While the world is suffering from Coronavirus disease (COVID-19) pandemic, malware authors are not missing their chances to take advantage from the pandemic scare and making the situation worse for the people. The SonicWall Threats Research team first observed the corona scares used by malware authors on February 4, 2020 and then keeping an eye on the campaign. We observed that COVID-19 scare is not only used by one malware family, perhaps multiple malware families are using the scare to get into the victim’s machine. The malware authors majorly distributing the malware files as an email attachment, stating it as COVID-19 related document. We have listed malware families which are misusing COVID-19 scare since Jan 2020.
GOZ InfoStealer:
The GOZ InfoStealer is known for stealing user data from installed applications, along with victim’s system information, which is then sent to the threat actor over Simple Mail Transfer Protocol.
| SHA256 |
faa7e2cbf2174401e13e18eaf50e43268db358a05d38c7c4bdbd9968e7f91221 |
| Archive Name |
Executable Name |
Date |
| CoronaVirus_Safety_Measures.rar |
CoronaVirus_Safety_Measures.exe |
5-Feb-2020 |
| SHA256 |
cf8ff986bb8b64d1f310ea6c3bb42aee2d2ca25478dfcfca55764880129ca8a2 |
| Archive Name |
Executable Name |
Date |
| FYR_COVID-19.CAB; |
COVID-19.exe |
13-Mar-2020 |
| SHA256 |
6bd5f8e80baeec88c836e465f39f779f4f638d538511c0f5effd3c7043ddad16 |
| Archive Name |
Executable Name |
Date |
| Coronavirus (COVID-2019) Safety Measures.gz |
Coronavirus (COVID-2019) Safety Measures.exe |
16-Mar-2020 |
| SHA256 |
c172d41be2a7644dca00fac50821d7f783eddc662c4f2409a60ce193fb6fb72d |
| Archive Name |
Executable Name |
Date |
| Coronavirus (COVID-2019) Safety Measures(2).7z |
Coronavirus (COVID-2019) Safety Measures(2).exe |
16-Mar-2020 |
| SHA256 |
05da803235e16b1e372d722956b1626cc52b6947af53063259a4ef58ab8bb8c9 |
| Archive Name |
Executable Name |
Date |
| COMUNICAT AGC COVID-19.tar |
COMUNICAT AGC COVID-19.exe |
17-Mar-2020 |
| SHA256 |
07279fec6937f9a4bdc913fc59c41f66fe30e9b575e999bad5ff5d03697218cc |
| Archive Name |
Executable Name |
Date |
| 2020-03-17 COVID-19 Client Communication_VA.pdf.gz |
2020-03-17 COVID-19 Client Communication_VA.pdf.exe |
17-Mar-2020 |
| SHA256 |
2d0b6f68767b4a71950fa19852bf10c78ea5de5b79552e2b0cfad217358df9cd |
| Archive Name |
Executable Name |
Date |
| dpcm 17-3-2020- COVID-19_pdf.rar |
dpcm 17-3-2020- COVID-19_pdf.exe |
17-Mar-2020 |
| SHA256 |
4b6e683ba34dfbd3d07ff18667cfaed341357d8839d10749bef31c05288a5690 |
| Archive Name |
Executable Name |
Date |
| 2020-03-17 COVID-19 Client Communication_VF.pdf.gz |
2020-03-17 COVID-19 Client Communication_VF.pdf.exe |
17-Mar-2020 |
| SHA256 |
c89f28698c375ff47ac444eb912bd51cdedc28a934bcd5b83fbea3770e68e5fc |
| Archive Name |
Executable Name |
Date |
| Covid-19_Precaution.rar; |
Covid-19_Precaution.exe |
17-Mar-2020 |
| SHA256 |
ca70837758e2d70a91fae20396dfd80f93597d4e606758a02642ac784324eee6 |
| Archive Name |
Executable Name |
Date |
|
|
17-Mar-2020 |
| SHA256 |
e52d171b0a4b6a14374ac9d53c5950815b5a0cc5ad0f479ba044621b6a86d5c7 |
| Archive Name |
Executable Name |
Date |
| W.H.O CUSTOMER ADVISORY COVID19.ace |
W.H.O CUSTOMER ADVISORY COVID19 |
17-Mar-2020 |
| SHA256 |
e52d171b0a4b6a14374ac9d53c5950815b5a0cc5ad0f479ba044621b6a86d5c7 |
| Archive Name |
Executable Name |
Date |
| W.H.O CUSTOMER ADVISORY COVID19.ace |
W.H.O CUSTOMER ADVISORY COVID19 |
17-Mar-2020 |
| SHA256 |
0fdd79e3372701bf0f9c3e8ba30d72444000787993a7815764bc2b5693eebd40 |
| Archive Name |
Executable Name |
Date |
| COVID- 19.tar |
COVID- 19.exe |
18-Mar-2020 |
| SHA256 |
2c464648ff97fd39dab054d0c3e1bd249e244fcc975b697e312796669c7763f1 |
| Archive Name |
Executable Name |
Date |
| NA |
Covid 19 Immunity Tips.exe |
18-Mar-2020 |
| SHA256 |
15e029c3834435150c76741e714540fcb799662db8cc2c61ba4ef192a781727b |
| Archive Name |
Executable Name |
Date |
| Greek |
Greek |
18-Mar-2020 |
| SHA256 |
43670ae43df9e361fa15f09f611da32db104ee207ed5af3e7e7f098ad82a68e0 |
| Archive Name |
Executable Name |
Date |
| COVID-19 WHO RECOMENDED V.gz |
COVID-19 WHO RECOMENDED V.exe |
18-Mar-2020 |
| SHA256 |
56552bdb4519ca608e20f4dde940a92353b5cde990cc93ad6e739602e0f09b7a |
| Archive Name |
Executable Name |
Date |
| #0302019 ITEMS SPECIFICATION.tar |
Solution_to_coronavirus.exe |
18-Mar-2020 |
| SHA256 |
b90ace49508a1cd157cb8885656dcef062d69cf9e9bc5dac87802487b21ddf78 |
| Archive Name |
Executable Name |
Date |
| CIRCULAR MEDIDAS EXTRAORDINARIAS CORONAVIRUS.tar |
CIRCULAR MEDIDAS EXTRAORDINARIAS CORONAVIRUS.exe |
19-Mar-2020 |
Remcos RAT:
REMCOS designed as Remote Control and Surveillance tool for legitimate purpose but it is being used by malware authors from a few years. The malware gathers and sends victim’s system information to its Command and Control (C&C) server and it is also capable of performing the tasks below:
- Screen Capture
- Remote CommandLine
- Remote Registry Editor
- Download, Upload and Execute files
- Login cleaner
| SHA256 |
d3cfdfed59ecbe333cc589d88151565721ad55c9ef5542c680fb5077d411386c |
| Archive Name |
Executable Name |
Date |
| CORONA VIRUS 1.uue |
CORONA VIRUS 1.exe |
19-Feb-2020 |
NanoCore RAT:
NanoCore Remote Access Trojan (RAT) is known for spying and stealing victim’s machine information:
| SHA256 |
87befa6cb254eee8f9d45671d8dbb015fbd8b04230fd590f084bcd26242930c8 |
| Archive Name |
Executable Name |
Date |
| CORONA VIRUS 2.uue |
CORONA VIRUS 2.exe |
19-Feb-2020 |
After looking into the delivery patterns and agent files involved in executing the Remcos and NanoCore on victim’s machine, we can say the malware families have somehow linked to each other.
NetWire RAT:
NetWire RAT enables access to the victim’s machine from the remote host:
| SHA256 |
db5038d60d1f0ee2f57fe0b3ee12f80ff10a90e088bd3316632036f4238823bf |
| Archive Name |
Executable Name |
Date |
| UNICEF COVID-19 APP.arj |
UNICEF COVID-19 APP.exe |
16-Mar-2020 |
HawkEye RebornX:
HawkEye has been active in the wild from the last few years. It has the features below:
- Key-logging
- Password stealing
- Screen capture
- Clipboard
| SHA256 |
f3eac3b0b250ae5da352a6d1358e9729e79af9549bc04f53d83283b5b07679fd |
| Archive Name |
Executable Name |
Date |
| Coronavirus Disease (COVID-19) CURE.rar |
Coronavirus Disease (COVID-19) CURE.exe |
19-Mar-2020 |
| SHA256 |
d4bf55a016c9d5bf28b4945c682e5f998efddbffe5578600a070da12eb985d78 |
| Archive Name |
Executable Name |
Date |
| Coronavirus Disease (COVID-19) CURE.rar |
Coronavirus Disease (COVID-19) CURE.exe |
19-Mar-2020 |
Unclassified InfoStealer:
This InfoStealer’s behavior is very much similar to GOZ InfoStealer, it steals user data from installed application and clipboard:
| SHA256 |
9df044870a8aaae7c5d11307f3bfb15887e5836a4e9cb5b6962cfddd7f8f7396 |
| Archive Name |
Executable Name |
Date |
| Document Arrival COVID-19 Detection.zip |
Document Arrival COVID-19 Detection.zip |
17-Mar-2020 |
Evidence of the detection by RTDMI(tm) engine for each malware family can be seen below in the Capture ATP reports:
GOZ InfoStealer
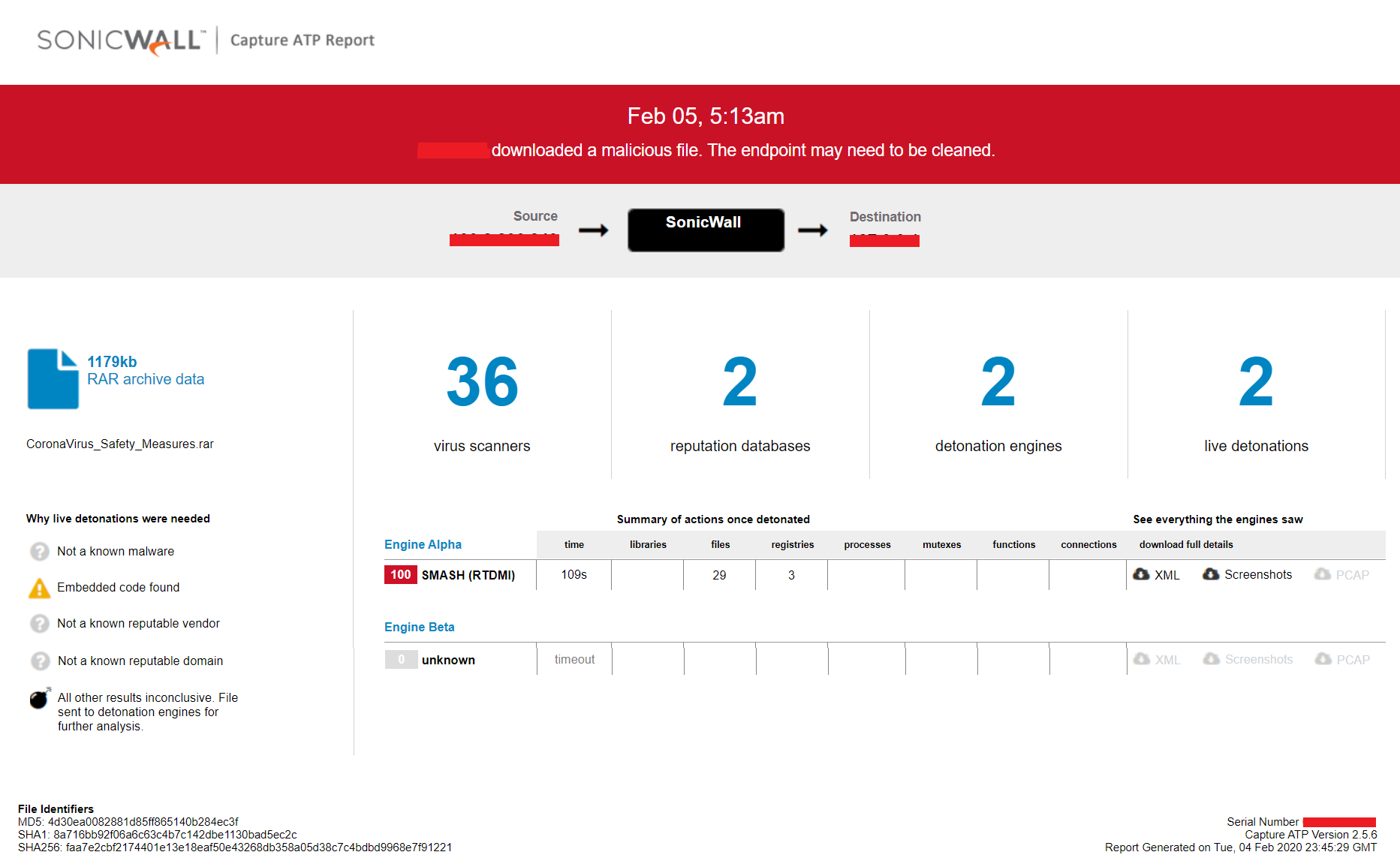
Remcos RAT
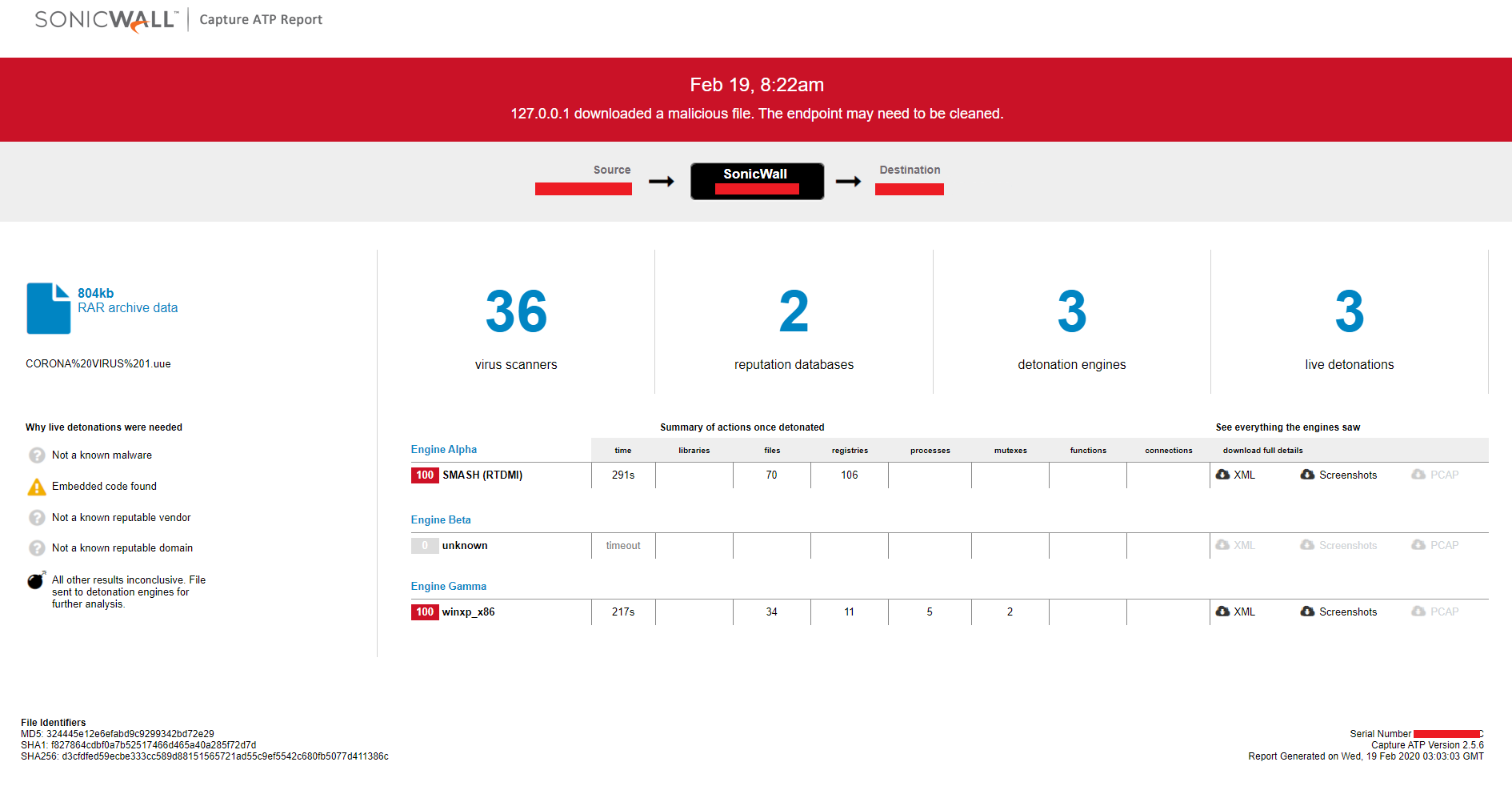
NanoCore RAT

NetWire RAT

HawkEye Reborn
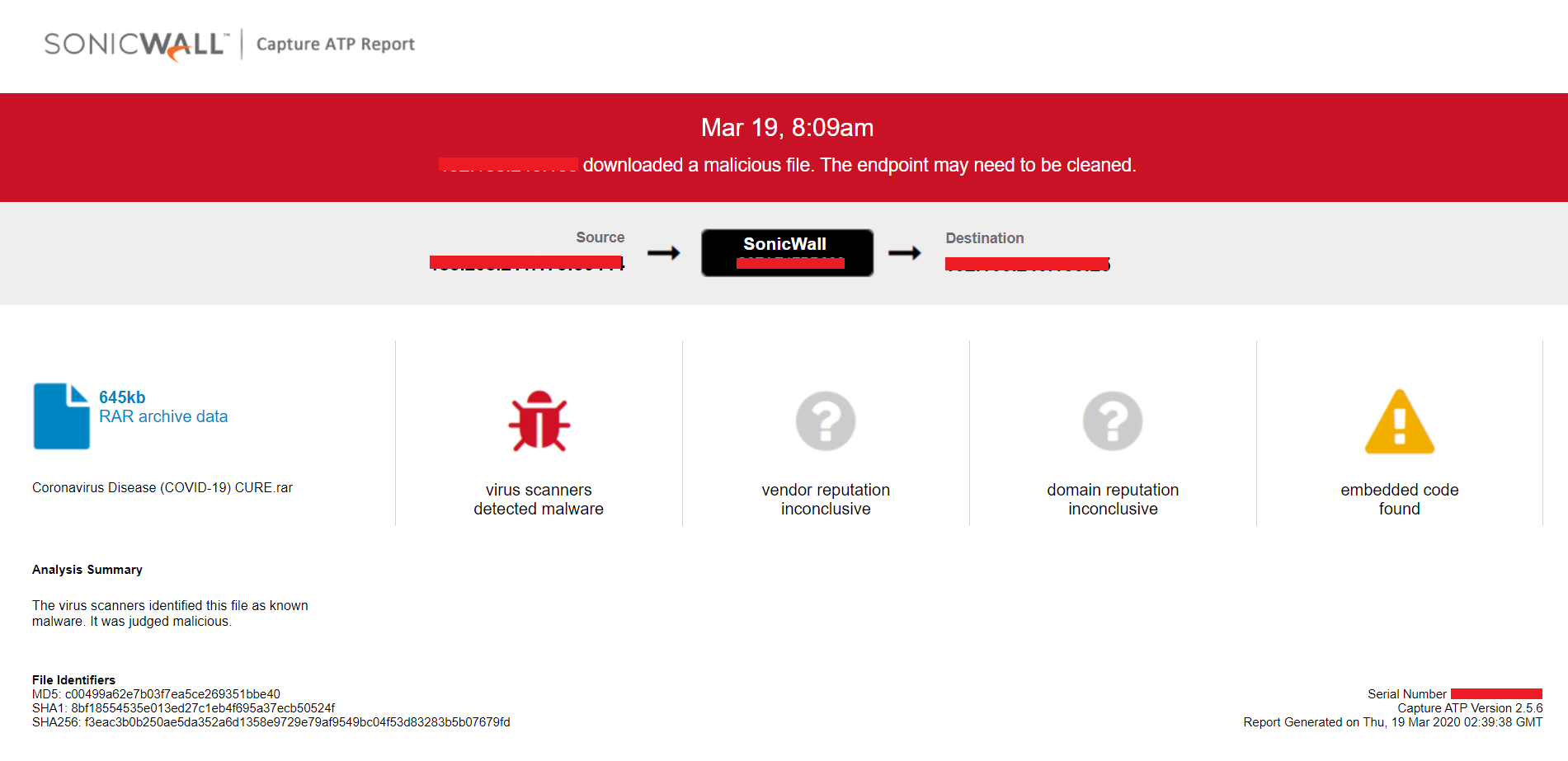
The SonicWall Capture Labs Threat Research Team gathers, analyzes and vets cross-vector threat information from the SonicWall Capture Threat network, consisting of global devices and resources, including more than 1 million security sensors in nearly 200 countries and territories. The research team identifies, analyzes, and mitigates critical vulnerabilities and malware daily through in-depth research, which drives protection for all SonicWall customers. In addition to safeguarding networks globally, the research team supports the larger threat intelligence community by releasing weekly deep technical analyses of the most critical threats to small businesses, providing critical knowledge that defenders need to protect their networks.










