Malware demands Bitcoin fine for fraudulently detecting pirated software
Running pirated software comes with risks. Counterfeit software packages commonly come bundled with adware or malware that can infect your system. But most importantly, using pirated copies is illegal and copyright infringement may result to serious legal penalties. The Sonicwall Capture Labs Threats Research team has observed a malware pretending to be from a government agency and warns the victim that pirated software was found running in their system and wants the fine be paid in cryptocurrency.
Infection cycle:
This malware pretends to be an archive file and uses the following icon:
![]()
Upon execution it drops an archived file in the temp directory:
- %TEMP%\Win64.Trojan.GreenBug.zip
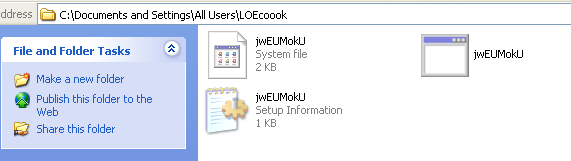
It then creates component files in the user profile directory under a randomly named folder such as the following:
- %USERPROFILE%\LOEcook\jwEUMokU.exe
- %USERPROFILE%\LOEcook\jwEUMokU.inf
- %USERPROFILE%\LOEcook\jwEUMokU
The malware adds the hidden attribute to these component files and folder.
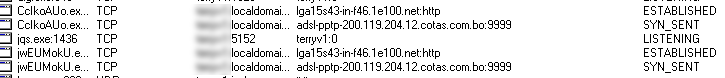
It then makes the following remote connections:
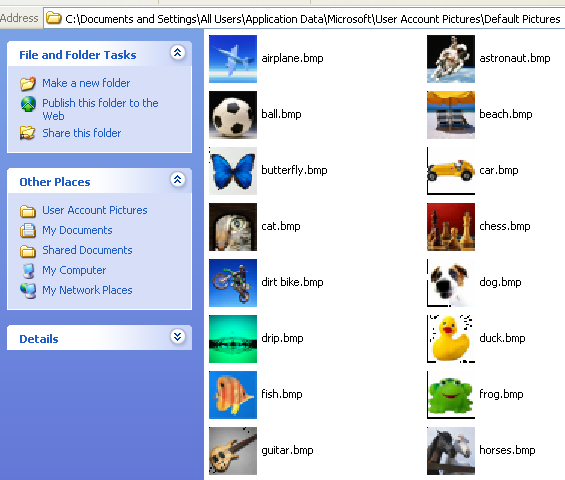
It overwrites files all photos, music and archive files in the victim’s machine with its own executable so every time one of these files is accessed a copy of the malware is actually executed. It keeps the original filename and icon for the previously overwritten files thus bmp files appear to still look like image files as seen in the screenshot below.
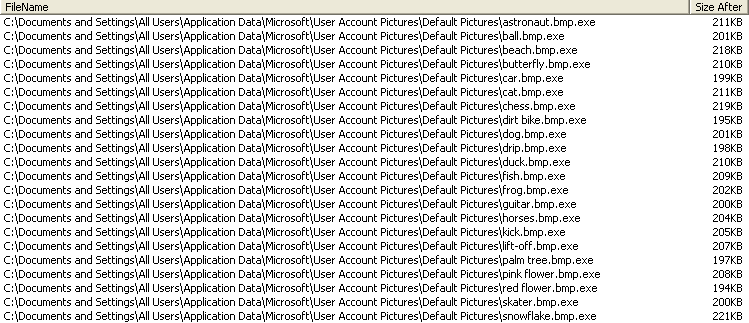
But tweaking the folder options and unhiding extensions for known file types will reveal that these files are in fact executable files.
Upon successful infection, it displays the following warning message from “National Security Bureau” and locks the screen of the victim machine until a fine is paid in bitcoins.
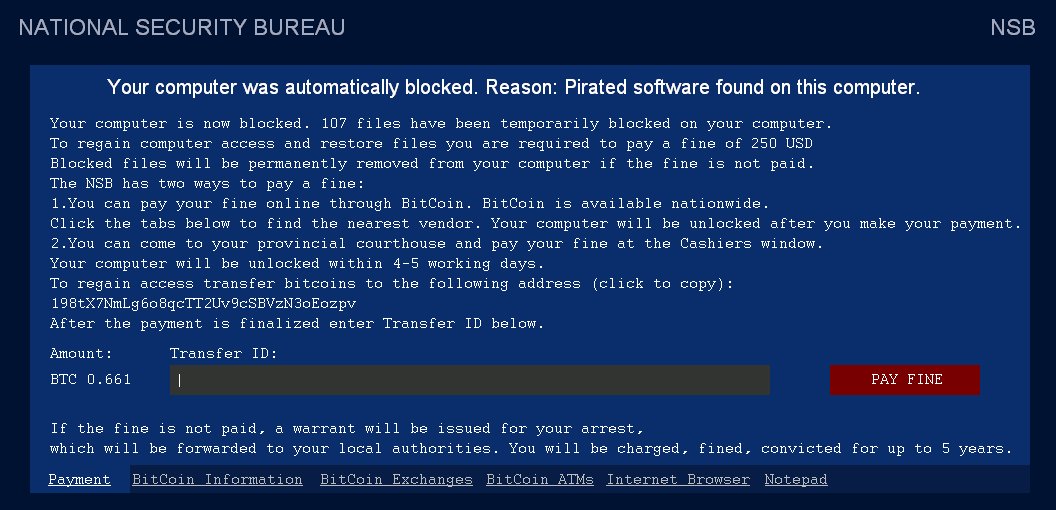
It also adds a run key in the registry to ensure that it executes the malware and locks the screen upon reboot.
- HKCU\Sofware\Microsoft\Windows\CurrentVersion\Run jwEUMokU “%USERPROFILE%\LOEcook\jwEUMokU.exe”
Quickly checking the bitcoin address 98tX7NmLg6o8qcTT2Uv9cSBVzN3oEozpv referenced on the warning message appears that this malware might not have been really successful.
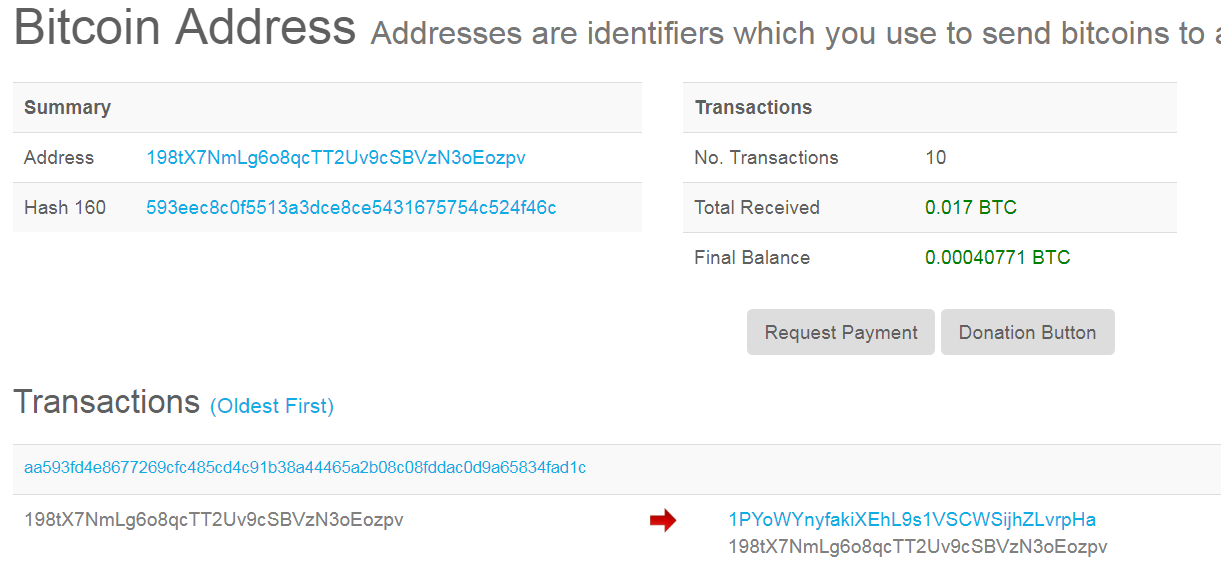
But following one of the outgoing transactions of this address we found an address that was known to be related to cryptolocker main chain. And thus we can conclude that this malware must be by the same malware author.
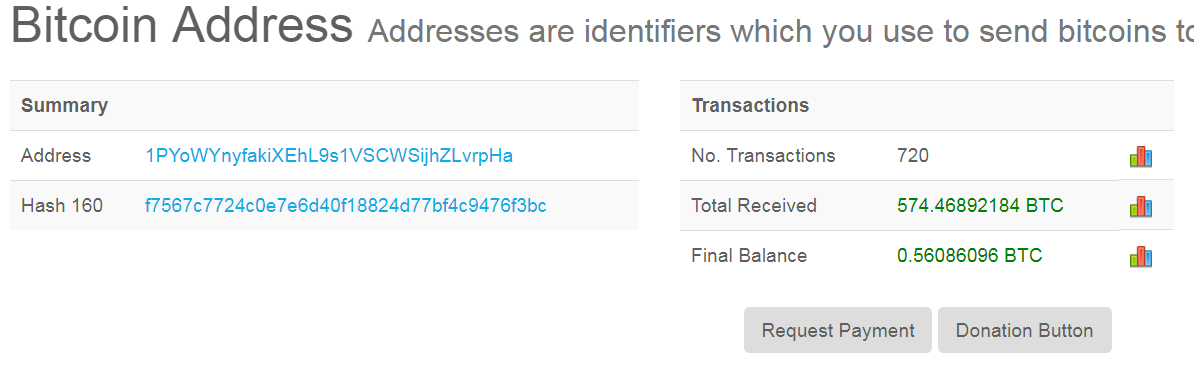
Malware authors, particularly ransomware operators, are known to generate multiple addresses and have been observed to execute several coordinated transactions in an attempt to further obfuscate the “paper trail” between two or more bitcoin addresses.
Sonicwall Capture Labs provides protection against this threat via the following signatures:
- GAV: Virlock.E_2 (Trojan)
- GAV: BackDoor.AAAB (Trojan)





