Money message Ransomware actively targeting large organization
Recently, the SonicWall Capture Labs Research team analyzed a ransomware called Money message. Written in C++, this ransomware encrypts the victim’s files without changing the filename or appending the extension, making it more difficult to identify which files have been compromised. Once the files are encrypted, the attackers demand a ransom payment in exchange for the decryption key.
Infection Cycle:
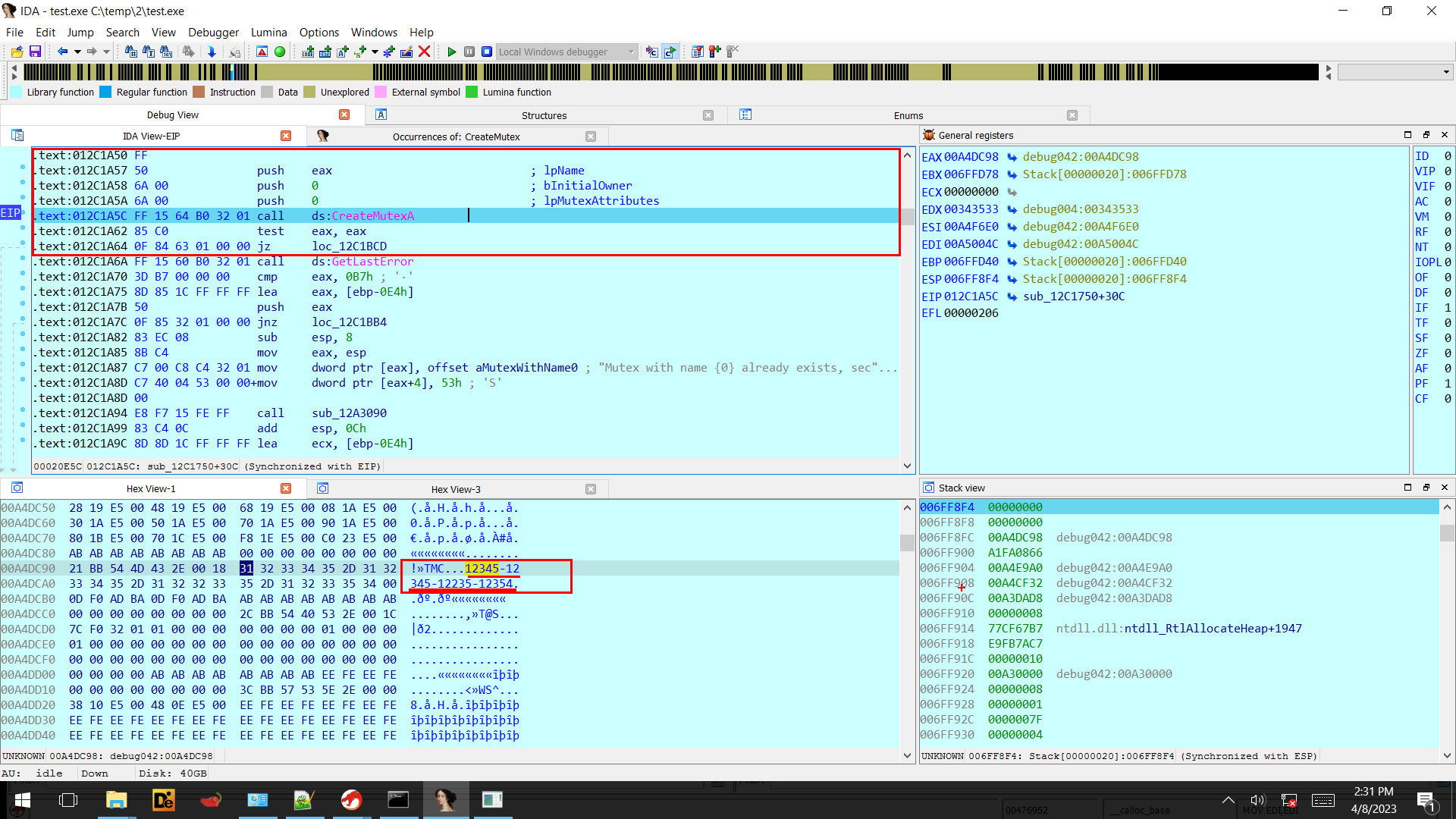
At the start of the execution it creates a named mutex “12345-12345-12235-12354” to avoid different instance of Money message Ransomware running on the same system.
It uses WMI (Windows Management Instrumentation) Query and Service Control Manager to disable the specific list of services.
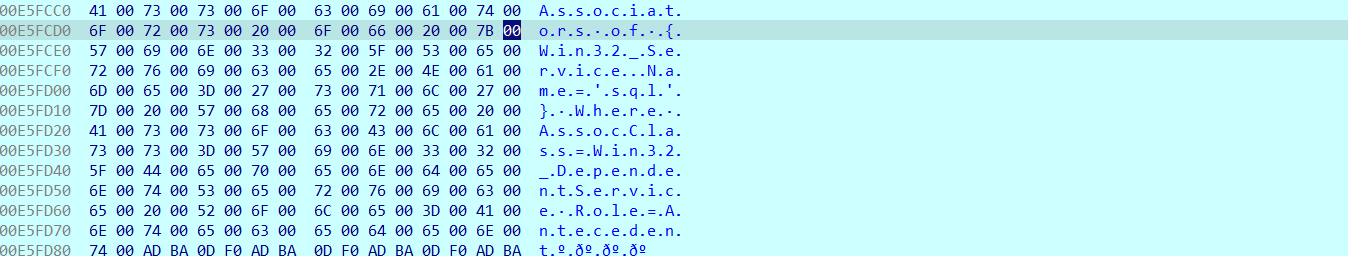
Associators of {Win32_ServiceName=’sql’} Where AssocClass=Win32_DependentService Role=Antecedent
It opens the Service Control Manager (SCM) by calling OpenSCManagerW() function.
It then calls OpenServiceW() function to open the service from the list and EnumDependentServicesW() function to enumerate all its dependent services, If any of the services present from the list is found to be running, the ransomware stops them using ControlService() function.
Below are the list of the services that are stopped by the ransomware
vss
sql
svc$
memtas
mepocs
sophos
veeam
backup
vmms
It then enumerates the running processes on the system and terminates the below list of processes.
sql.exe
oracle.exe
ocssd.exe
dbsnmp.exe
synctime.exe
agntsvc.exe
isqlplussvc.exe
xfssvccon.exe
mydesktopservice.exe
ocauto upds.exe
encsvc.exe
firefox.exe
tbirdconfig.exe
mdesktopqos.exe
ocomm.exe
dbeng50.exe
sqbcoreservice.exe
excel.exe
infopath.exe
msaccess.exe
mspub.exe
onenote.exe
outlook.exe
powerpnt.exe
steam.exe
thebat.exe
thunderbird.exe
visio.exe
winword.exe
wordpad.exe
vmwp.exe
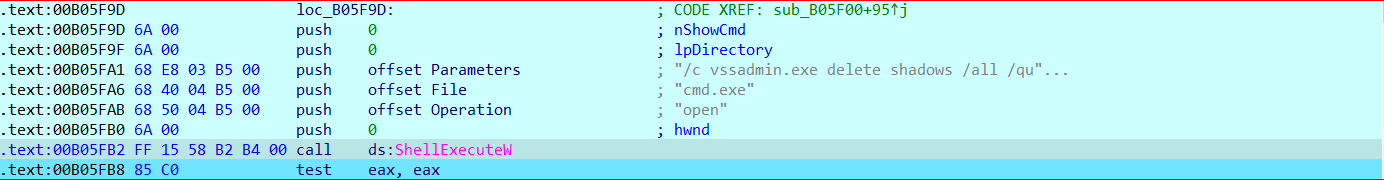
It deletes the volume shadow copies using ShellExecuteW() function by passing below command
It avoids encrypting the files from below directories
It also has a list of files which it avoids encrypting:
The files which are not present in the whitelisted directories nor the files are whitelisted are encrypted by the ransomware.
Once the files are encrypted the filename of the original file remains the same nor the extension of it is changed.
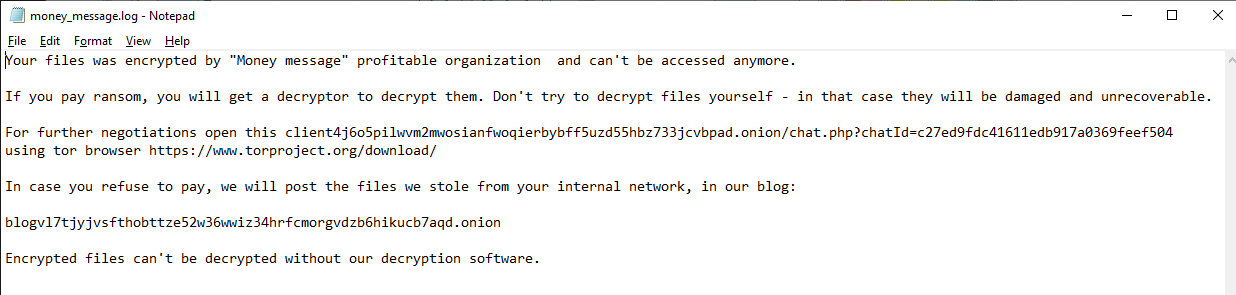
Once the files are encrypted it displays below ransom message
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV:MoneyMsg.RSM (Trojan)
SonicWall RTDMI engine – part of capture ATP – has a proactive 0-day protection against this ransomware.