Malicious Android apps observed during Thanksgiving season of 2019
The shopping season during Thanksgiving is amplified by numerous deals during Black Friday and Cyber Monday. There are a lot of mobile apps that keep track of deals, provide discount coupons and provide the convenience of shopping from mobile devices and skipping long lines at shopping malls. Malware writers use this opportunity to spread malware under the guise of shopping/deals related apps.
SonicWall Threats Research Team keeps a vigilant eye on such apps during the shopping season. We observed a number of malicious Android apps in the past few weeks that use the shopping theme to trick users into downloading and installing these apps. Below are a few highlights from our findings
- Name: Amazon Shopping Hack
- Package: com.amazon.mShop.android.shopping.hack
- SHA: fa87b95eead4d43b2ca4b6d8c945db082b4886b395b3c3731dee9b7c19344bfa
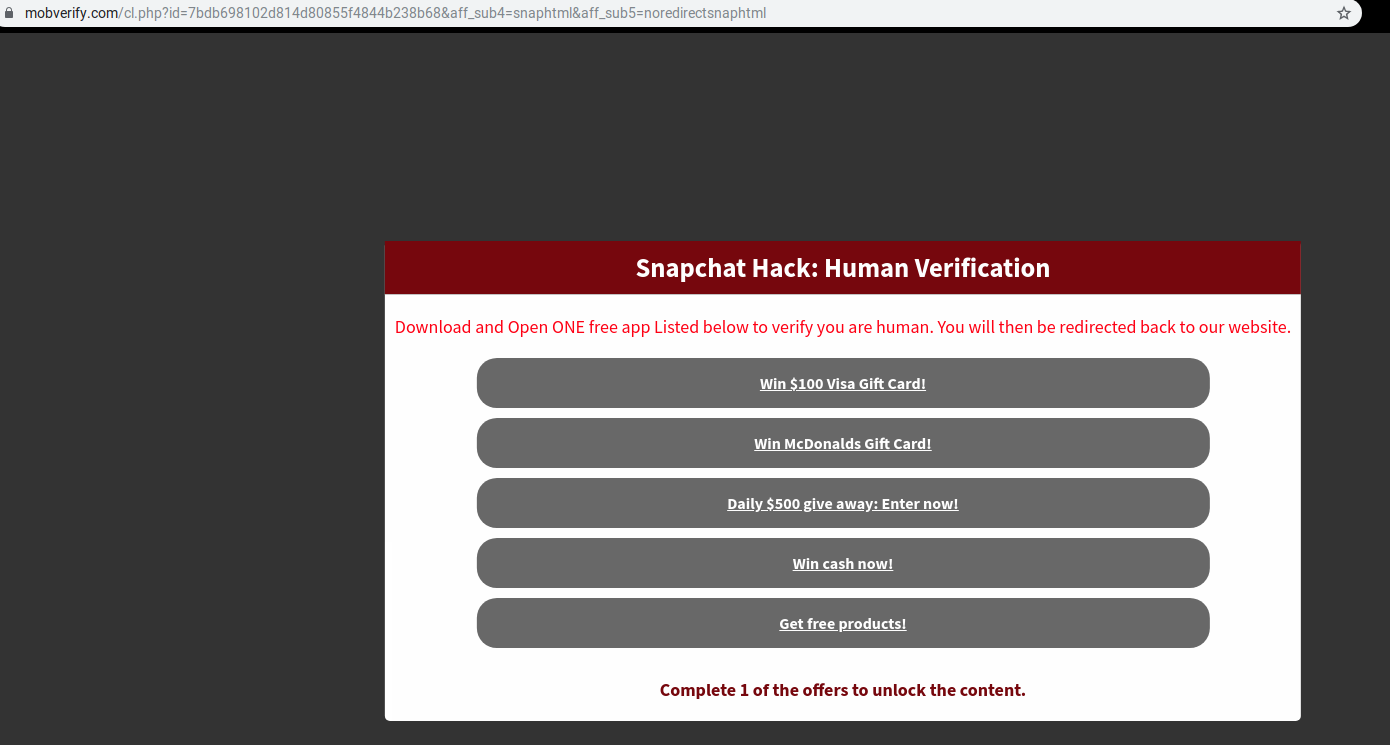
After execution this app shows a human verification page to continue using this app further. This essentially leads to survey related scams that aim towards extracting sensitive user related information such as email address, credit card details, address, etc.
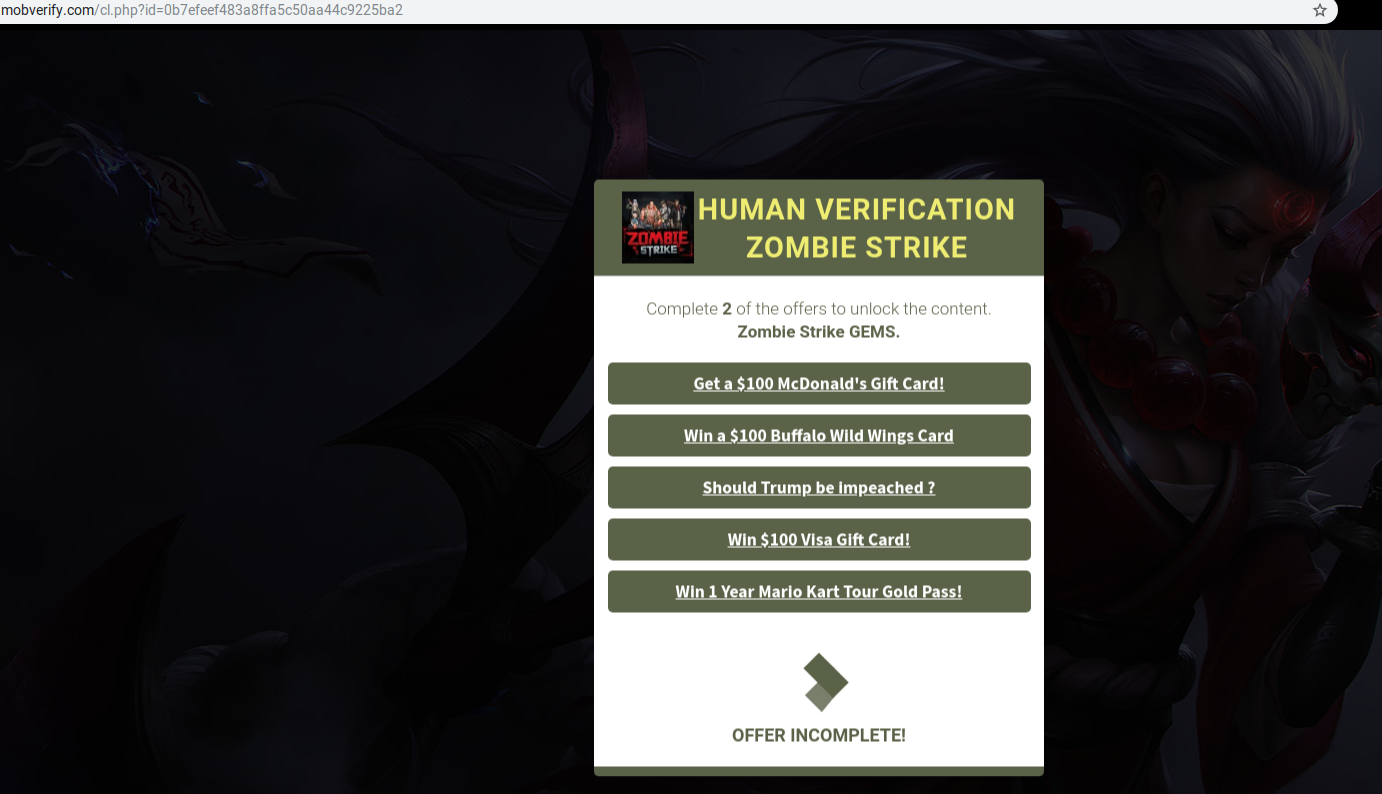
One of the domains contacted by this app during its execution is mobverify.com. A quick search about this domain revealed a number of other survey related pages:
This domain is associated with a number of malicious apps, survey scam links and malicious executables:
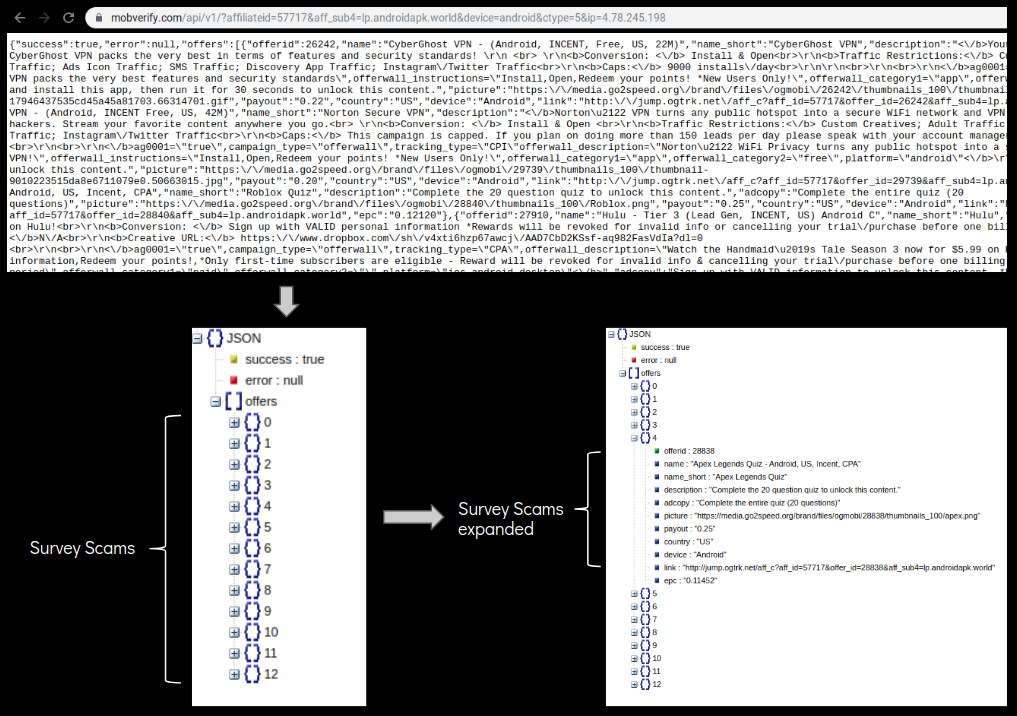
During analysis of this app, we observed a GET request to mobverify.com which downloads a json file containing a list of different survey scams:
- Name: 逛街早知道
- Package: com.shangchao.discount
- SHA: b8eae5573540392431c71dc4cbe0ca64db95ae494d8e0d8403f7041a16756f44
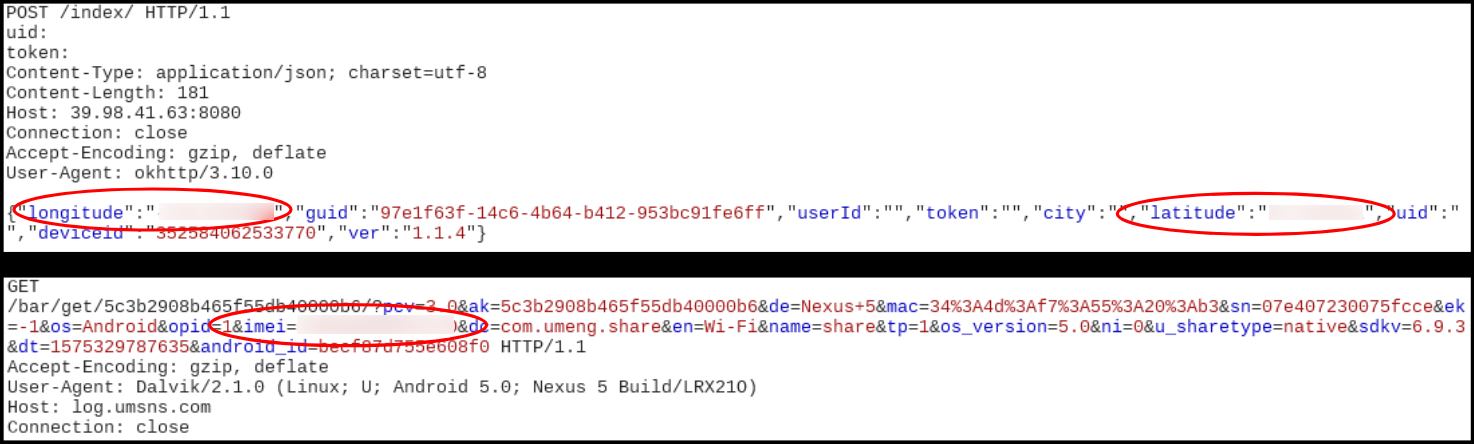
After execution this app shows coupons from different categories. In the background we saw this app communicate with malicious domains and transmit sensitive information from he infected device. In one instance we saw device location and IMEI details being sent to suspicious domains:
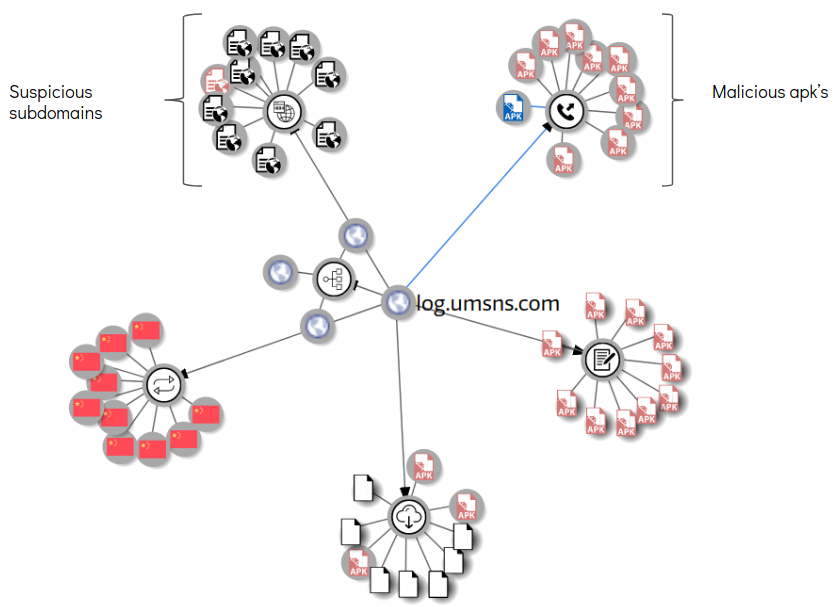
One of the domains that was communicated with is log.umsns.com which is connected with a number of malicious apk detections:
- Name: Daily coupons – hot shopping
- Package: cn.appfly.dailycoupon
- SHA: 1ebb118b35d1b9f906f1e78db9a0ea92ba45f86836f63141a48d0dbbb03844b3
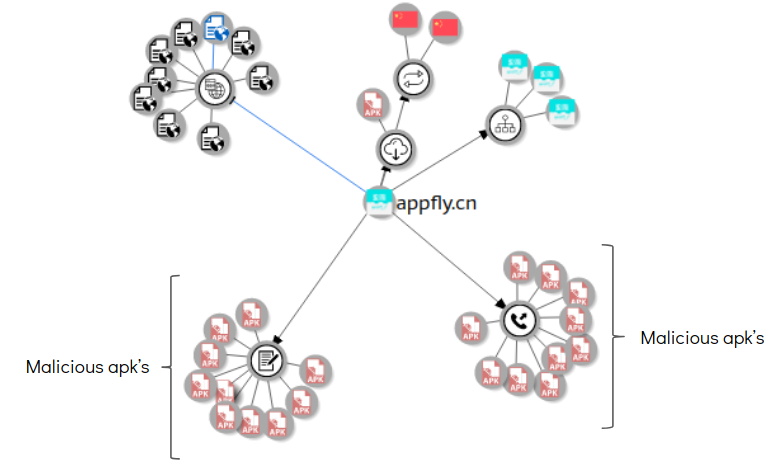
After execution this app appears to show coupons from different categories. In the background we saw this app communicate with a domain that has a number of malicious apps associated with it:
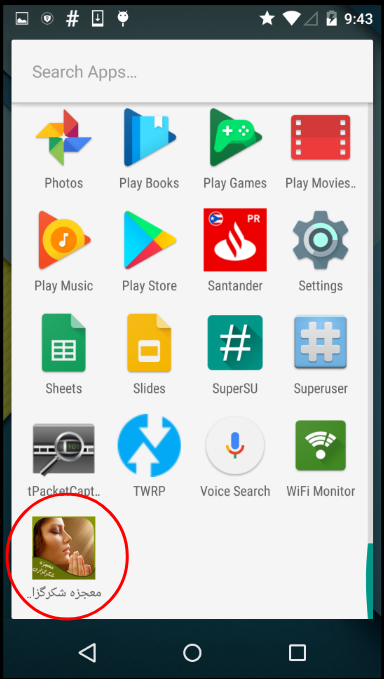
- Name: معجزه شکرگزاری
- Package: com.marjansb1.thanksgiving
- SHA: 45149b486cdb79c7bdce5eca95defb64f9b69f3f617d112e790863fbb228bd66
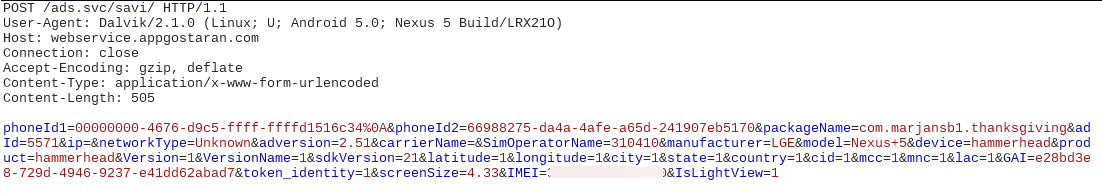
During the app execution we observed sensitive data being transmitted from the device to suspicious domains. Again IMEI data was seen transmitted to these domains along with other device related information:
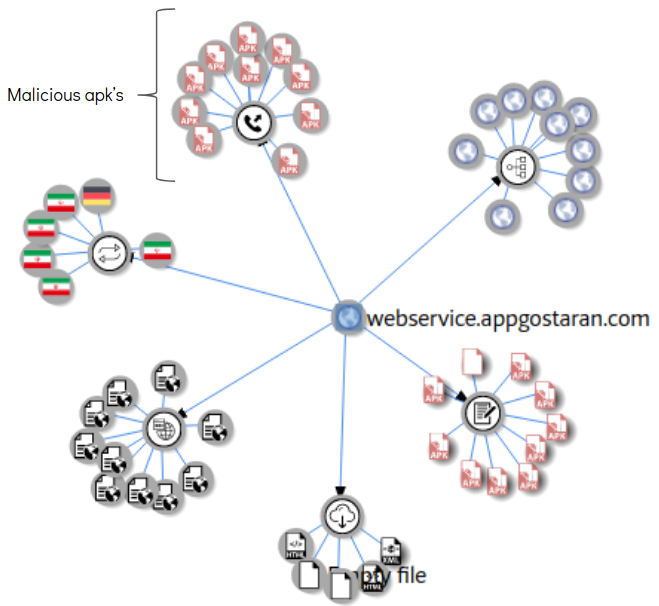
This app communicated with a domain webservice.appgostaran.com which is connected with a number of malicious apks:
SonicWall Capture Labs provides protection against these threats with the following signatures:
- AndroidOS.Verification.AM
- AndroidOS.Verification.BR