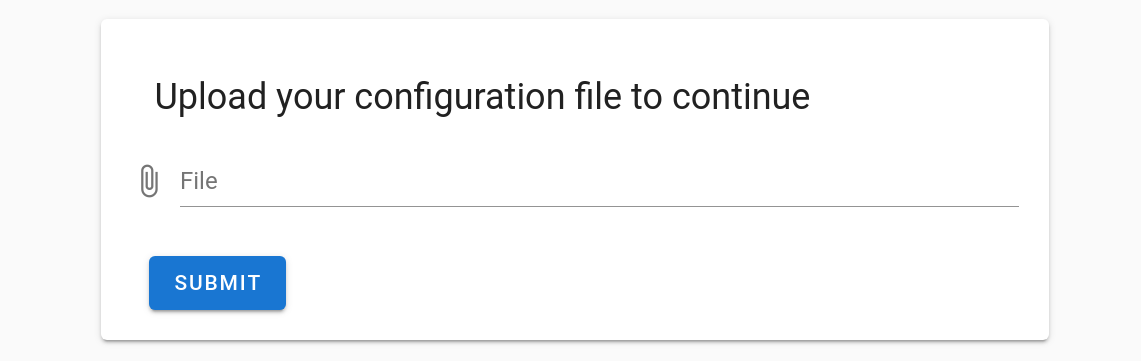
After uploading the ransom note that contains the “NEMTY DECRYPTION KEY“, you are able to upload a sample file to decrypt:
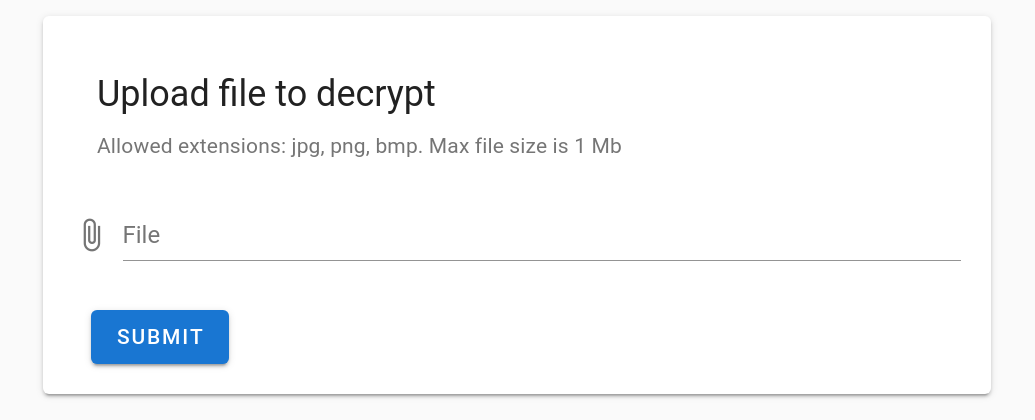
The following page allows you to download the decrypted file and also chat with the operators via the chat box. At the time of our analysis no one responded to our questions.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Nemty.RSM (Trojan)
- GAV: Nemty.RSM_2 (Trojan)
- GAV: Nemty.RSM_3 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




