Misinformaiton related to CoronaVirus is being used to further propagate malicious Android RAT
SonicWall Threats Research Team recently blogged about an Android RAT that uses the CoronaVirus name in an attempt to lure victims. We found a website that currently serves (at the time of writing this blog) an Android RAT belonging to the same family.
Propagation Mechanism
The attackers have created a website that spreads misinformaiton about CoronaVirus. They aim to attract new victims via download links on these websites.
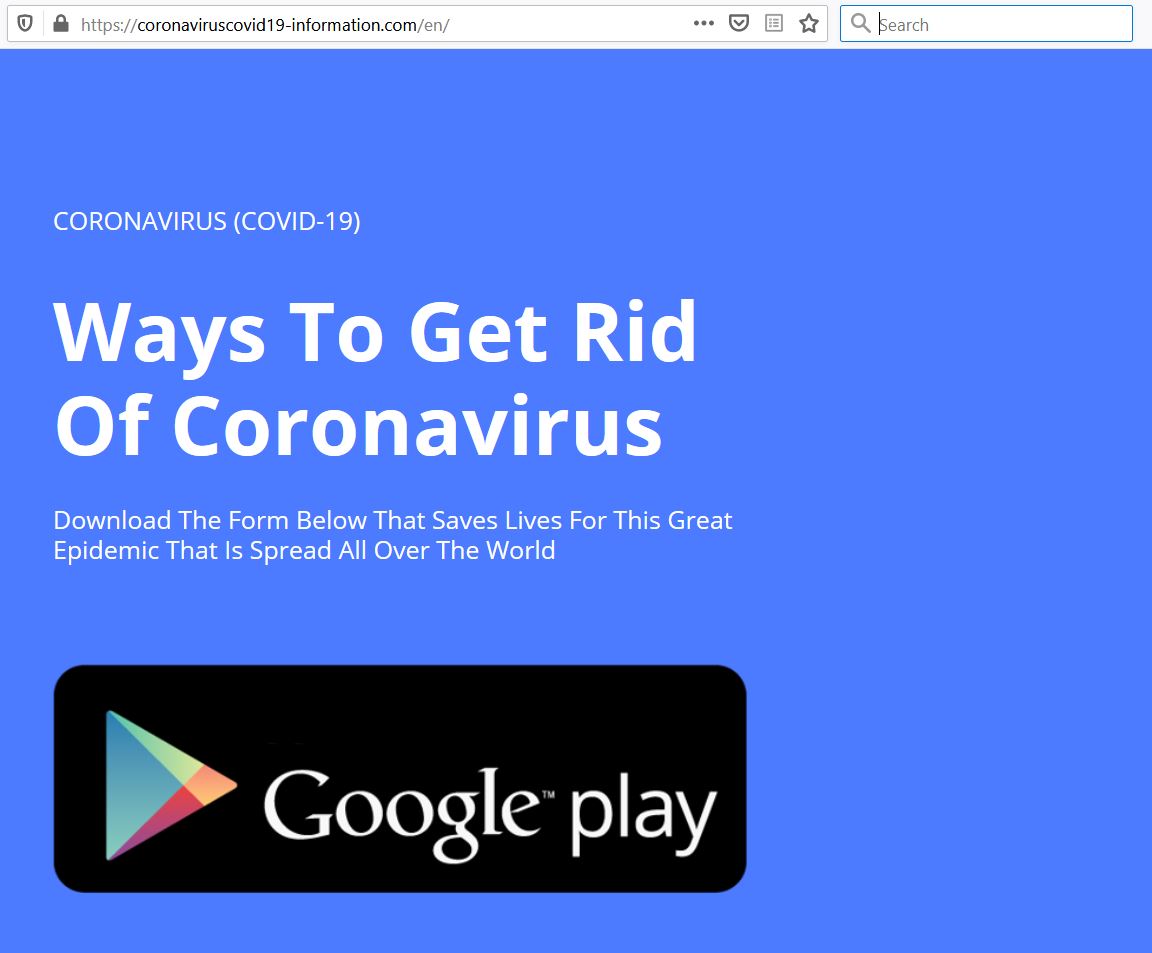
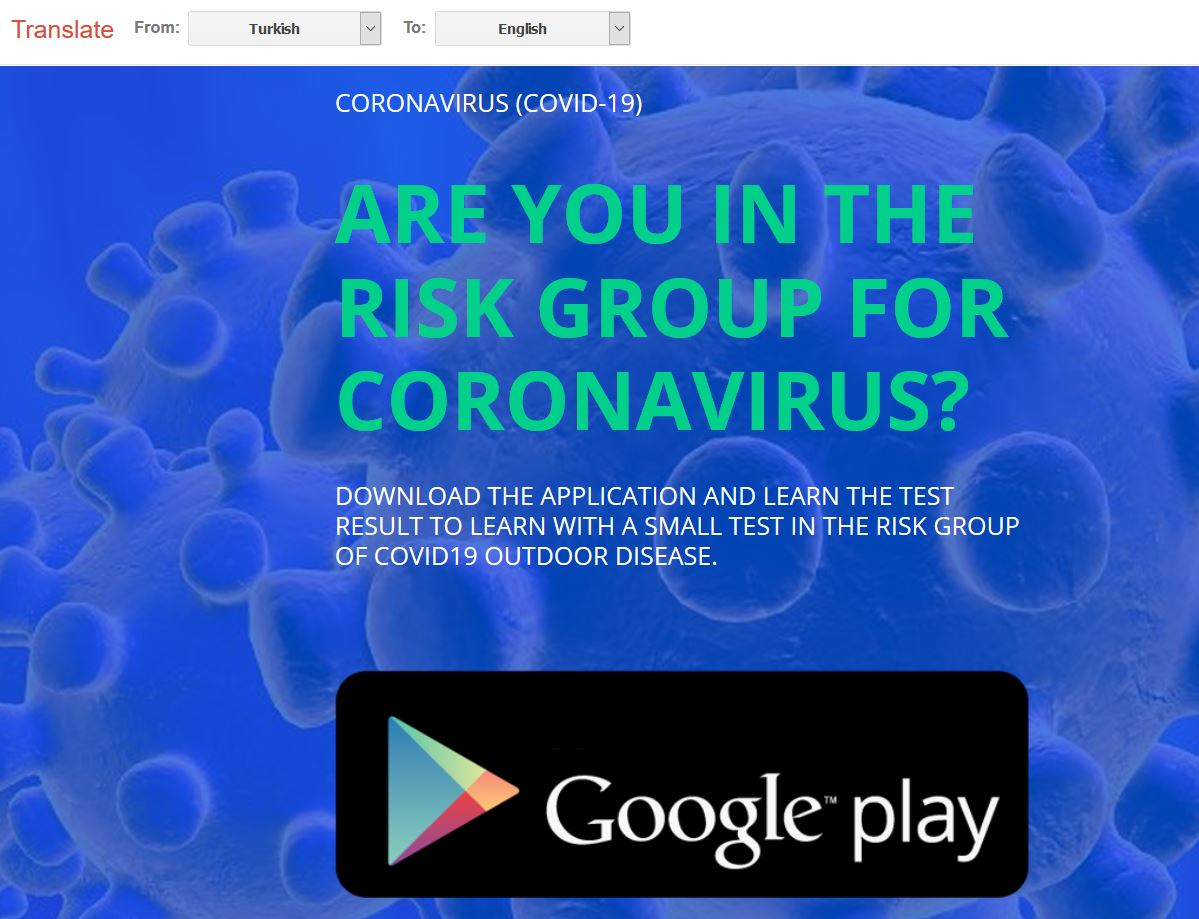
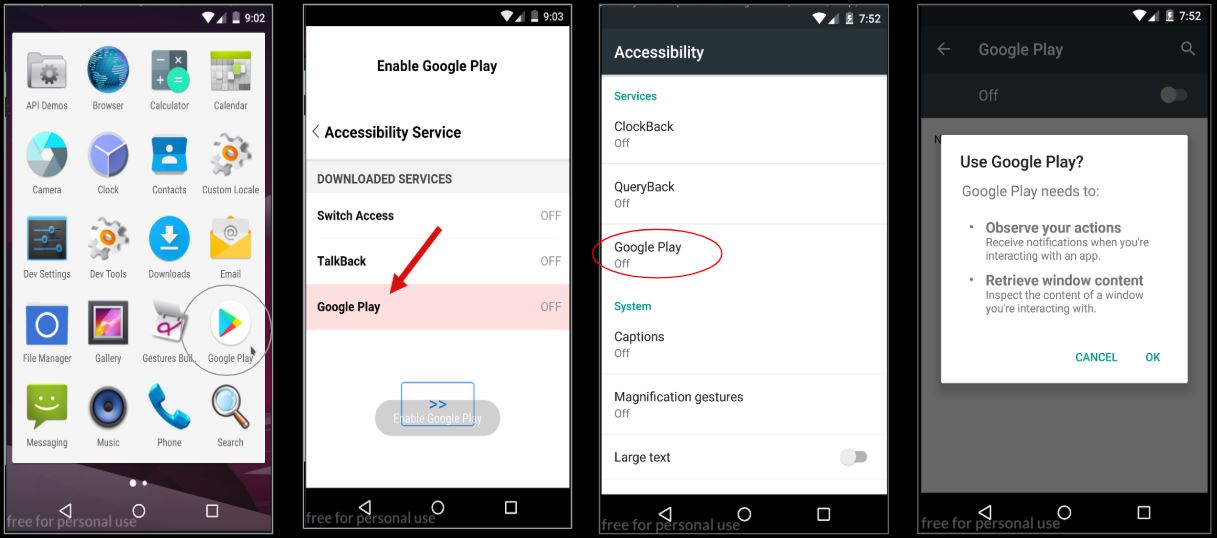
We found two versions of this website, one in English and another in Turkish which serve the apk named corona.apk on clicking the on Google Play image:
- English version: hxxps://coronaviruscovid19-information.com/en/
- Turkish version: hxxps://coronaviruscovid19-information.com/tr/
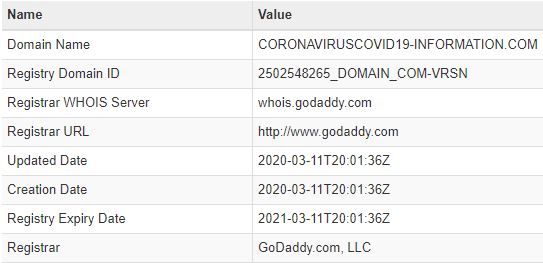
Whois details reveal that the website was hosted recently:
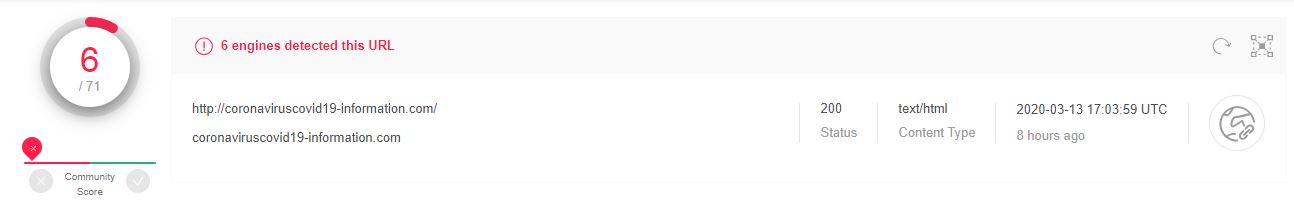
The website has already been marked malicious on VirusTotal:
Sample analysis and details
A more thorough detail of this type of sample has been highlighted in our previous blog. Few highlights of the infection cycle for this type of sample are listed below.
Sample details:
- Package Name: cpymezxmapzsdforaduuda.illoyztchthogekxpd.fojccdfkzahlhfmcaeowdalsjp
- App Name: Google Play
- MD5: 599db33d534d1e98ea63dd2ce30100a7
The sample gets installed by the name of “Google Play”. Upon installation and execution the sample requests for Accessibility services:
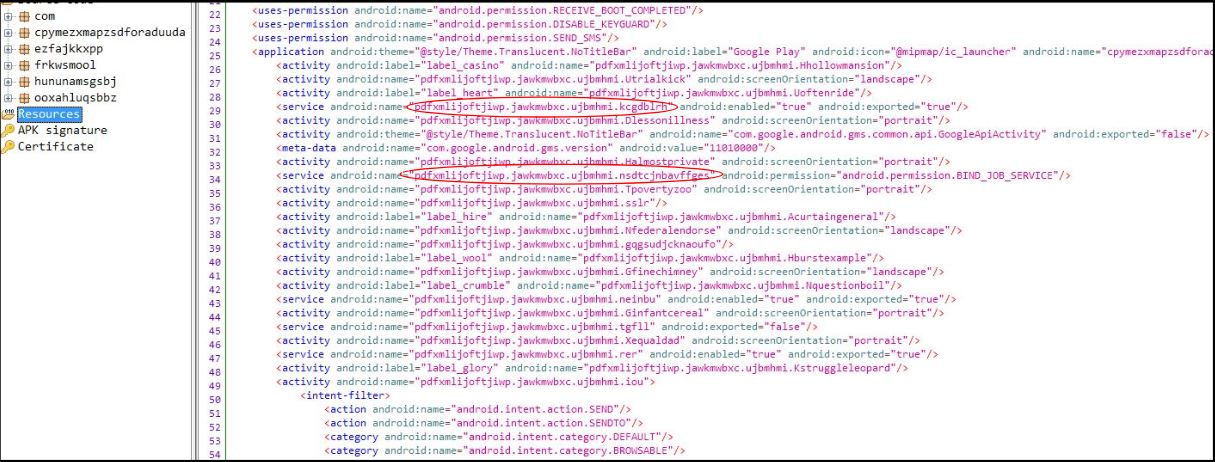
Upon downloading the apk file and examining the code we see a similar structure to the one we outlined in the previous blog. As shown below, the class files mentioned in the Manifest.xml file are not present in the code, which means they are loaded during runtime:
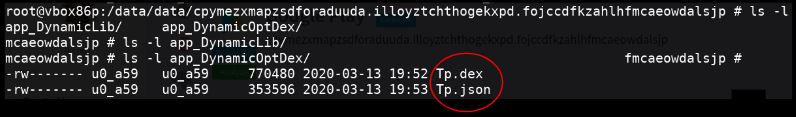
When the sample executes a .json file is dropped on the system which is actually a dex file, in this case the name of the files is Tp:
On loading this .dex file we finally see the class files and the code.
Capabilities
As stated in the previous blog this sample is an Android RAT and can perform a number of malicious operations, few of these functions include:
- Get information about the device
- Get a list of apps installed
- Allow remote control of the device via teamviewer
- Steam Gmail password, lock pattern
- Keylogger
- Upload files
- Steal SMS messages, contacts
- Disable Play Protect
Interesting Observation
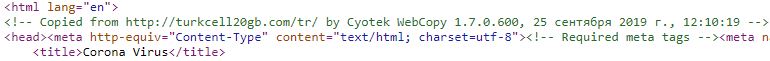
Inspection of the source of revealed something interesting. We observed a comment that states – Copied from http://turkcell20gb.com/tr/ by Cyotek WebCopy сентября 2019 (September 2019):
There is a lot of misinformation and panic surrounding CoronaVirus. We would like to re-iterate that there are no mobile apps that can track CoronaVirus infections or point to a vaccine. Please exercise caution when absorbing any information related to CoronaVirus.
SonicWall Capture Labs provides protection against this threat with the following signatures:
- AndroidOS.CoronaVirus.Spy (Trojan)
Update – March 23,2020
We have consolidated the detection into a single signture instead of the two signatures listed earlier. The new signature is GAV: AndroidOS.CoronaVirus.Spy